The first step in port scanning is to check if a specific port is open or being used by a service. This can be done using the nc command, or with other tools such as telnet, nmap, or socat. Once a port is identified as open, further analysis can be done to determine what service or application is listening on that port.
To scan ports using netcat, you can use the nc command followed by the target IP address and port number you want to scan. For example, to scan a particular port i.e. 22 on a host with IP address 192.168.174.132, you can use the command: nc -zvn 192.168.174.132 22.
The -v option is for verbose output, the -n option tells nc to use IP addresses instead of hostnames, and the -z option tells nc to only scan for open ports without sending any data.
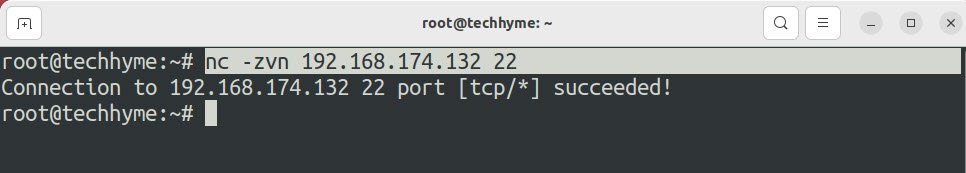
And as you can see, port no 22 is open for 192.168.174.132.
And if you are getting such error “Connection refused”, then it means the port you are scanning with netcat is closed.

To scan multiple ports at once using the netcat, you’d need to follow the given command syntax:
Command: nc -vz -w3 <Target> <Port 1><Port 2><Port 3>
Indeed, you can use the previous method to scan for multiple ports but what if you want to scan more than 50 or 100 ports? You can define the range.
Command: nc -vz -w3 <Target> <Port Range>
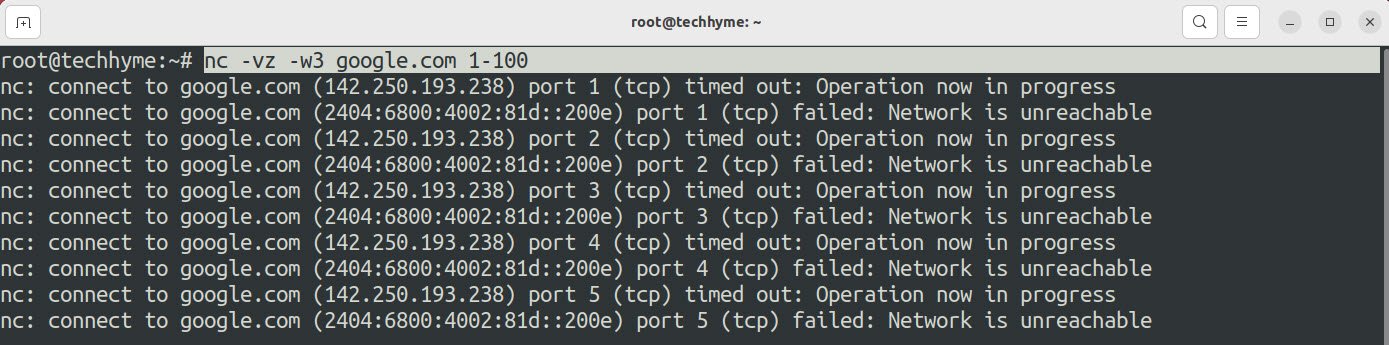
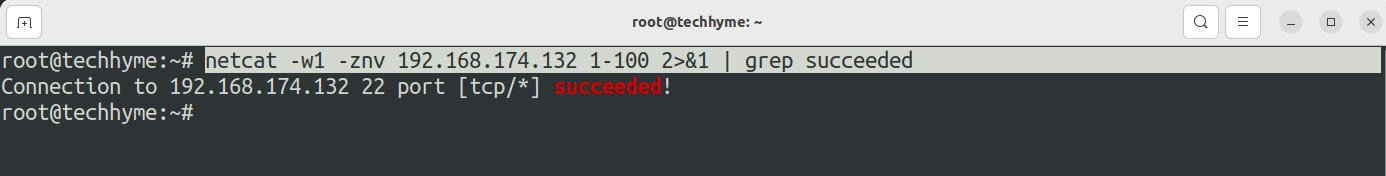
Seems pretty long list of unavailable ports right? In this case, you can use the grep command to fetch only the open ports:
Command: netcat -w1 -znv <Target> <Port Range> 2>&1 | grep succeeded
Here,
- -w1 will force the netcat command to wait for 1 second for each port.
- 2&1 redirects standard error.




Pingback: Top 100 Vulnerabilities in Cybersecurity - Tech Hyme
Pingback: Netcat (nc) - The Swiss Army Knife of Networking - Tech Hyme
Pingback: How to Close Open Ports in Ubuntu - Tech Hyme