In a significant move to combat cybercrime, the U.S. Federal Bureau of Investigation (FBI) has announced that it has over 7,000 decryption keys associated with the LockBit ransomware operation. These keys will be used to assist victims in retrieving their data at no cost.
The FBI is actively reaching out to known LockBit victims and encouraging anyone who suspects they were a victim to visit their Internet Crime Complaint Center. This announcement was made by FBI Cyber Division Assistant Director Bryan Vorndran during his keynote address at the 2024 Boston Conference on Cyber Security (BCCS).

Potential victims can contact IC3 by visiting our LockBit Victim Reporting Form at lockbitvictims.ic3.gov.
LockBit, once a prolific ransomware gang, has been linked to over 2,400 attacks globally, with no less than 1,800 impacting entities in the U.S. Earlier this February, an international law enforcement operation dubbed Cronos, led by the U.K. National Crime Agency (NCA), dismantled its online infrastructure.
Last month, authorities identified a 31-year-old Russian national named Dmitry Yuryevich Khoroshev as the group’s administrator and developer, a claim LockBitSupp has since denied. Despite these actions, LockBit has continued to remain active under a new infrastructure, albeit operating nowhere at its previous levels.
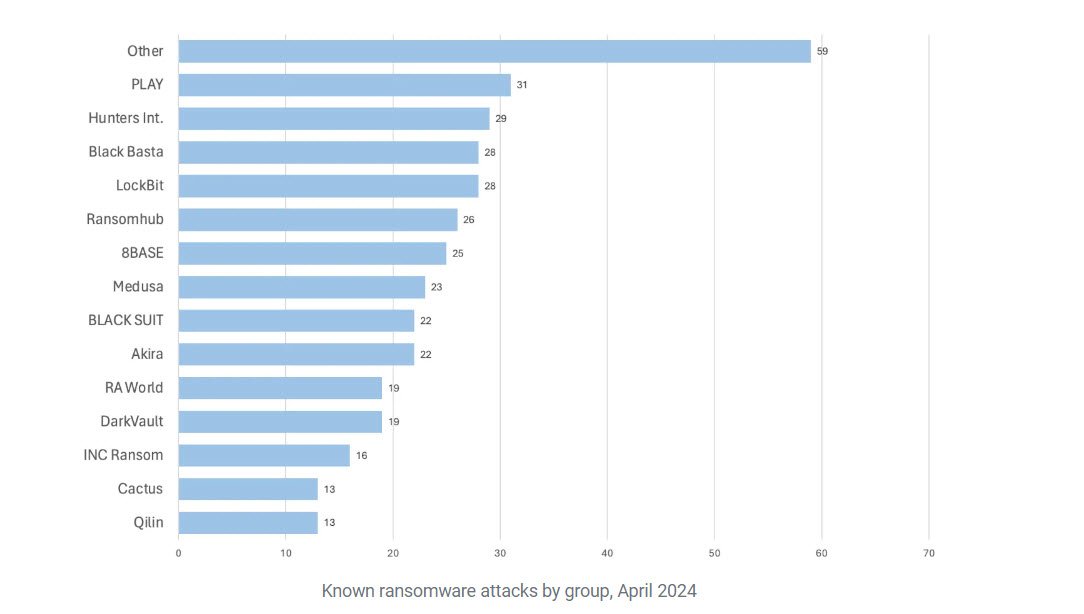
Statistics shared by Malwarebytes show that the ransomware family has been linked to 28 confirmed attacks in the month of April 2024, putting it behind Play, Hunters International, and Black Basta. Vorndran also emphasized that companies opting to pay to prevent the leak of data have no guarantee that the information is actually deleted by the attackers.
According to the Veeam Ransomware Trends Report 2024, organizations experiencing a ransomware attack can recover, on average, only 57% of the compromised data, leaving them vulnerable to substantial data loss and negative business impact.
The development coincides with the emergence of new players such as SenSayQ and CashRansomware (aka CashCrypt), as existing ransomware families like TargetCompany (aka Mallox and Water Gatpanapun) are consistently refining their tradecraft by leveraging a new Linux variant to target VMWare ESXi systems.
The attacks take advantage of vulnerable Microsoft SQL servers to gain initial access, a technique adopted by the group since its arrival in June 2021. It also determines if a targeted system is running in a VMWare ESXi environment and has administrative rights before proceeding further with the malicious routine.
The fight against ransomware is a global challenge that requires a concerted effort from all stakeholders. The FBI’s move to distribute decryption keys is a significant step in the right direction. However, it also underscores the need for organizations to implement robust security measures to protect their systems and data from such threats.




Pingback: The Importance of Cybersecurity Awareness Training in 2025 - Tech Hyme
Pingback: Indian Government Calls on Organizations to Adopt SIEM/SOAR Solutions - Tech Hyme