
The security tools market is as big as the field itself. Separating the hundreds of different tools helps to break them down into different categories.
The first category is event managers. These tools respond to events that occur on the networks you monitor. They analyze the logs on your systems to detect these events. Another handy tool is packet sniffers that allow you to decode packets while digging into traffic to scan their cargo. Packet sniffers are used when you delve deeper into security events that occur.
Intrusion Detection and Prevention Systems are another useful category of tools. They may look like firewalls and antiviruses, but they differ greatly in function. When it comes to this software, you should always consider them as a perimeter around your network that is there to detect illicit activity.
Of course, not every tool can be categorized because of how specific they are when it comes to function and design. However, they can be very useful for many different situations. It is very difficult to determine which tools are better than others in different categories because of the different purposes they may have.
Most of the tools we are talking about are vastly different from each other and you can never say that one is absolutely better than the other. This means it is difficult to select tools for each different job, but here are some commonly used tools that you should always keep in mind when taking on a job.
1. SolarWinds Log and Event Manager (LEM)
You may have never heard of SolarWinds, but you should listen carefully now. This company has created a huge amount of useful management tools over a number of years. In the market for NetFlow collectors and analyzers, the NetFlow Traffic Analyzer from SolarWinds is a popular tool. Another great tool SolarWinds has given us is the Network Performance Monitor, which is one of the best in the market for network monitoring SNMP tools.
SolarWinds LEM is now Security Event Manager (SEM)
