TCP/IP networks are interconnected across the world, each computer on the Internet must have a unique address (called an IP address) to make sure that transmitted data reaches the correct destination.
Blocks of addresses are assigned to organizations by the Internet Assigned Numbers Authority (IANA). Individual users and small organizations may obtain their addresses either from the IANA or from an internet service provider (ISP).
The Internet Protocol (IP) uses a 32-bit address structure. The address is usually written in dot notation (also called dotted-decimal notation), in which each group of 8bits is written in decimal form, separated by decimal points.
For example, the following binary address: 11000011 00100010 00001100 00000111 is normally written as: 195.34.12.7
The latter version is easier to remember and easier to enter into your computer. In addition, the 32 bits of the address are subdivided into two parts. The first part of the address identifies the network, and the second part identifies the host node or station on the network. The dividing point may vary depending on the address range and the application.
Suggested Read: [Compilation] SEO Tips and Tricks, Resources and Useful Websites
There are 5 standard classes of IP addresses. These address classes have different ways of determining the network and host sections of the address, allowing for different numbers of hosts on a network. Each address type begins with a unique bit pattern, which is used by the TCP/IP software to identify the address class.
After the address class has been determined, the software can correctly identify the host section of the address. The below list shows the 5 IP address classes, including network and host sections of the address for each address type.
The five IP address classes are:
1. Class A IP Address –
Class A addresses can have up to 16,777,214 hosts on a single network. They use an 8-bit network number and a 24-bit node number. Class A addresses are in this range: 1.x.x.x to 126.x.x.x.
2. Class B IP Address –
Class B addresses can have up to 65,354 hosts on a network. A Class B address uses a 16-bit network number and a 16-bit node number. Class B addresses are in this range: 128.1.x.x to 191.254.x.x.
3. Class C IP Address –
Class C addresses can have up to 254 hosts on a network. A Class C address uses a 24-bit network number and an 8-bit node number. Class C addresses are in this range: 192.0.1.x to 223.255.254.x.
4. Class D IP Address –
Class D addresses are used for multicasts (messages sent to many hosts). Class D addresses are in this range: 224.0.0.0 to 239.255.255.255.
5. Class E IP Address –
Class E addresses are for experimental use. This addressing structure allows IP addresses to uniquely identify each physical network and each node on each physical network.
For each unique value of the network portion of the address, the base address of the range (host address of all zeroes) is known as the network address and is not usually assigned to a host. Also, the top address of the range (host address of all ones) is not assigned, but is used as the broadcast address for simultaneously sending a packet to all hosts with the same network address.
Private IP Addresses
If your local network is isolated from the Internet (for example, when using Network Address Translation, NAT), you can assign any IP addresses to the hosts without problems, However, the IANA has reserved the following three blocks of IP addresses specifically for private networks:
- 10.0.0.0 – 10.255.255.255
- 172.16.0.0 – 172.31.255.255
- 192.168.0.0 – 192.168.255.255
Choose your private network number form above mentioned range. Some NETGEAR or DLINK products have DHCP servers that are pre-configured to automatically assign private addresses.
Types of IP Addresses
There are two types of IP addresses:
- IPv4 (e.g. 101.168.3.33)
- IPv6 (e.g. 0:0:0:0:0:ffff:d83a:d9ce)
IPv6 was developed due to the internet growing so fast that essentially, we were running out of numbers. IPv6 has allowed us to keep expanding, and new IP addresses can be assigned. With that being said, IPv4 addresses are still the most commonly used IPs on the web and with ISPs.
Find Your IP Address
Regardless of the device and OS that you’re running, you should navigate to your WiFi or Ethernet settings to find your machine IP address.
Here is the list of websites through which you can easily find your public IP address along with other information such as ISP Name, City, Country etc or you can simply type “What is my IP” into Google and you’ll get the same result.
- https://whatismyipaddress.com/
- https://www.whatismyip.com/
- https://nordvpn.com/what-is-my-ip/
- https://kinsta.com/tools/what-is-my-ip/
- https://www.tunnelbear.com/whats-my-ip
- https://www.expressvpn.com/what-is-my-ip
- https://whatismyip.host/
- https://www.maxmind.com/en/locate-my-ip-address
- https://www.privateinternetaccess.com/pages/whats-my-ip/
- https://www.name.com/ip
- https://ipaddressworld.com/
- https://www.uptrends.com/tools/ip-address
- https://www.vyprvpn.com/what-is-my-ip-address
- https://mxtoolbox.com/whatismyip/
- https://www.reviews.org/internet-service/whats-my-ip-address/
- https://www.internetmarketingninjas.com/whats-my-ip.php
- https://www.iplocation.net/find-ip-address
- https://www.dunplab.it/what-is-my-ip
On Windows 10 Machine –
Search for “cmd” using Windows search or type in run command. In the resulting pop-up box, type “ipconfig” then enter.
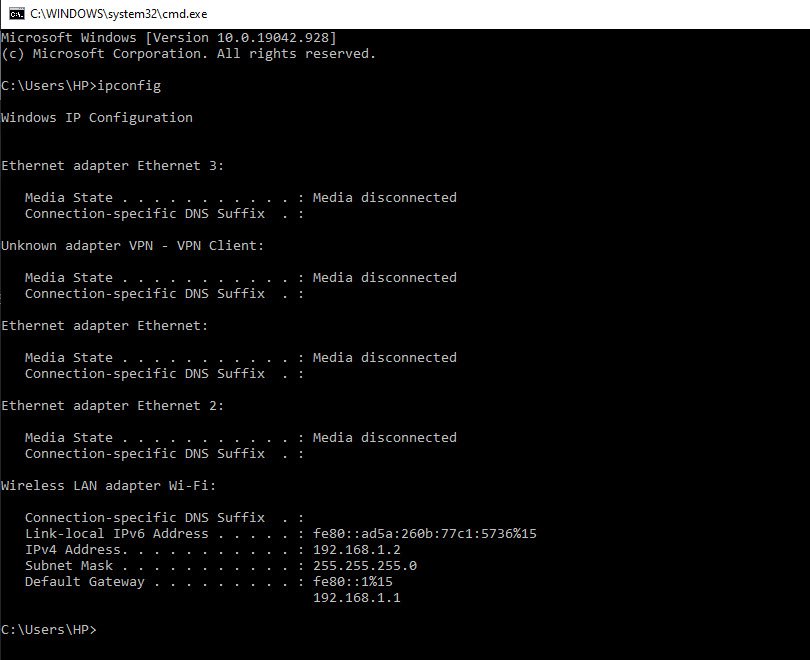
In case if you want more detailed information such as MAC Address, Hostname, Adapter name etc then type “ipconfig/all” command:

You can also get the IP address in windows machine by navigating Wi-Fi or Ethernet -> Click on network you’re currently connected to -> Select Properties -> Your IP address is listed next to “IPV4 address”.
Security Threats
Cyber criminals or Hackers can use various techniques to obtain your IP address. Here is the list of some security threats related to Internet Protocol which are wild in the market.
- Online Stalking
- Downloading illegal content
- Tracking down your location
- Directly attacking your network
- Hacking into your device




Pingback: 10 Different Ways To Get Someone's IP Address - Checklist 2023 - Tech Hyme
Pingback: Top 9 Basic Key Features of IPv6 Protocol - Tech Hyme