In an era dominated by digital connectivity, it’s crucial to be aware of the information flowing in and out of your computer. Understanding which applications are sending data can empower you to take control of your privacy and security.
This article will explore two methods to check which apps are sending information: using the Task Manager and utilizing Netstat commands.
1. With Task Manager:
Task Manager is a built-in utility in Windows that provides a comprehensive view of your system’s performance and processes. Here’s how you can use it to identify data-transmitting applications:
Right-click on the taskbar and select “Task Manager,” or press “Ctrl + Shift + Esc” to open it directly.
With Task Manager displayed, click the More Details arrow. This will expand the Task Manager options. From here, click the App History tab and then the Network Column so that there’s a downward pointing arrow above it.

This indicates network use in a descending order of amount of data sent.
If you don’t see the “Network” column, right-click on any column header, choose “Select Columns,” and then check the “Network” option. The “Network” column will show the amount of network data each process is using.
2. With Netstat Commands:
Netstat is a command-line tool available on Windows and Unix-like systems that displays network connections, routing tables, interface statistics, masquerade connections, and more. The following Netstat command provides detailed information about TCP connections and the applications using them:
Another excellent method is by using the Netstat command. Click on Windows Start button and enter CMD, then right-click the Command Prompt Option and choose Run as Administrator from the menu.
When the message to authenticate the action pops up, click on YES.
With the command prompt open, enter the following command and press Enter:
netstat -e -s -p tcp -b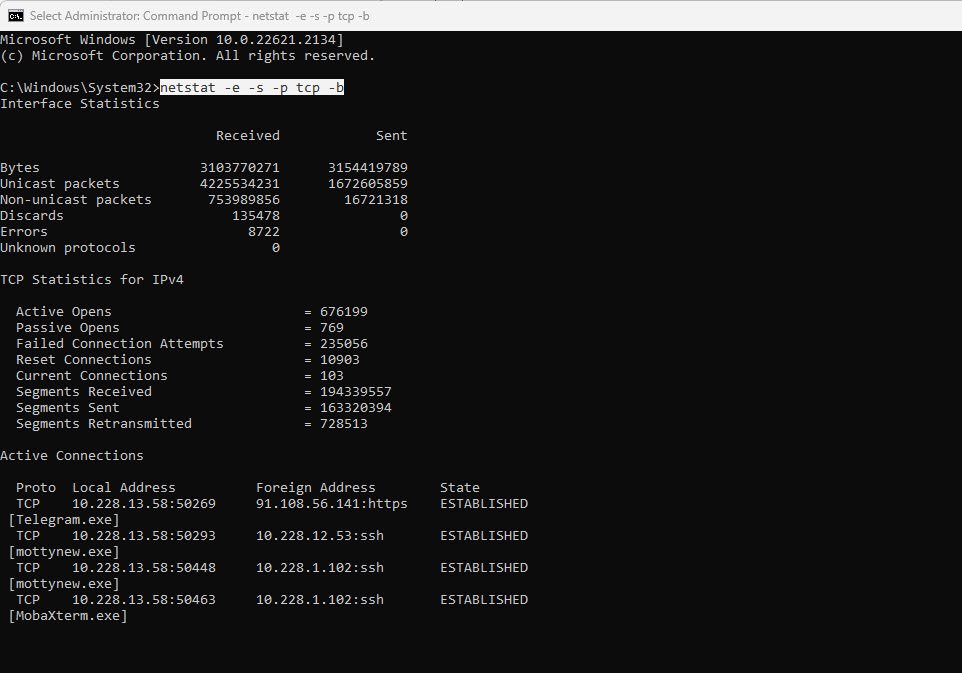
The command will display a list of active TCP connections, their state, and the corresponding executable (application) names. Identify processes with established connections to remote addresses, as they are likely sending or receiving data. It can be confusing to view at first but after a moment or two, it should begin to make sense.
In case, if you want to send the output to a file, then you can use the following command:
netstat -e -s -p tcp -b > save.txt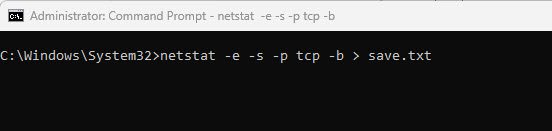
If you want to simplify the information and the process, you can use the following command:
netstat -b 5 Press Ctrl+C, once you capture the enough data.
Conduct online research or use built-in tools like Task Manager to gather more information about the identified processes. Be cautious and investigate further if you find any unfamiliar or suspicious applications.
Conclusion
Knowing which applications are sending information from your computer is a crucial step in maintaining your privacy and security. By utilizing built-in tools like Task Manager and command-line utilities like Netstat, you can gain insights into the data flows on your system.
Regularly monitoring and investigating network activities empower you to make informed decisions about your digital security and maintain control over your personal information.



