
Networking is a vast and intricate field, filled with numerous protocols, technologies, and terminologies. Understanding the essential acronyms is crucial for anyone involved in the field. Here is a comprehensive list of the…
Read more
Kali Linux is a powerful platform for cybersecurity professionals and enthusiasts. It comes packed with tools designed to identify and analyze vulnerabilities in systems. Here’s a list of 19 essential tools for vulnerability…
Read more
Kali Linux is a specialized Linux distribution designed for security professionals and enthusiasts. It is a powerful operating system that comes preloaded with a vast array of tools for various aspects of cybersecurity….
Read more
Tracking the right Key Performance Indicators (KPIs) in your SEO efforts is crucial to understanding how well your strategies are performing and identifying areas for improvement. Here are some essential SEO KPIs that…
Read more
Driving traffic to your blog or website is crucial for success. Create high-quality, engaging content that provides value to your readers. Well-researched and well-written articles attract more visitors. Here are some quick and…
Read more
CSS libraries are essential tools that can help developers build better, faster, and more attractive web projects. With so many libraries available, it can be challenging to know where to start. In this…
Read more
Effective SEO is essential for driving traffic, enhancing online visibility, and increasing conversions. To gauge the success of your SEO efforts, it’s crucial to monitor and measure key metrics regularly. Here are the…
Read more
Finding the right niche can make a big difference in your SEO business. Whether you’re an agency, freelancer, affiliate marketer, blogger, or running an eCommerce site, choosing a niche that suits your strengths…
Read more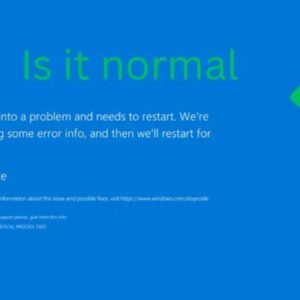
If you’re experiencing a Blue Screen of Death (BSOD) issue related to CrowdStrike, follow these steps to resolve it: Steps to Fix the Issue 1. Boot into Safe Mode or Windows Recovery Environment:…
Read more
A massive global outage has hit Microsoft services, causing widespread disruptions. People are unable to access their laptops, and many major organizations are affected. Almost all Indigo flights are delayed as they have…
Read more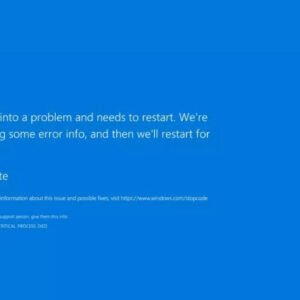
Windows users worldwide are experiencing the dreaded Blue Screen of Death (BSOD) error, causing their systems to suddenly shut down or restart. Microsoft has identified the issue as a recent CrowdStrike update gone…
Read more
Structured Query Language (SQL) is a standard language for managing and manipulating databases. This guide will walk you through some common SQL operations using practical examples. 1. Selecting Data from a Table To…
Read more
Addressing software vulnerabilities is a critical task for ensuring the security and reliability of applications. However, unless the origin of the vulnerability is explicitly identified, any patch may only cover up a problem…
Read more
In the realm of cybersecurity, the ability to monitor, detect, and respond to incidents is critical. Security Information and Event Management (SIEM) systems are central to this effort, offering real-time analysis of security…
Read more
In the rapidly evolving landscape of technology, cybersecurity has emerged as one of the most critical fields. With cyber threats becoming increasingly sophisticated, the need for comprehensive knowledge and understanding of cybersecurity principles…
Read more