Network security audits are crucial for identifying vulnerabilities and strengthening cybersecurity defenses. Kali Linux, a powerful penetration testing distribution, provides a wide range of tools to conduct thorough security audits.
In this article, we will discuss how to perform a network security audit using Kali Linux in simple steps.
What is a Network Security Audit?
A network security audit is a systematic evaluation of an organization’s IT infrastructure to identify security weaknesses. The goal is to detect vulnerabilities before malicious attackers exploit them. Security audits involve scanning for open ports, checking for outdated software, identifying misconfigurations, and testing network defenses against attacks.
Why Use Kali Linux for Security Audits?
Kali Linux is a specialized Linux distribution designed for penetration testing and security auditing. It comes with pre-installed tools for ethical hacking, making it a preferred choice for cybersecurity professionals. Some of the popular tools in Kali Linux include Nmap, Wireshark, Metasploit, Nikto, and Aircrack-ng.
Steps to Perform a Network Security Audit Using Kali Linux
1. Setting Up Kali Linux
Before starting the audit, ensure that Kali Linux is installed on your system. You can run Kali Linux in different ways:
- As a standalone OS (installed directly on hardware)
- In a virtual machine (using VirtualBox or VMware)
- As a live USB (bootable USB drive)
Ensure that you have the latest updates by running the following command:
sudo apt update && sudo apt upgrade -y2. Identifying Network Information
Before scanning the network, gather information about the target network. Use the following command to check your IP address and network details:
ip a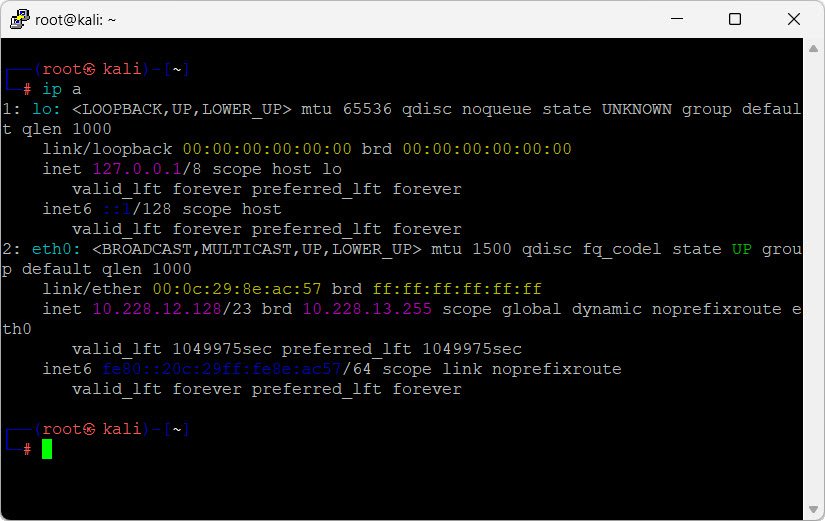
