When you compile any source code, an object file is generated of that program and with the help of linker, that object files gets converted to a binary file which, only the machine can understand. This kind of file follows some structures one of which is ELF (Executable and Linkable Format) and to get the information of these ELF files readelf command is used.
readelf command is used to analyze binaries based on Linux. This is most common tool used by security professionals who want to dig useful information from binary files.
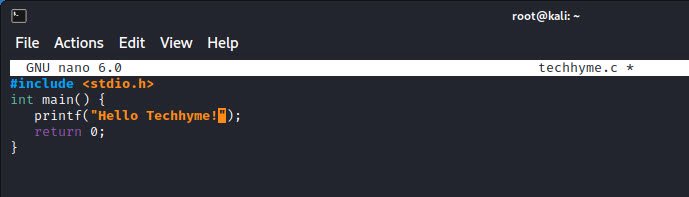
As first step, create a file named as “techhyme.c” using any of your favorite editor such as vi, vim, nano or gedit and write the following code into it.
#include <stdio.h>
int main() {
printf("Hello, World!");
return 0;
}
Compile and Execute the above file by typing the following command:
Command to compile: gcc techhyme.c -o techhyme
Command to execute: ./techhyme

In case, if you want to get more information about the type of the file, then you can use file command:
Command: file techhyme

To display the ELF header of binary file, you can use:
Command: readelf -h techhyme

With -l option, you can also get the information related to program headers of any binary file.
Command: readelf -l techhyme

With -S option, you can display the section headers. As you can see that, there are around 31 section headers of above binary file which we created with GCC compiler.

To display all information related to binary file (Headers, Section Header etc), you can use the following command:
Command: readelf -a techhyme

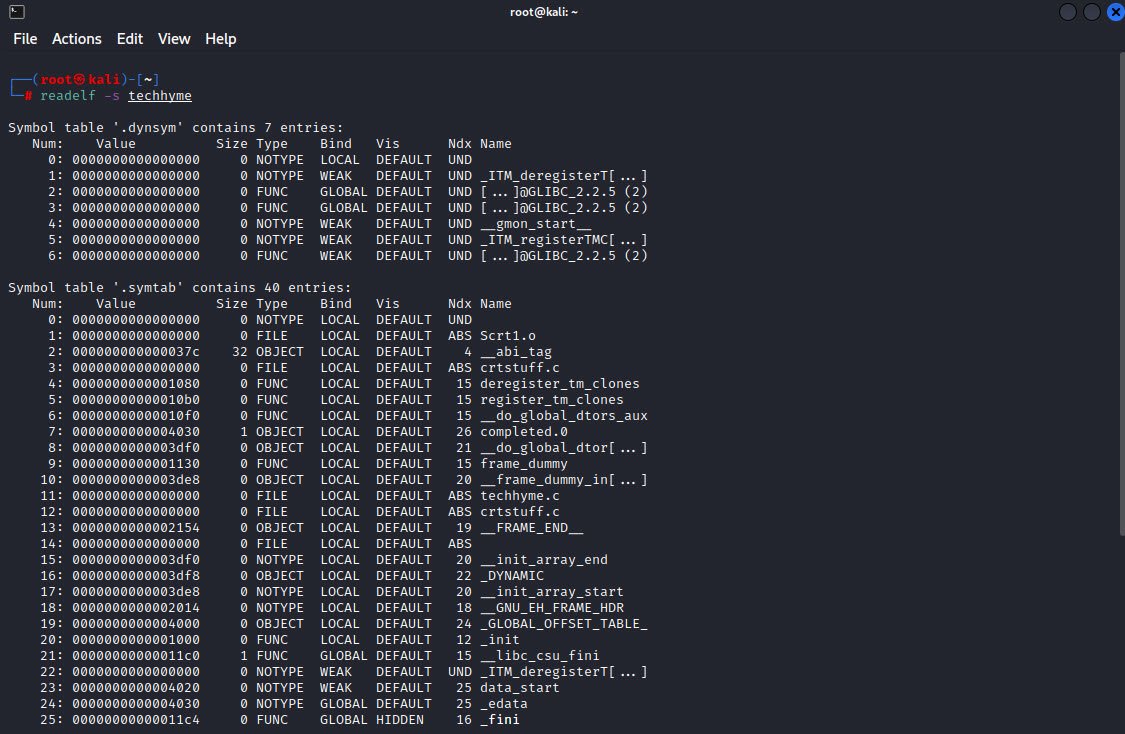
To display the symbol table, you can use -s option.
Command: readelf -s techhyme
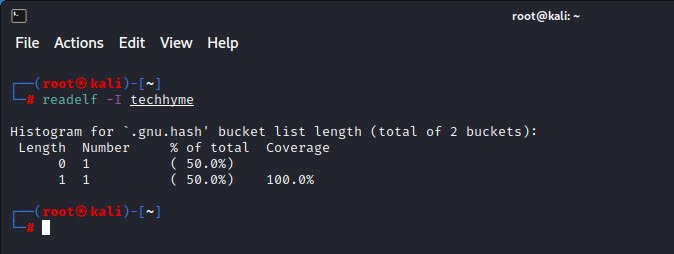
And to display histogram, the command is:
Command: readelf -I techhyme
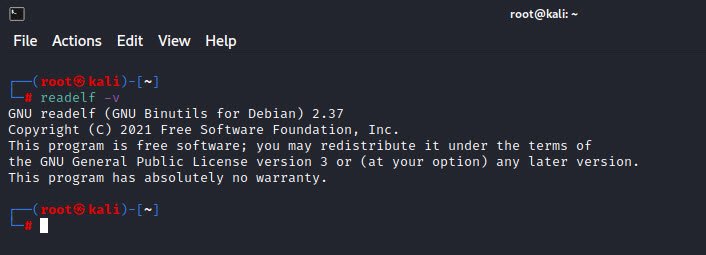
Furthermore, you can also check the version which you are using with -v option:
Command: readelf -v
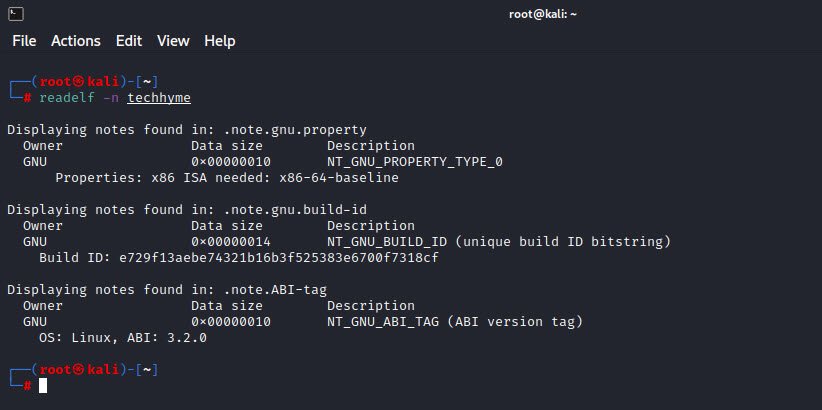
To display the notes of binary file, you can use -n option:
Command: readelf -n techhyme
And to display the relocations, you can use -r option:
Command: readelf -r techhyme

If you have any questions, feel free to ask in the comments section or you can also mail us at hymeblogs@gmail.com.

![[Solution] Fix Windows Defender in Windows 11 Operating System](https://techhyme.com/wp-content/uploads/2022/03/Windows-Defender-Antivirus-Windows-11-Solution-Fix-Repair-Techhyme-150x150.jpg)