In short, what you need to know about SolarWinds is that they offer a wide variety of free tools that you can use for different tasks and that they can fulfill many different roles that you may be trying to fulfill yourself. Network and system administrators are often grateful to SolarWinds for being a great source of useful tools.
Speaking of SolarWinds, it’s hard to ignore some of their biggest bits of software. If you’re looking for network security tools, you’ll want to check out the LEM, short for Log and Event Manager. This is an easy choice if you are looking for a security and event management system that is very beginner friendly. This is the tool you want to start with.
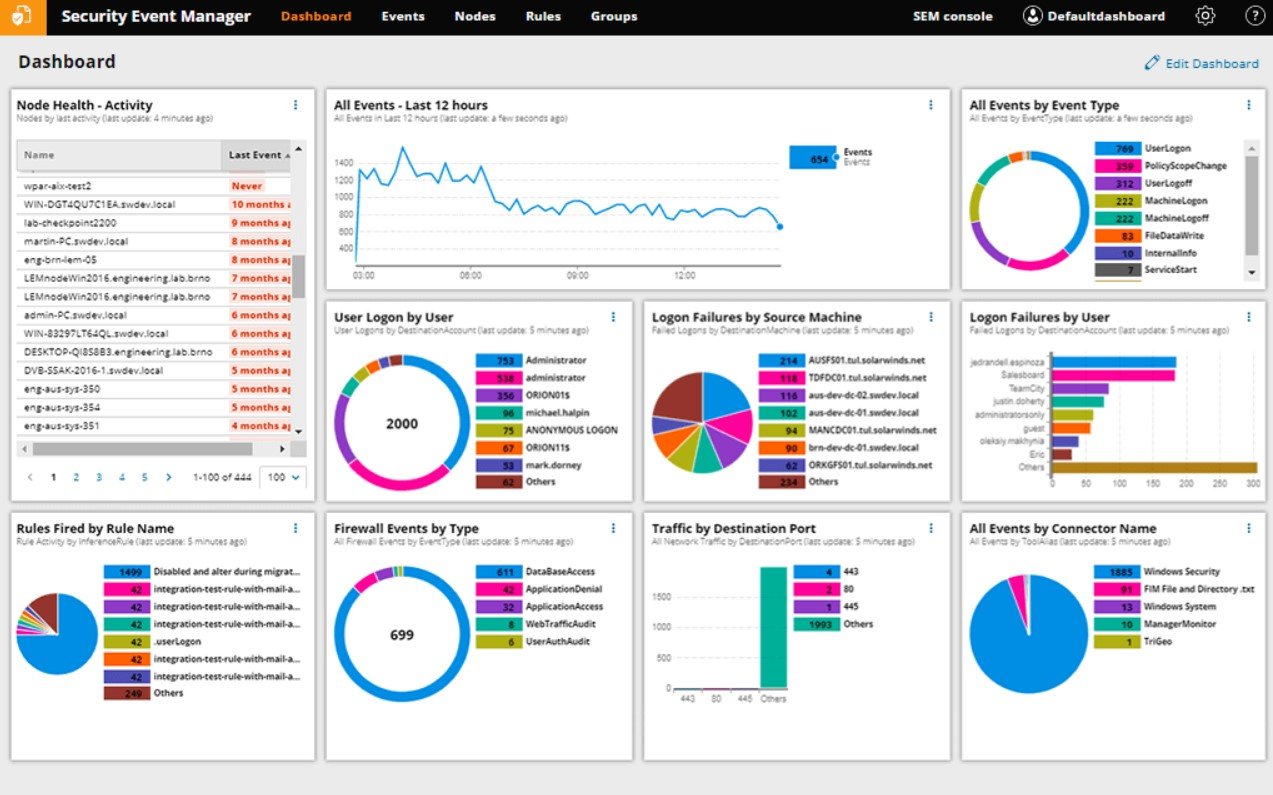
In the entry-level SIEM market, this is arguably the most competitive option. When dealing with SolarWinds, you can expect to get everything every base system would have and something more. The SolarWinds LEM a.k.a SEM has a great log management function and runs on an impressive engine.
The LEM also offers you impressive response functions. It detects threats in real time and is very reliable in what it does. The tool works great when trying to protect yourself from zero-day exploits and threats that you don’t know about, as it is not based on signature creation. Behavior is what this tool is looking for. You rarely need to update it. One of the best assets of the LEM is the dashboard. The system is very simple and makes quick work of finding anomalies and reporting them.
Read more about SEM, https://www.solarwinds.com/security-event-manager/use-cases/log-event-manager-software
2. SolarWinds Network Configuration Manager
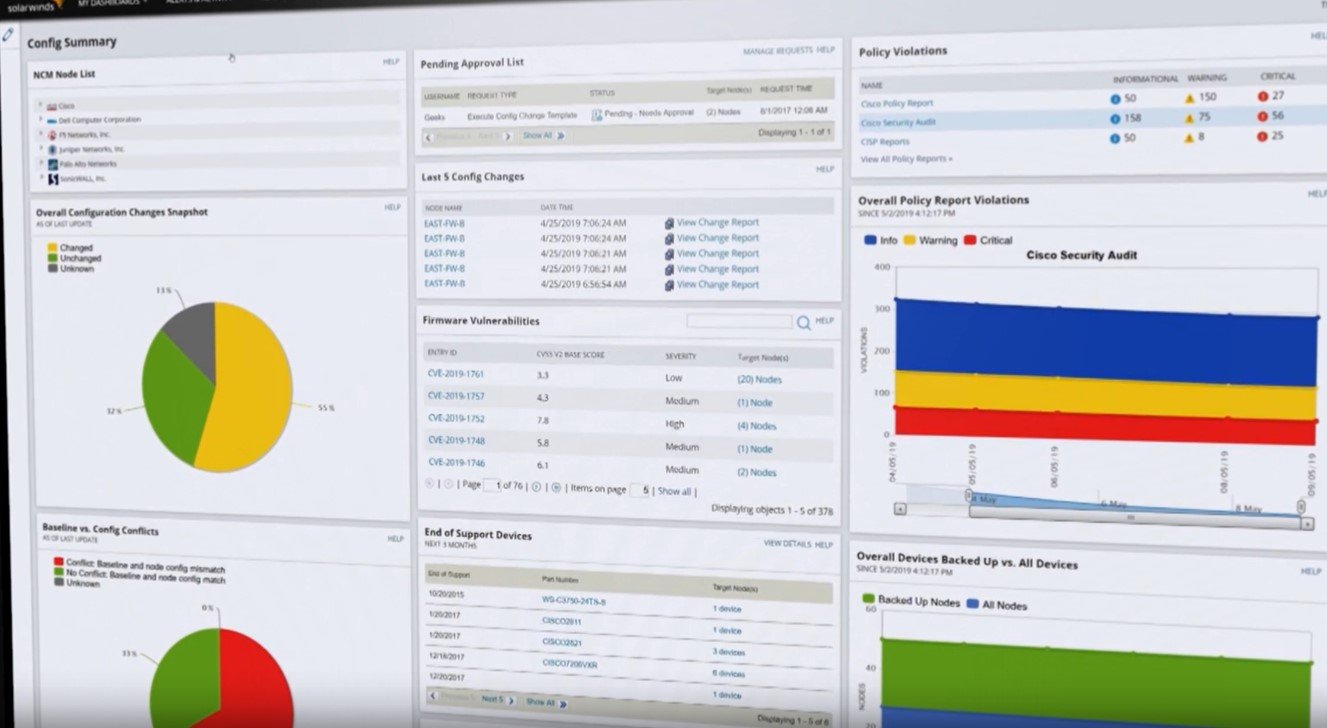
The LEM isn’t the only impressive piece of software that SolarWinds can boast. They have several other tools that focus on network security. One is their Network Configuration Manager, which is used to monitor your equipment and ensure everything is configured based on certain standards. What it does for your safety is that it detects unauthorized changes to your system. This is useful because these changes can be a good sign of an upcoming attack.
