
Linux systems grant significant power and privileges to the root user, making it a pivotal account in managing the server. However, this immense authority also poses a substantial security risk. If unauthorized users gain access to the root user, they can wreak havoc on the server and compromise sensitive data.
Therefore, it’s essential to disable root login to fortify the server’s security.
The Significance of Disabling Root Login
The root user possesses unparalleled permissions within a Linux system. It can execute any action, modify critical system settings, and access sensitive data. Given this supreme authority, the root user becomes a prime target for potential hackers. Disabling direct root login is a fundamental security measure aimed at minimizing this risk.
How to Disable Root Login
To disable root login and enhance server security, follow these simple steps:
1. Access the SSH Configuration File:
Open the main SSH configuration file in a text editor. Use the following command:
sudo nano /etc/ssh/sshd_configThis command will open the SSH configuration file, enabling you to make necessary modifications.
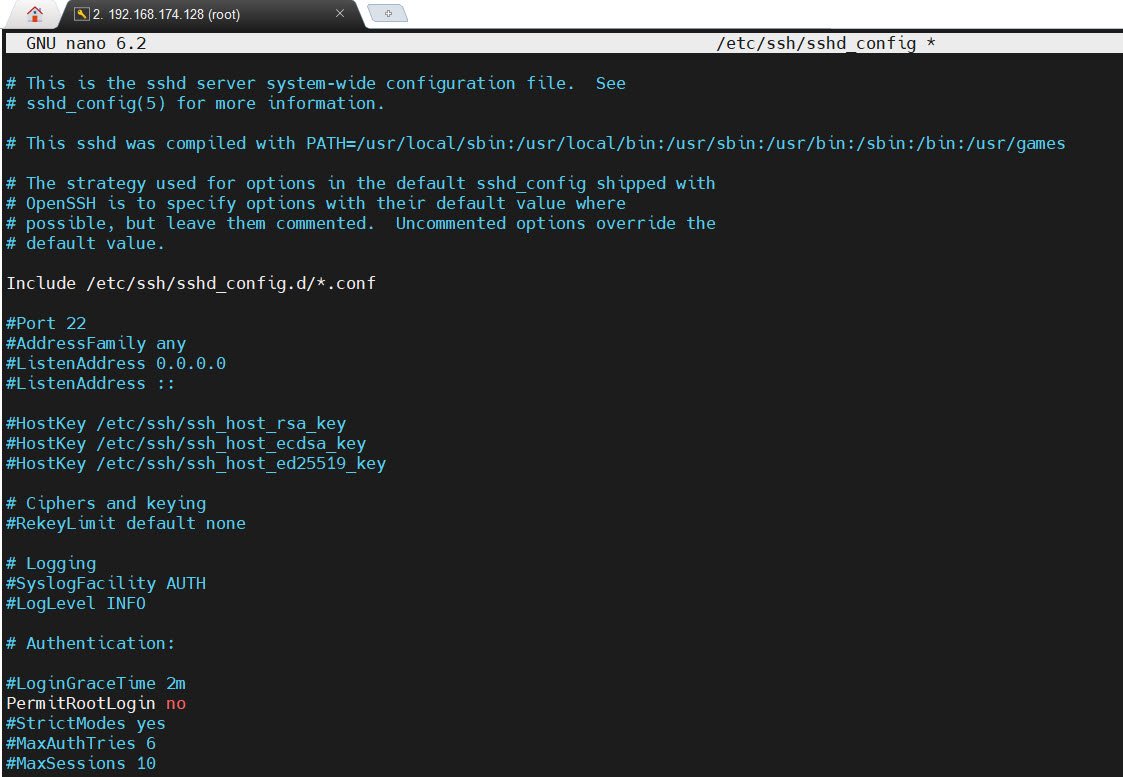
2. Locate PermitRootLogin Directive:
Within the configuration file, locate the `PermitRootLogin` directive. You can do this by pressing `CTRL+W` and typing `PermitRootLogin`. Hit the `Enter` key to proceed.
3. Update the Directive:
If the directive is set to `PermitRootLogin yes`, change it to `PermitRootLogin no`. This modification will disallow the root user from logging in directly to the server.
4. Save the Changes:
After making the necessary change, save the configuration file. Press `CTRL+X`, then `Y` to confirm the changes, and finally, press `Enter` to exit the editor.
5. Restart the Service:
At the end, restart the SSH service by typing “service ssh restart“.
Conclusion
Disabling root login is a fundamental security practice in Linux systems, aimed at mitigating potential security risks associated with unauthorized access to the root account. By restricting direct root login, server administrators can significantly enhance the server’s security posture, ensuring the safety and integrity of critical data and system resources.
Implement this precautionary measure as part of an overall security strategy to fortify your server against potential threats.
You may also like:- How To Install Python 2.7.18 From The Source
- How To Parse SSH Authentication Logs with Logstash
- How To Easily Crack Wi-Fi Password
- 6 Most Useful Windows Command Prompt Commands
- Ripgrep – Searching for Specific File Types and Beyond
- Insert and Create Data in Elasticsearch
- Manage Time and Date in Linux with timedatectl
- How to Set Network Adapter Priority on Windows 11
- How to Add a User to Sudoers on Ubuntu
- 25 Popular Linux IP Command Examples








