Winlogbeat is a lightweight log shipper that monitors Windows event logs and forwards them to various destinations. In this article, we’ll walk you through the steps to install and configure Winlogbeat on a Windows system.
Also Read: Installation of Elasticsearch, Logstash, and Kibana (Elastic Stack) on Ubuntu 21.04
Prerequisites:
- Windows machine (Winlogbeat supports Windows 7 or later)
- Internet connection to download the Winlogbeat package
- Administrative privileges to install Winlogbeat as a service
Step 1: Download the Winlogbeat package
Go to the Elastic website (https://www.elastic.co/downloads/beats/winlogbeat) and download the Winlogbeat package. You can download the MSI or ZIP package, depending on your preference.
Step 2: Extract the Winlogbeat package
Extract the contents of the Winlogbeat package to a folder of your choice. In this example, we’ll extract the contents to the C:\Program Files\winlogbeat folder.
Step 3: Configure Winlogbeat
To configure Winlogbeat, you need to edit the winlogbeat.yml configuration file located in the extracted folder. The file contains various settings such as the event logs to monitor, the output destination, and authentication credentials (if needed).
Here’s a sample configuration file:
winlogbeat.event_logs:
- name: Application
- name: Security
- name: System
output.logstash:
hosts: ["10.x.x.x:9200"]In the above configuration, Winlogbeat will monitor the Application, Security, and System event logs and forward them to an Elasticsearch cluster running on the same machine.
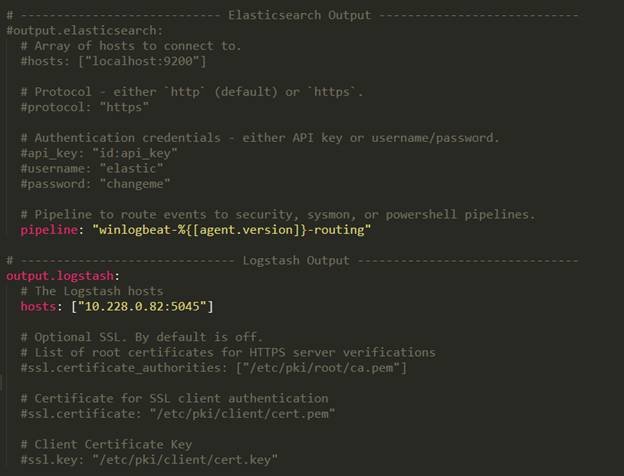
You can customize the configuration file according to your needs. Refer to the Winlogbeat documentation (https://www.elastic.co/guide/en/beats/winlogbeat/current/winlogbeat-configuration.html) for more details.
Step 4: Install Winlogbeat as a service
To install Winlogbeat as a service, open a command prompt with administrative privileges and navigate to the extracted Winlogbeat folder. Run the following command:
.\install-service-winlogbeat.ps1This will install Winlogbeat as a Windows service.
Step 5: Start the Winlogbeat service
To start the Winlogbeat service, open the Services console (services.msc) and locate the Winlogbeat service. Right-click on it and select Start.
Alternatively, you can start the service from the command prompt by running the following command:
Start-Service winlogbeatStep 6: Verify Winlogbeat is working
To verify that Winlogbeat is working, check the logs in the Winlogbeat folder. The logs are located in the logs subfolder.
You can also check the destination output (e.g., Elasticsearch, Logstash, etc.) to ensure that the event logs are being forwarded.
Conclusion
In this article, we’ve covered the steps to install and configure Winlogbeat on a Windows machine. With Winlogbeat, you can monitor Windows event logs and forward them to various destinations for analysis and visualization.