The main function of this software is to help you recover by restoring your system to the latest authorized configurations. It also highlights the changes and saves the information in a configuration file. Another thing it helps you with is compliance. It helps you pass audits because of the standardized reports it creates on the job.
Read more about network configuration manager, https://www.solarwinds.com/network-configuration-manager
3. SolarWinds User Device Tracker
This is another one of the great tools that SolarWinds offers. It is a great tool that everyone who works in computer security should have. It tracks endpoint devices and users to improve your safety. You can use it to identify which ports are being used and which are available.
This tool is great in situations where you expect an attack with a specific target. The tools help you by identifying the user with suspicious activity. The searches performed through this software are based on username, IP / MAC addresses and host names. The search can go a little deeper and even go as far as to scan earlier connections of the suspect.
4. Wireshark
Speaking of Wireshark, it would be insulting to say that it is just a security tool. This tool is very popular and is used. It is acclaimed as one of the best capture and analysis packages. This tool is used to thoroughly analyze network traffic. It can capture and decrypt any package so you can inspect the data it contains.
Wireshark has built a great reputation. Due to the quality of the service it offers, it has pretty much become the standard for the other tools on the market. The competition always tries to emulate it as much as possible.
Many administrators use the Wireshark to check the recordings obtained through other software. This has been done so many times that the newer versions of the software allow you to run a capture file when setting up that you already have to go through traffic immediately. Where the tool excels most is the filters that come with it. They are a great addition as they help you pinpoint the exact data that is relevant to you.
