Ubuntu is a popular Linux distribution known for its user-friendly interface and robust security features. However, like any operating system, Ubuntu may have open ports that, if left unattended, can pose security risks. Open ports can potentially expose your system to unauthorized access and attacks. To enhance the security of your Ubuntu system, it’s essential to know how to close open ports.
In this article, we’ll guide you through the process of identifying open ports and securing your system.
Why Close Open Ports?
Open ports are network access points that allow data to enter or leave your computer. While some ports are necessary for system services and applications to function correctly, open ports that you don’t actively use can be security vulnerabilities. Cyber attackers may exploit these open ports to gain unauthorized access to your system, potentially compromising your data and privacy.
Here’s how to identify and close open ports in Ubuntu:
1. Identifying Open Ports
Before closing open ports, you need to identify which ports are currently open on your system. You can use various tools and commands for this purpose. One of the most commonly used commands is `netstat`. Open your terminal and type:
netstat -tulnThis command will display a list of open ports, both for TCP and UDP connections. You can also use the `ss` command, as mentioned in the previous response:
ss -tlThe command “ss -tl” is used to display a list of listening TCP sockets on a Linux system. It shows information about TCP connections that the system is currently listening for. The “ss” command is a replacement for the older “netstat” command and provides detailed socket statistics.
Here’s a breakdown of the command:
– “ss”: This is the command to invoke the socket statistics utility in Linux.
– “-t”: This option is used to display TCP sockets.
– “-l”: This option is used to show only listening sockets.

Similarly, if you want to have a list of both TCP and UDP in the listening state, you can use the given command:
ss -tul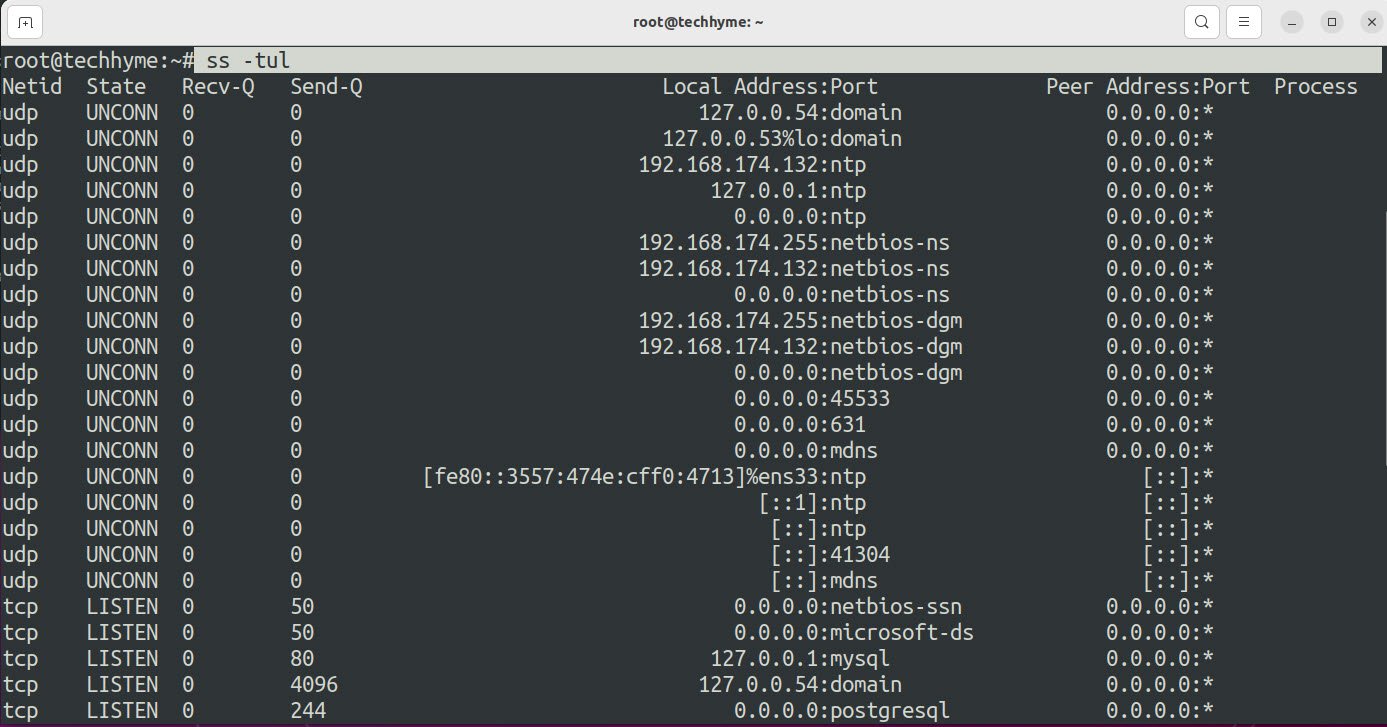
To display the listening port of each service, you can use -n option and for more fine-tuned results, you can always use the grep command:
