
Information Technology consists of all forms of technology used to create, store and exchange information in various forms, i.e. it incorporates all computerized and automated information handling including system design and analysis, conversion…
Read more
General purpose computers come in many sizes and capabilities. Traditionally, computers were classified by their size, processing speed, and cost. Based on these factors and generations, computers were classified as: ANALOG COMPUTERS DIGITAL…
Read more
The term computer generation refers to the development of both the hardware and software technologies. Each step of development in computer is regarded as a new generation of computers. Each generation of computers…
Read more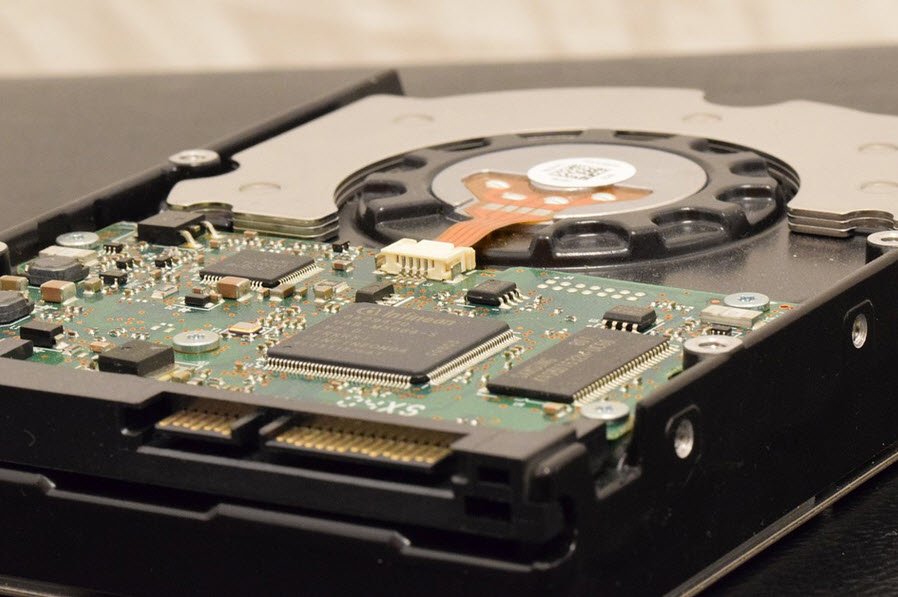
It is important to know the difference between secondary storage and a computer’s main memory. The primary (computer’s) memory or commonly known as random access memory (RAM) is the volatile memory and the…
Read more
The CCIE Certification is the highest level of achievement for network professionals, certifying an individual as an expert or master. Cisco Systems has since become an unrivaled worldwide leader in networking for the…
Read more
Hello Everyone! You can easily increase your productivity by using computer keyboard shortcuts which actually increase your focus in your work too. For example, to copy any text, you can select that text…
Read more
Inheritance is one of the key concept in the Object Oriented Programming language like C++, that enables you to organize classes in a hierarchical form. Just like a child inherits the characteristics of…
Read more
Polymorphism is a very powerful concept that allows the design of amazingly flexible applications. Polymorphism can be defined as one interface multiple methods which means that one interface can be used to perform…
Read more
Like function overloading, C++ also support a powerful concept called operator overloading. C++ contains a rich set of operators such as +,-,*,>>,<,++ etc which work on built-in types such as int, float, char…
Read more
If you ever see a message like this upon opening a new shell – “zsh: corrupt history file /root/.zsh_history“. You can easily fix your history file by extracting only the valid strings. The…
Read more
Most people ask themselves whether they can be tracked over the Internet by having their MAC Address or IP address detected by others. It’s true that IP addresses are no longer secret. It’s…
Read more


