If you’ve ever used the popular All-in-one-Wp-Migration WordPress plugin, you know that it creates backup files in the .wpress format. These files contain your entire WordPress website, including themes, plugins, and content.
But how do you extract or open these .wpress files?
Wpress-Extractor is a lightweight utility that allows you to extract .wpress files effortlessly. It’s especially handy if you need to recover your website from a backup or migrate it to a different server.
1. Download the Extractor
First, grab the Wpress-Extractor from its GitHub repository. Make sure to download the version compatible with your operating system (Windows or Mac).
2. Drop and Extract
If you’re on Windows, simply drop your .wpress file onto the Wpress-extractor.exe executable. Alternatively, follow these steps:
1. Create a directory where you want your extracted files to reside.
2. Copy the downloaded Wpress-Extractor into that directory.
3. Place your .wpress backup file in the same directory.
4. Open a command prompt.
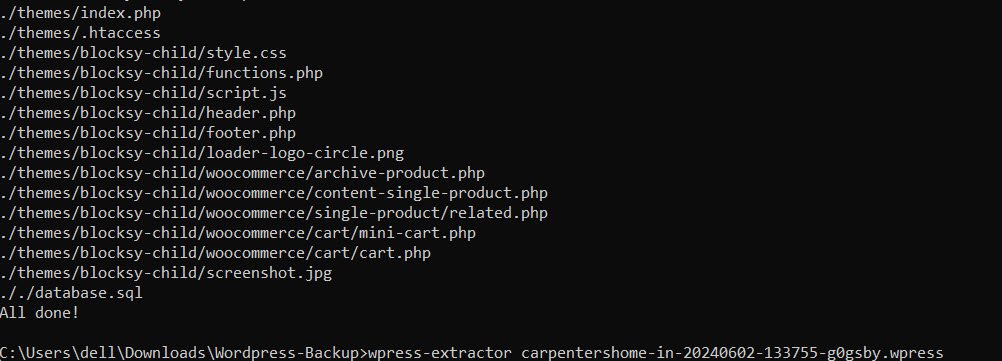
5. Navigate to the directory using the `cd` command. For example:
cd C:\Wordpress-Backup6. Run the following command, replacing `<name-of-your.wpress file>` with your actual file name:
wpress-extractor <name-of-your.wpress file>7. Your files will be extracted into the same directory where the extractor was run (in this case, `C:\Wordpress-Backup`).
Conclusion
Wpress-Extractor simplifies the process of working with .wpress files, making it easier to manage your WordPress backups. Whether you’re a developer, site owner, or just curious, give it a try and unlock the contents of your .wpress backups!



