
In the realm of network security, the Secure Shell (SSH) protocol stands as a cornerstone for establishing encrypted communications between servers and clients. This protocol, based on the Transmission Control Protocol (TCP), ensures secure data transmission over potentially insecure networks.
In this article, we will explore into the intricacies of SSH, its key features, implementation, and best practices for ensuring a secure connection.
What is SSH?
The Secure Shell (SSH) protocol is a network protocol that enables secure, encrypted communication between a server and a client. It replaces the inherently insecure Telnet and FTP protocols with a robust encryption mechanism, ensuring confidentiality and integrity of data transmission.
1. Public-Private Key Authentication
One of the key features of SSH is its support for public-private key pair authentication. Users generate a key pair consisting of a public key, which is stored on systems requiring secure connections, and a private key, which is securely kept by the user.
The server verifies the public key against an authorized list of keys to grant access without requiring a password.
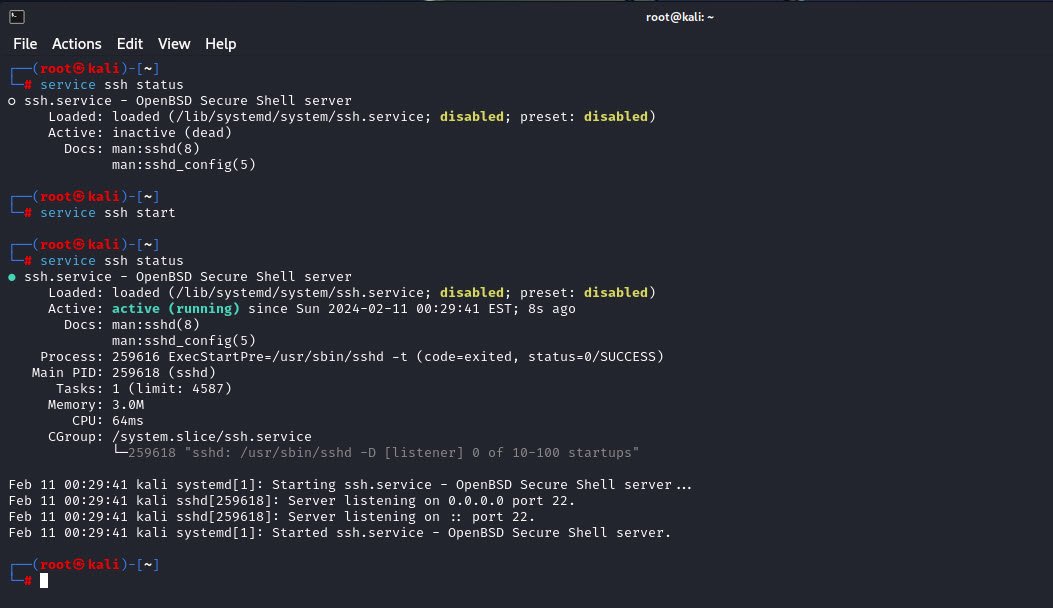
2. SSH Service Management
Managing the SSH service involves starting, stopping, and checking the status of the SSH daemon. The default SSH service listens on port 22, but it can be customized to use a different port for added security.
Commands such as `service ssh start`, `service ssh stop`, and `service ssh status` are used to control the SSH service.
