Secure Shell (SSH) is a widely used protocol for securely accessing and managing Linux systems remotely. Monitoring SSH logs is essential for identifying who is accessing your system, who is attempting to but failing, and why some connections may be denied.
This guide will show you how to view SSH logs on Linux, whether your system uses systemd or the traditional syslog.
Viewing SSH Logs on Systemd-Based Systems
Most modern Linux distributions, such as Ubuntu, Fedora, and CentOS 7+, use `systemd`. The `journalctl` command is the primary tool for viewing logs in these systems.
To check SSH logs, use:
sudo journalctl -u ssh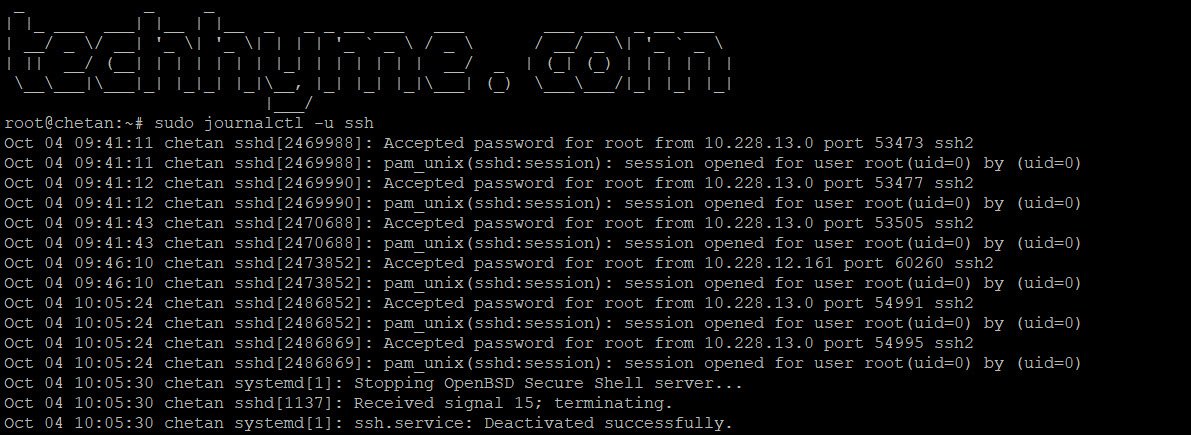
Here’s an example from a production server:
Dec 03 11:38:29 chetan systemd[1]: Starting OpenBSD Secure Shell server...
Dec 03 11:38:30 chetan sshd[1144]: Server listening on 0.0.0.0 port 22.
Dec 03 11:38:30 chetan sshd[1144]: Server listening on :: port 22.
Dec 03 11:38:30 chetan systemd[1]: Started OpenBSD Secure Shell server.
Dec 11 12:39:02 chetan sshd[43588]: error: kex_exchange_identification: Connection closed by remote host
Dec 11 12:39:02 chetan sshd[43588]: Connection closed by 10.228.0.3 port 59944
Dec 11 12:44:19 chetan sshd[43647]: Invalid user cdac from 10.228.0.3 port 58726
Dec 11 12:44:19 chetan sshd[43647]: pam_unix(sshd:auth): check pass; user unknown
Dec 11 12:44:19 chetan sshd[43647]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=10.228.0.3
Dec 11 12:44:21 chetan sshd[43647]: Failed password for invalid user cdac from 10.228.0.3 port 58726 ssh2
Dec 11 12:44:23 chetan sshd[43647]: Connection closed by invalid user cdac 10.228.0.3 port 58726 [preauth]
Dec 11 13:08:02 chetan sshd[43683]: error: kex_exchange_identification: Connection closed by remote host
Dec 11 13:08:02 chetan sshd[43683]: Connection closed by 10.228.0.3 port 40688
Dec 11 13:13:22 chetan sshd[43737]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=10.228.0.3 user=root
Dec 11 13:13:24 chetan sshd[43737]: Failed password for root from 10.228.0.3 port 50292 ssh2
Dec 11 13:13:25 chetan sshd[43737]: Connection closed by authenticating user root 10.228.0.3 port 50292 [preauth]
Dec 24 20:11:53 chetan sshd[149902]: Accepted password for root from 10.228.0.3 port 41751 ssh2
Dec 24 20:11:53 chetan sshd[149902]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0)This output reveals connection attempts, disconnections, and authentication failures.