To identify active devices on the network, use the netdiscover tool:
sudo netdiscover -r 192.168.1.0/24This will list all active hosts on the network.
3. Scanning for Open Ports and Services
Open ports can be potential entry points for attackers. Use Nmap to scan for open ports and running services:
nmap -sV -A 192.168.1.1/24Explanation:
- -sV – Detects service versions
- -A – Enables OS detection, version detection, script scanning, and traceroute
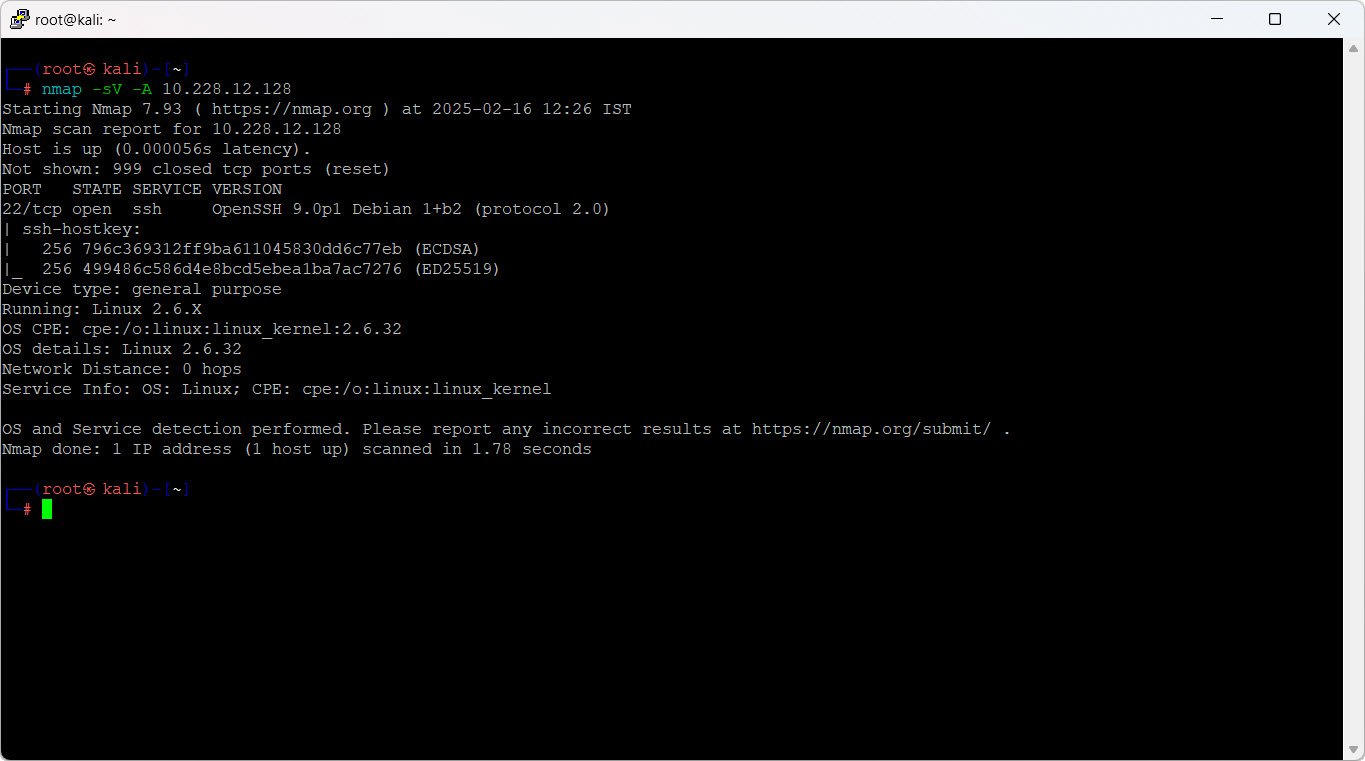
You can also perform a more aggressive scan using:
nmap -p- -T4 -A -v 192.168.1.1This will scan all 65,535 ports on the target.
4. Detecting Vulnerabilities
Once you identify active devices and open ports, check for vulnerabilities using Nikto and Metasploit.
Using Nikto for Web Server Scanning
Nikto helps identify security issues in web servers:
sudo nikto -h http://192.168.1.100This scans for outdated software, misconfigurations, and known vulnerabilities.
Using Metasploit for Deeper Analysis
Metasploit is a powerful tool for identifying vulnerabilities:
sudo msfconsole
use auxiliary/scanner/ssh/ssh_version
set RHOSTS 192.168.1.100
runThis will check for SSH version vulnerabilities.
5. Sniffing Network Traffic
Packet sniffing allows security analysts to monitor network traffic for suspicious activities.
Using Wireshark
Wireshark is a popular network analyzer:
- Open Wireshark in Kali Linux.
- Select the network interface (e.g., wlan0 or eth0).
- Start capturing packets.
- Analyze packets for unusual behavior.
Alternatively, use tcpdump in the terminal:
sudo tcpdump -i eth0 -n -c 100This captures 100 packets on the eth0 interface.
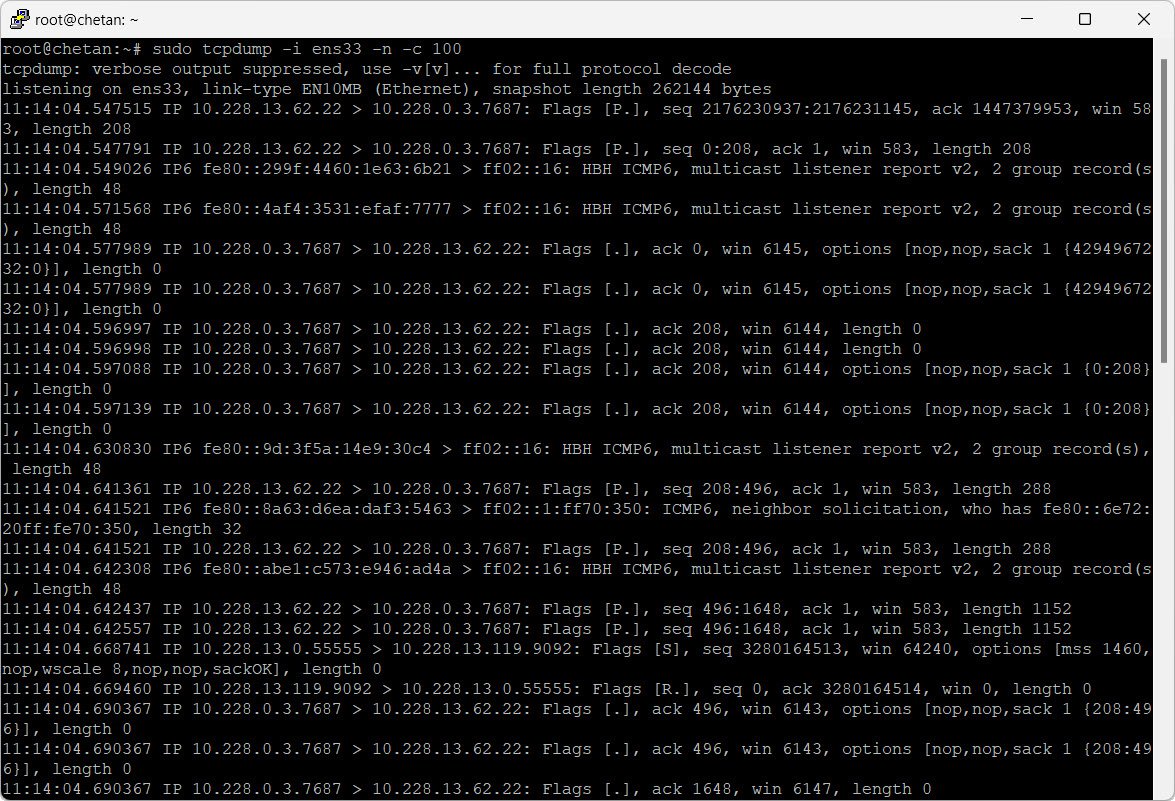
6. Testing Wireless Network Security
If auditing a wireless network, tools like Aircrack-ng can be used to check Wi-Fi security.
