Kali Linux is a powerful penetration testing and security auditing operating system, but like any other Linux distribution, it requires additional security measures to make it more resilient against attacks. Since Kali is often used in ethical hacking and cybersecurity, it can be a prime target for attackers if not properly secured.
In this guide, we will walk through the best practices to harden Kali Linux for maximum security.
- Keep Your System Updated
- Create a Non-Root User
- Enable a Firewall
- Disable Unnecessary Services
- Secure SSH Access
- Use AppArmor or SELinux
- Secure the Boot Process
- Use Full Disk Encryption (LUKS)
- Enable Automatic Log Monitoring
- Disable USB Ports (Optional)
- Enable Audit Logging
- Secure Browsing and Network Connections
1. Keep Your System Updated
Regular updates are essential to keep Kali Linux secure. Developers constantly patch vulnerabilities, so keeping your system updated reduces the risk of exploitation.
How to update Kali Linux:
sudo apt update && sudo apt full-upgrade -yEnable automatic updates by adding the following to /etc/apt/apt.conf.d/20auto-upgrades:
APT::Periodic::Update-Package-Lists "1";
APT::Periodic::Unattended-Upgrade "1";2. Create a Non-Root User
By default, Kali Linux uses a non-root user for security reasons. If you’re using an older version or want to create an additional secure user, do the following:
sudo adduser username
sudo usermod -aG sudo username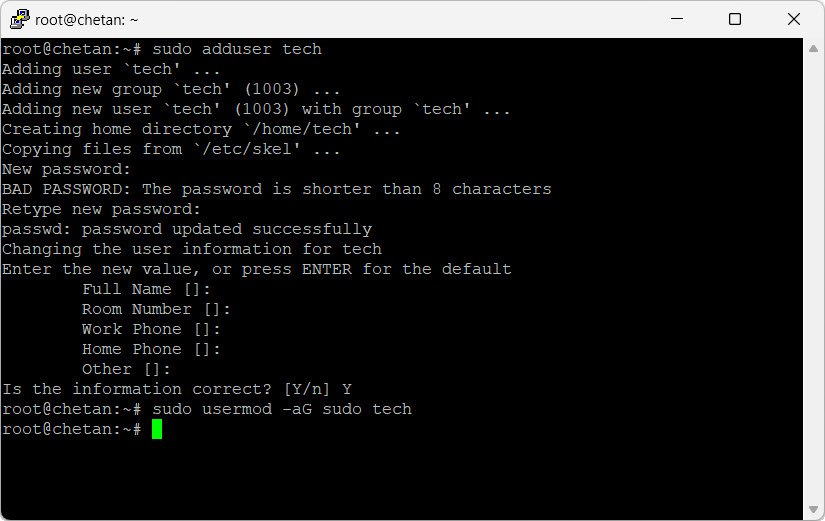
Then, disable the root account login:
sudo passwd -l root3. Enable a Firewall
Kali Linux comes with UFW (Uncomplicated Firewall), which is a user-friendly interface for managing firewall rules.
Enable and configure UFW:
sudo apt install ufw -y
sudo ufw enable
sudo ufw default deny incoming
sudo ufw default allow outgoing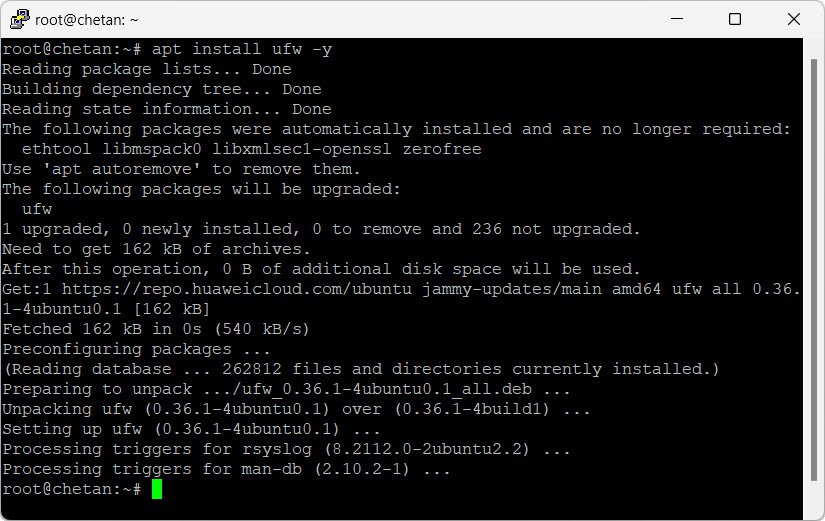
To allow SSH connections:
sudo ufw allow 22/tcpCheck firewall status:
sudo ufw status verbose4. Disable Unnecessary Services
Check running services:
sudo systemctl list-units --type=service --state=running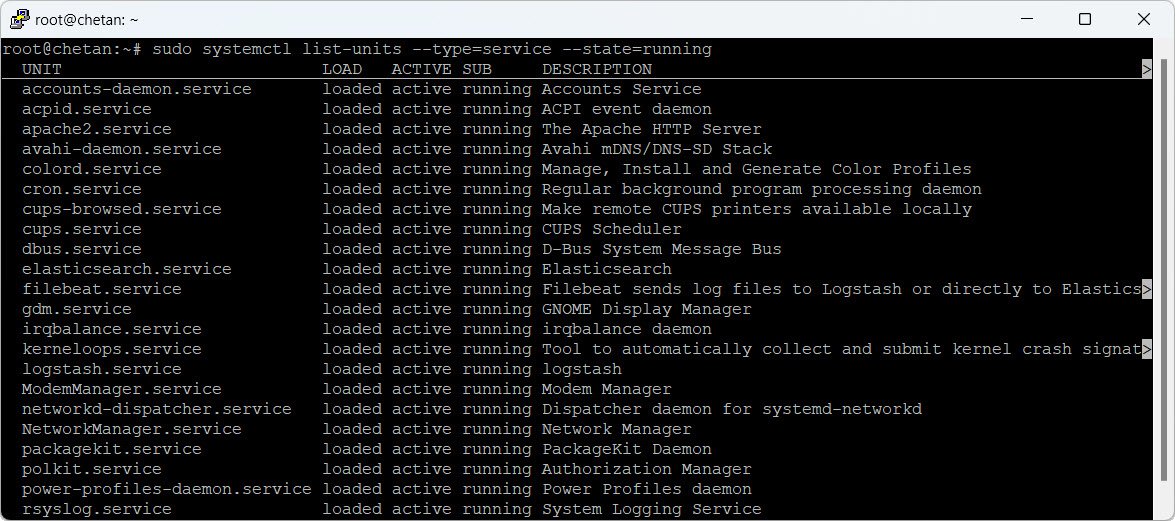
Disable unwanted services:
sudo systemctl disable service-name
sudo systemctl stop service-name5. Secure SSH Access
If you use SSH, follow these steps to harden it:
Change the default SSH port (e.g., port 2222 instead of 22):
sudo nano /etc/ssh/sshd_configFind the line #Port 22 and change it to:
Port 2222Restart SSH:
sudo systemctl restart sshDisable root login:
PermitRootLogin noAllow only specific users:
AllowUsers your_username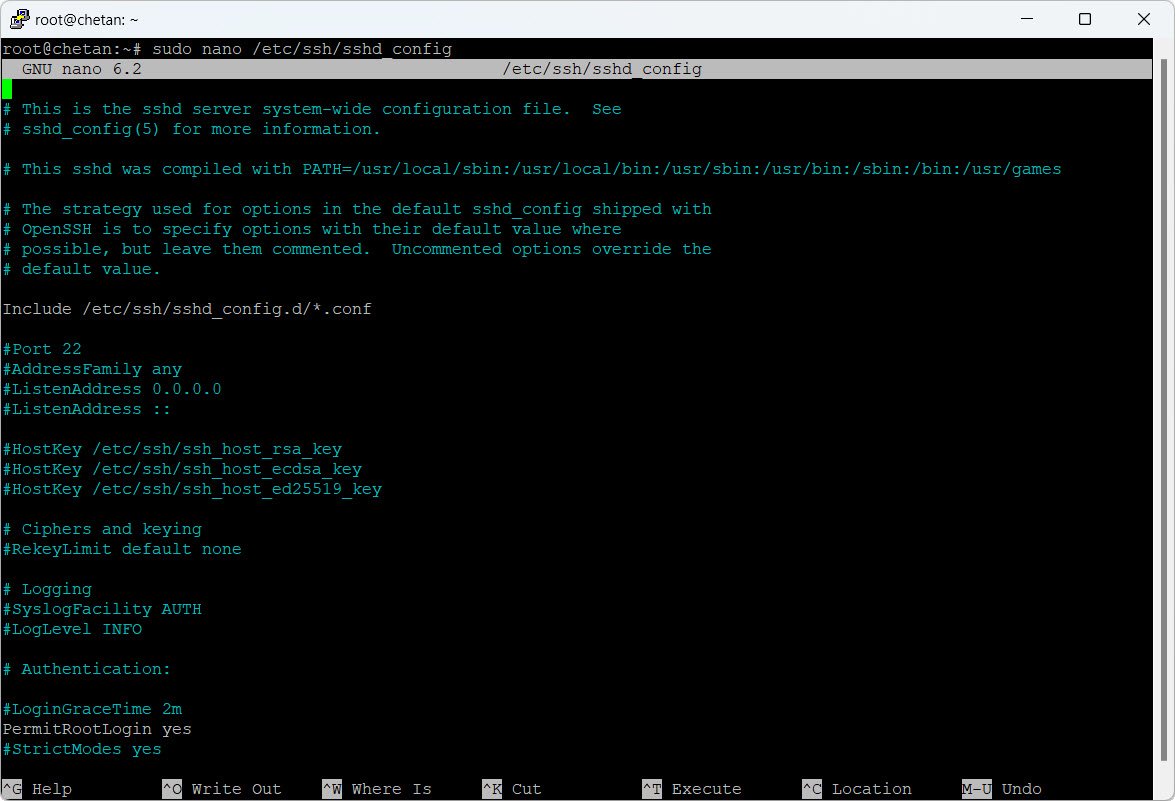
Use key-based authentication instead of passwords:
ssh-keygen -t rsa -b 4096
ssh-copy-id username@server-ip6. Use AppArmor or SELinux
AppArmor and SELinux add an extra layer of security by restricting applications’ access to system resources.
Enable AppArmor:
sudo apt install apparmor apparmor-utils -y
sudo systemctl enable apparmor
sudo systemctl start apparmorTo check AppArmor status:
sudo aa-status7. Secure the Boot Process
To prevent unauthorized users from booting into recovery mode or editing GRUB settings:
Set a GRUB password:
grub-mkpasswd-pbkdf2Copy the generated hash and add it to /etc/grub.d/40_custom:
set superusers="admin"
password_pbkdf2 admin <hashed-password>Update GRUB:
sudo update-grub8. Use Full Disk Encryption (LUKS)
Encrypting your disk ensures that even if someone gains physical access to your device, they cannot access your data.