Filtering Logs by Time
Large public-facing servers can generate hundreds of log lines. Use `journalctl`’s filtering options for specific time ranges:
– Logs from the last 5 minutes:
sudo journalctl -u ssh --since -5m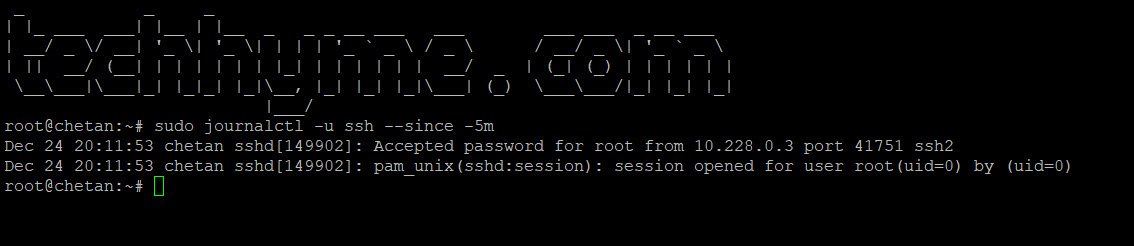
– Logs from the past hour:
sudo journalctl -u ssh --since -1h– Logs from the past three days:
sudo journalctl -u ssh --since -3d– Logs up to a specific time:
sudo journalctl -u ssh --until "2024-12-20 19:00:00"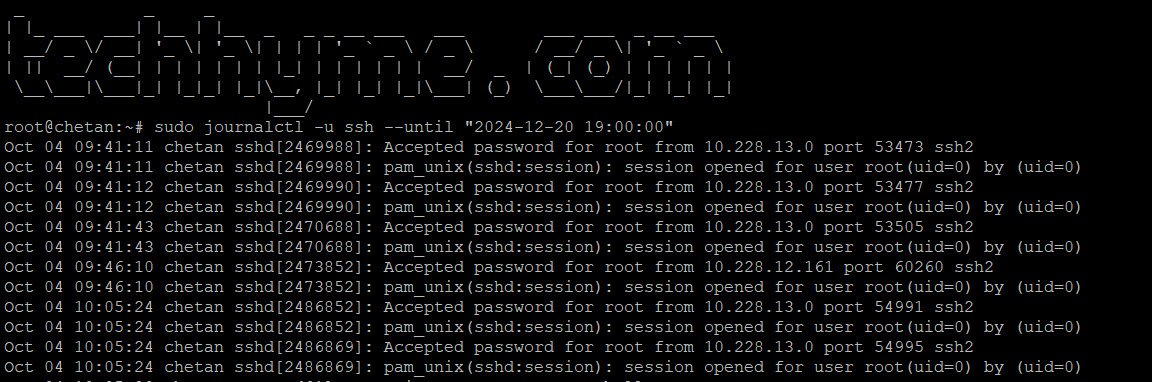
Real-Time SSH Log Monitoring
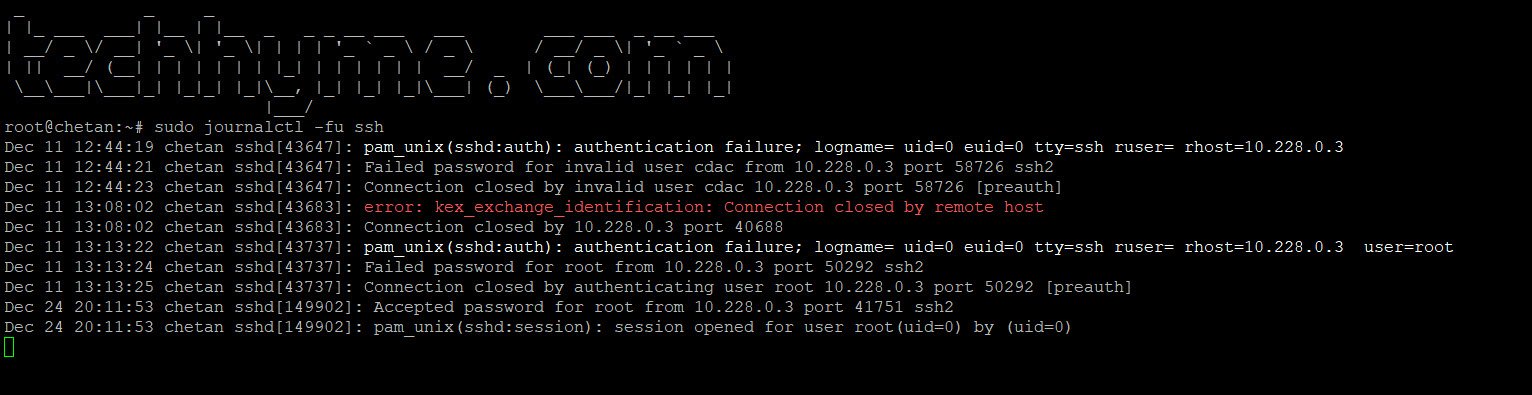
To monitor SSH logs in real time, use:
sudo journalctl -fu sshPress `Ctrl+C` to stop the log viewer.
