
Linux is a powerful and flexible operating system widely used for its stability, security, and efficiency in server environments. Mastering the Linux command line can significantly enhance productivity by allowing users to interact…
Read more
Efficient process management is crucial for optimizing system performance and ensuring smooth operations in any Linux environment, especially in distributions like Kali Linux used by security professionals and penetration testers. Understanding and mastering…
Read more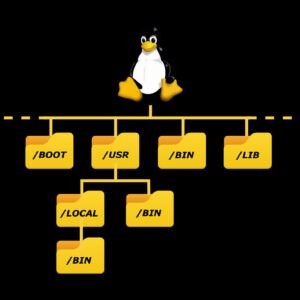
In the world of Linux, mastering file system commands is crucial for efficient navigation, management, and manipulation of files and directories. Whether you’re a seasoned Linux user or just starting out, understanding these…
Read more
Efficiently managing and compressing files is a crucial aspect of system administration and data management on Linux distributions like Debian. File compression not only reduces storage space but also makes it easier to…
Read more
In the realm of network security, the Secure Shell (SSH) protocol stands as a cornerstone for establishing encrypted communications between servers and clients. This protocol, based on the Transmission Control Protocol (TCP), ensures…
Read more
In the realm of cybersecurity, monitoring active network connections is essential for detecting and mitigating potential security threats. Kali Linux, a popular distribution among penetration testers and security professionals, provides powerful tools like…
Read more
Keeping accurate time and date settings on your Linux machine is crucial for various system tasks and overall functionality. Linux provides a powerful command called `timedatectl` that allows users to query and manipulate…
Read more
In many Linux environments, it’s common to grant sudo access to non-privileged users for performing administrative tasks. This practice ensures that certain actions, typically requiring root privileges, can be executed without granting full…
Read more
In the realm of Linux networking, the `ip` command has emerged as a versatile and powerful tool, replacing the aging `ifconfig` and `route` commands. Part of the `iproute2` package, the `ip` command offers…
Read more
Nmap, short for “Network Mapper,” stands as a powerful and versatile tool in the realm of network exploration. Developed by Gordon Lyon, this free and open-source network scanner has become a go-to solution…
Read more
The `w` command is a fundamental tool in Linux used to gather information about the users currently logged into a system and their ongoing activities. It provides a snapshot of user-related data, including…
Read more
The `ss` command in Linux is a powerful utility that provides detailed information about network socket connections. It is considered an advanced version of the older `netstat` command, offering more features and flexibility….
Read more
In the realm of Linux, determining whether your system is connected to the internet is a common task. Various tools and utilities are available to perform this check, and you can use either…
Read more
The whois utility is an essential tool for obtaining detailed information about domain registrations, including ownership details, contact information, registration and expiration dates, and more. In this article, we will guide you through…
Read more
File attributes in Linux play a crucial role in controlling the behavior and access permissions of files. The `chattr` command is a powerful tool that allows users to manipulate these attributes to enhance…
Read more