To encrypt your existing setup:
sudo cryptsetup luksFormat /dev/sdX
sudo cryptsetup open /dev/sdX encrypted_disk9. Enable Automatic Log Monitoring
Use Fail2Ban to protect against brute-force attacks:
sudo apt install fail2ban -yEnable and start Fail2Ban:
sudo systemctl enable fail2ban
sudo systemctl start fail2banCheck logs using:
sudo fail2ban-client status10. Disable USB Ports (Optional)
If you are concerned about data theft via USB, disable USB ports:
echo "blacklist usb-storage" | sudo tee -a /etc/modprobe.d/blacklist.confReload settings:
sudo update-initramfs -u11. Enable Audit Logging
Audit logs track system activities, which helps identify security breaches.
Install the audit daemon:
sudo apt install auditd -y
sudo systemctl enable auditd
sudo systemctl start auditdCheck logs:
sudo ausearch -k logins12. Secure Browsing and Network Connections
Use a VPN to encrypt internet traffic.
Disable IPv6 if not in use:
echo "net.ipv6.conf.all.disable_ipv6 = 1" | sudo tee -a /etc/sysctl.conf
sudo sysctl -pAvoid connecting to public Wi-Fi without security precautions.
Conclusion
Hardening Kali Linux is a crucial step in ensuring that your system remains secure while performing cybersecurity tasks. By following these best practices—keeping your system updated, securing SSH, enabling a firewall, and encrypting your data—you significantly reduce the risk of compromise. Security is an ongoing process, so always stay vigilant and monitor your system for any anomalies.
With these steps, your Kali Linux installation will be more resilient against attacks, keeping your sensitive data and tools secure. Stay safe and happy hacking!