Viewing Logs on Non-Systemd Systems
If your Linux system doesn’t use `systemd`, you can find SSH logs in the traditional log files, typically located at `/var/log/auth.log` or `/var/log/secure`.
To view SSH logs in this case:
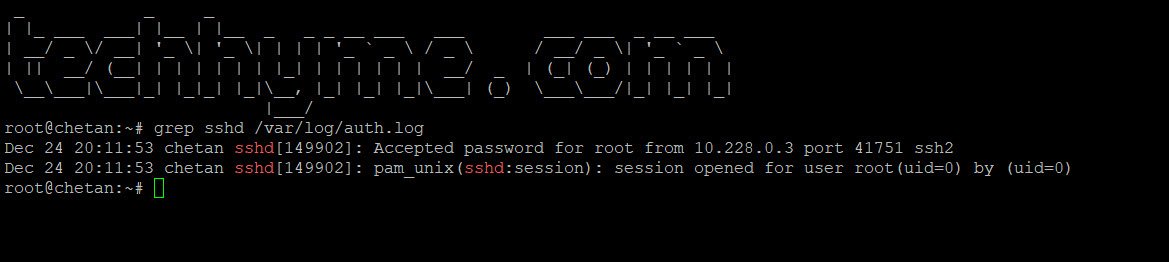
sudo grep sshd /var/log/auth.logExample Output
Dec 24 20:11:53 chetan sshd[149902]: Accepted password for root from 10.228.0.3 port 41751 ssh2
Dec 24 20:11:53 chetan sshd[149902]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0)This output shows failed connection attempts and invalid user login attempts.
Identifying Successful Logins
If you want to see who successfully logged in, use commands like `last` or `lastlog`:
last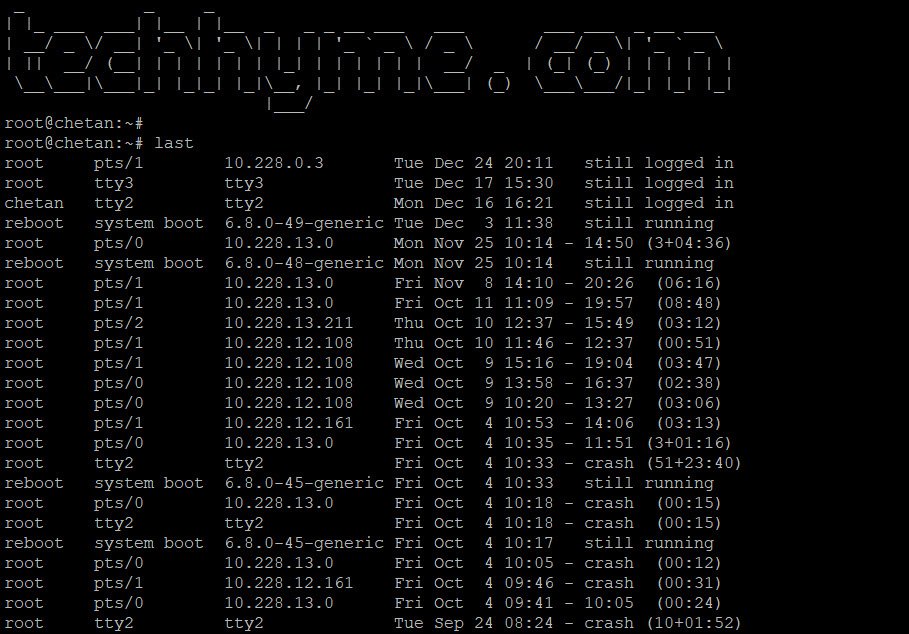
Why So Many Connection Attempts?
If your server is publicly accessible, you’ll notice numerous SSH connection attempts. These are typically automated bots trying to guess usernames and passwords using common defaults.