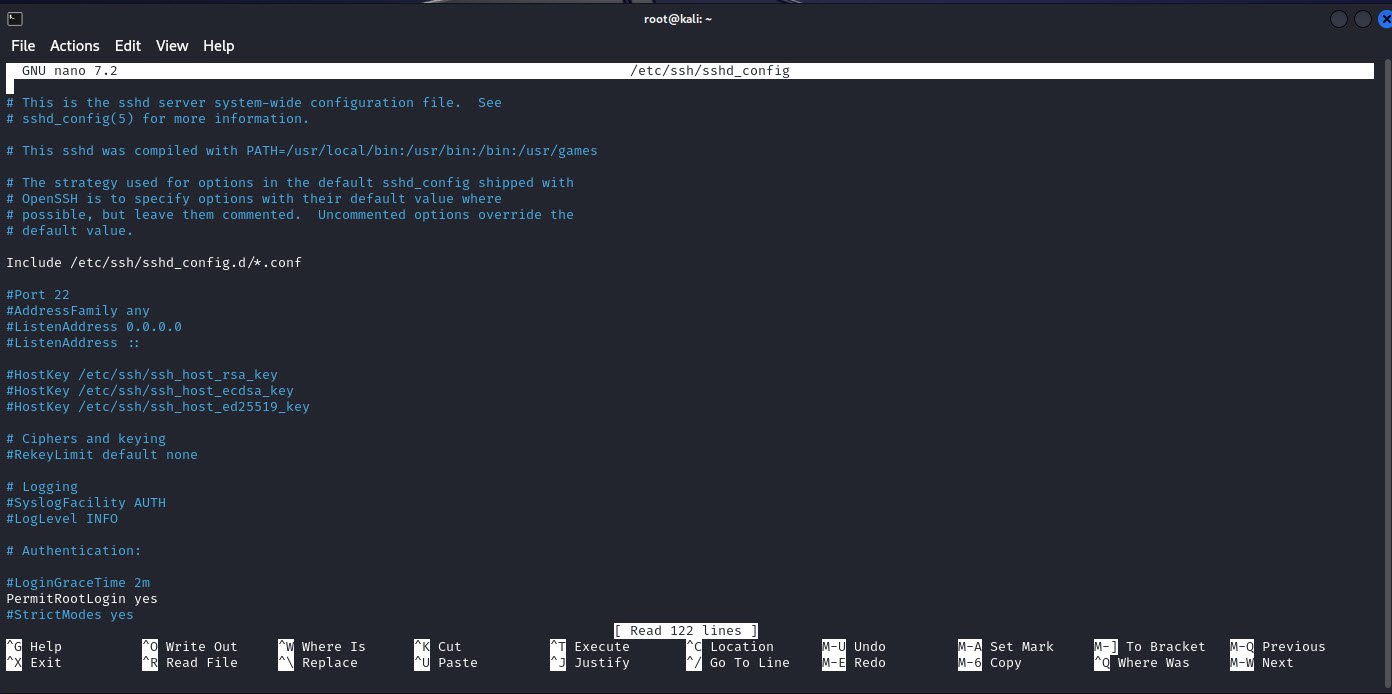
3. Secure Configuration
To enhance security, SSH configurations can be adjusted to allow or disallow certain types of access. For example, enabling root remote login into SSH should be done cautiously, as it introduces potential security risks.
This can be achieved by modifying the `sshd_config` file and restarting the SSH server.
4. SSH Connection Management
Establishing an SSH connection to a remote server involves using the `ssh` command followed by the username and IP address of the target server.
Moreover, if the SSH service on the server is running on a custom port, the port number can be specified using the `-p` option.
5. Key Management
Regularly updating and managing SSH keys is essential for maintaining a secure connection.
Users can generate new SSH keys using commands such as `dpkg-reconfigure openssh-server`, ensuring cryptographic strength and minimizing the risk of compromise.
Conclusion
The Secure Shell (SSH) protocol plays a vital role in securing network communications by providing encrypted connections between servers and clients. By understanding the principles of SSH, implementing best practices for key management, and securely configuring SSH services, users can leverage this protocol to establish secure and reliable communication channels.
As cyber threats continue to evolve, maintaining vigilance and adherence to SSH security practices is crucial for safeguarding sensitive data and maintaining the integrity of network communications.
You may also like:- A Comprehensive Guide to File System Commands in Linux
- Essential File Compression Commands in Linux
- Monitoring Active Connections in Kali Linux Using Netstat
- Manage Time and Date in Linux with timedatectl
- How to Add a User to Sudoers on Ubuntu
- 25 Popular Linux IP Command Examples
- Top 11 Nmap Commands for Remote Host Scanning
- 9 Useful w Command Examples in Linux
- 25 Useful Linux SS Command Examples to Monitor Network Connections
- 9 Essential Linux Commands and Shell Scripts to Check Internet Connectivity








This Post Has One Comment