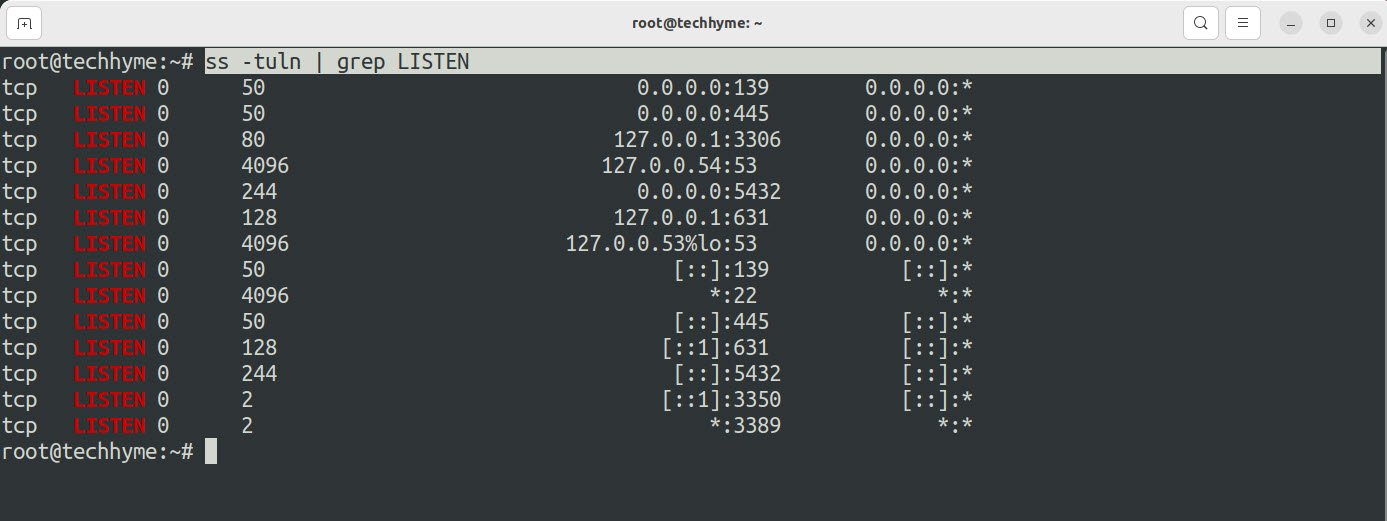
ss -tuln | grep LISTENThe above command “ss -tuln | grep LISTEN” is used to display a list of listening network sockets in a Linux system. It’s a way to filter the output of the “ss” command to show only the sockets that are in a “LISTEN” state. Here’s what each part of the command does:
2. Close Open Ports
To close an open port, you have a few options depending on the nature of the port:
a) Firewall Rules: Ubuntu uses a firewall management tool called Uncomplicated Firewall (UFW) by default. You can use UFW to create rules that block traffic on specific ports. For instance, if you want to close port 8080, use the following command:
sudo ufw deny 8080To apply the rules, enable UFW:
sudo ufw enableb) Disabling Services: Many open ports are associated with running services or daemons. You can stop and disable these services to close their associated ports.
To close the port, first, you will need to stop the service and to find the service name, you can use the same ss command with -p option:
ss -tulnp | grep LISTEN
As you can see, the xrdp is utilizing port number 3389. So let’s stop it using the given command and then recheck again:
service xrdp stopRemember, disabling services like xrdp or ssh should be done with caution, as it might affect your ability to access the system remotely.
c) Uninstalling Software: If you have software installed that opens ports you no longer need, consider uninstalling it. For example, if you want to close port 3306 associated with the MySQL database server:
sudo apt-get remove mysql-serverSecuring your Ubuntu system by closing open ports is a crucial aspect of maintaining a robust defense against unauthorized access and cyber threats. By following these steps to identify, evaluate, and close open ports, you can significantly enhance the security of your Ubuntu installation.
Remember always to be cautious and verify that the ports you close are genuinely unnecessary to prevent disrupting essential services. Regular auditing and proactive security measures will help you maintain a more secure and efficient Ubuntu system.