How to Protect Against Unwanted SSH Attempts
Use Fail2Ban
Fail2Ban monitors logs and bans IPs that show malicious behavior. To install and enable it:
sudo apt install fail2ban
sudo systemctl enable fail2ban
sudo systemctl start fail2ban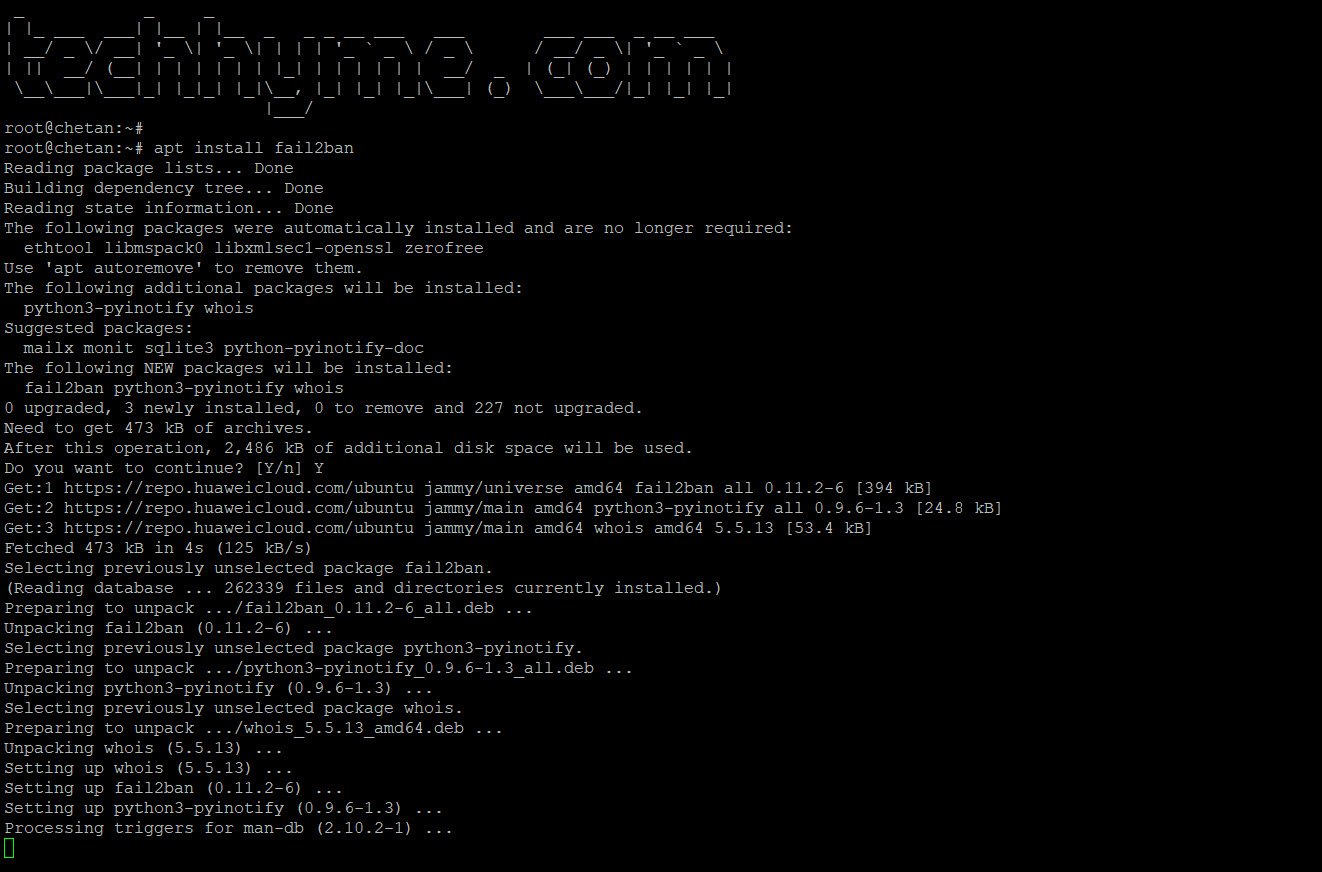
Additional Tips
- Disable root login by editing `/etc/ssh/sshd_config` and setting `PermitRootLogin no`.
- Use SSH keys for authentication instead of passwords.
- Change the default SSH port to something non-standard.
By monitoring and analyzing SSH logs, you can stay informed about access attempts and secure your Linux system effectively.




Pingback: 15-Step SIEM Deployment Checklist to Strengthen Cybersecurity - Tech Hyme