
Virtualization is an entry-level technology for cloud computing and a very important technology in cloud computing. Also Read: HCIA Security – Practice Test Questions With Answers This exam (HCIA – Cloud Computing) introduces…
Read more
This course is designed for networking professionals with beginner-intermediate knowledge of the Juniper Networks Junos OS for SRX Series devices, this written exam verifies the candidate’s understanding of security technologies and related platform…
Read more
CompTIA offers everything you need to get you ready for your IT Fundamentals certification exam. CompTIA IT Fundamentals (ITF+) is an introduction to basic IT knowledge and skills that helps professionals or students…
Read more
HCIA – Security certification covers the basic knowledge and skills in enterprise network security. HCIA- Security certificate holders are able to perform basic O & M and management operations related to enterprise network…
Read more
The Automation and DevOps certification track enables you to demonstrate competency in common scripting languages and tools for automating device and network functions. Also Read: Juniper JN0-211 – Multiple Choice Questions & Answers…
Read more
JN0-211 exam is the current version for Cloud, Associate (JNCIA-Cloud) certification exam. We have updated JNCIA-Cloud JN0-211 practice exam tests online to help you prepare for the Cloud Associate certification exam well. The…
Read more
There are certain commandments that an ethical hacker lives by. Here are 10 of the main ones: You must set goals If you have planned to evaluate the security of an online system…
Read more
Databases are usually the main targets of any attack, specifically for the information that they store in their database. According to OWASP Standard, the SQL injection vulnerability is one of the ten most…
Read more
There are different ways that a hacker can launch an attack on a system. Systems have become even more vulnerable in recent times due to social media, cloud computing and virtualization. The more…
Read more
Although assembly language makes it unnecessary to write binary machine language instructions, it is not without difficulties. Assembly language is primarily a direct substitute for machine language, and like machine language, it requires…
Read more
When you compile any source code, an object file is generated of that program and with the help of linker, that object files gets converted to a binary file which, only the machine…
Read more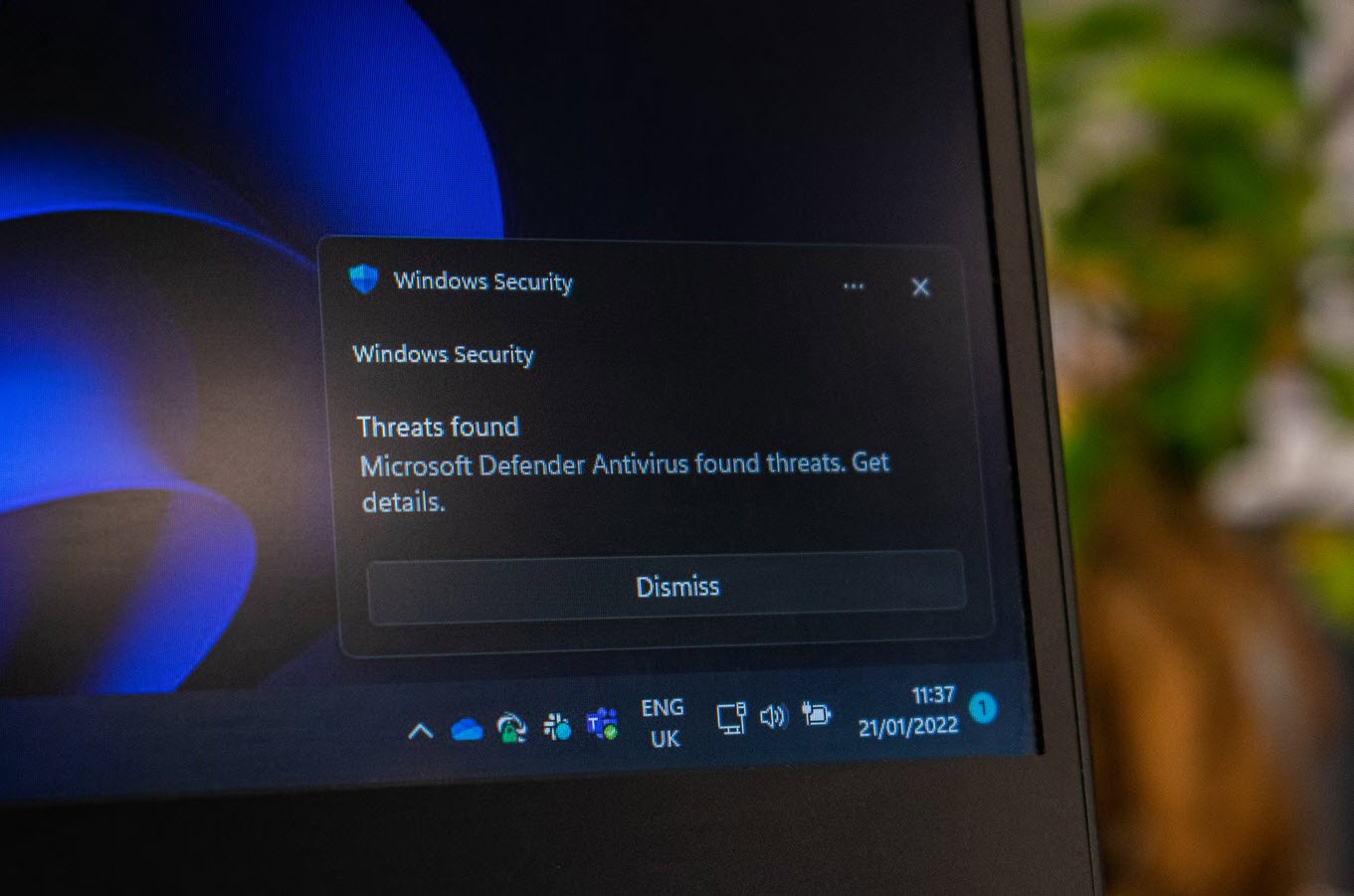
Microsoft Defender Antivirus (a.k.a Windows Defender) is a built-in free anti-malware software included with Windows 10/11 that protects the computer from viruses, malware, spywares and Trojans. In addition to antivirus and anti-malware protection,…
Read more
Windows 11 is the latest major release of Microsoft’s Windows NT operating system, and is the successor to Windows 10. Citing security considerations, the system requirements for Windows 11 were increased over Windows…
Read more
Kali Linux operating system can be considered the number one security operating system of today. This is the operating system that the programming world usually likes to use to perform penetration testing or…
Read more
Ethical hackers are usually security professional or network penetration testers who use their hacking skills for defensive and protective purposes. They do their work with the permission of the organization. The work is…
Read more