Put the wireless adapter in monitor mode:
sudo airmon-ng start wlan0Scan for available Wi-Fi networks:
sudo airodump-ng wlan0monCapture packets and attempt to crack the Wi-Fi password (only with permission).
7. Checking for Weak Passwords
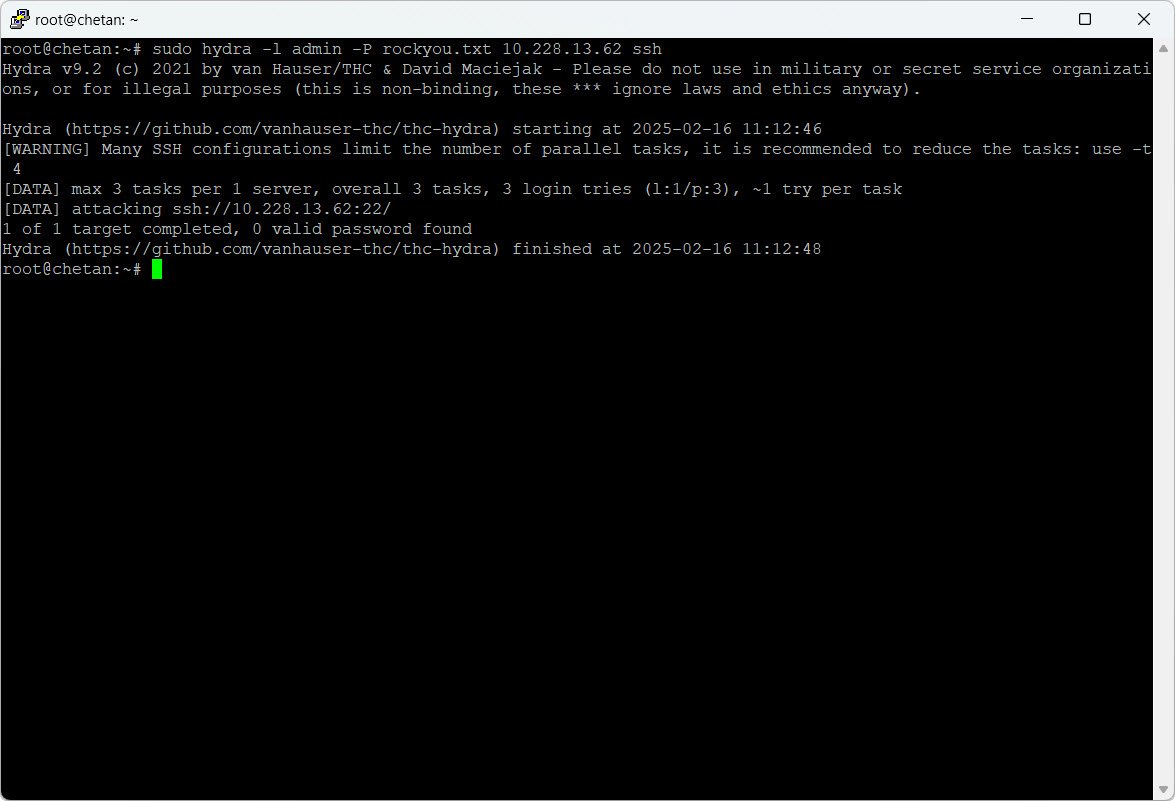
Use Hydra to test for weak login credentials on network services:
sudo hydra -l admin -P rockyou.txt 192.168.1.100 sshThis attempts SSH login using the username admin and password list rockyou.txt.
8. Generating Security Audit Reports
After completing the network audit, generate a report detailing the findings.
- Document open ports, vulnerabilities, and misconfigurations.
- Provide recommendations for securing the network.
- Use tools like Faraday for report generation in Kali Linux.
Conclusion
Performing a network security audit using Kali Linux is an effective way to identify vulnerabilities and strengthen cybersecurity defenses. By following the steps outlined above, IT professionals can proactively secure their networks against potential threats.
Regular audits help in maintaining a secure and resilient IT infrastructure.




Pingback: The Best YouTube Channels to Learn Kali Linux in 2025 - Tech Hyme
Pingback: Top 28 Windows Firewall Management Commands You Need To Know - Tech Hyme