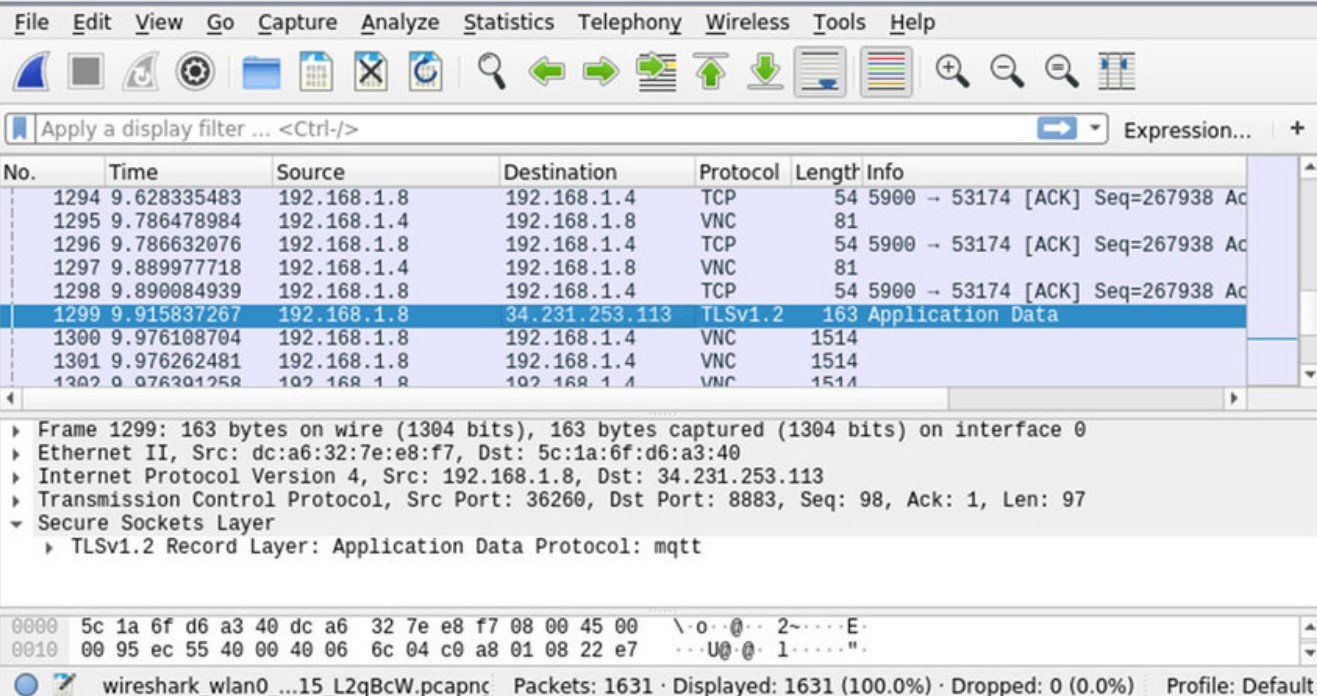
The software is difficult to get used to. There are courses that last several days and provide instructions on how to use them. Nevertheless, it is worth learning how to use Wireshark. It is an extremely valuable tool for any administrator. The tool is free and can be used on most operating systems. You can get one yourself on the official website.
5. Nessus Professional
Among solutions for identifying malware, problems and vulnerabilities, the Nessus Professional is one of the most widely used. Millions of professionals use the Nessus Professional because of the outside view it offers them. It also gives you great insight into how to improve the security of your system.
Suggested Read: A Step-By-Step Guide to Penetration Testing
The Nessus Professional offers one of the broadest coverage when it comes to threats. It uses a lot of impressive intelligence and is very easy to use. The software is also updated quite often which means that you will never have problems with previously unseen problems. It has quite a comprehensive package when it comes to vulnerability scanning.
6. Sniffing
Among open source IDSs, Snort stands out among the best. This intrusion detection system was created in 1998. It became the property of the Cisco system in 2013. Snort entered the Open Source Hall of Fame in 2009. This means it has been recognized as one of the best open source software ever. This speaks volumes.
There are three modes in the snort: sniffer, packet logger and network intrusion detection. The sniffer mode is the basic mode and the main function is to read network packets and display their content. The package logger is quite similar, except that the scanned packages are logged on the disk. The most interesting mode is the intrusion detection mode.
It analyzes traffic according to the instructions of a rule set set by you. Based on what kind of threat it has found, you can go through different lines of action.
Snort can find many different types of cracks in the system that could be a sign of a possible attack that may take place in the future. Snort has a website where you can download it.
7. TCPdump
If you were ever interested in which packet sniffer was the first, look no further than Tcpdump. The first release of the software was in 1987. Since then it has been regularly updated and maintained. However, the core of the software has always remained the same. Most Unix-like systems come with pre-installed TCPdump because it is the default tool for those operating systems.
The standard way of working for the TCPdump is to capture the traffic in landfills on the screen. You may notice that this is quite similar to the sniffer mode we talked about earlier. Dumps can be piped to capture specific files for further analysis, similar to the packer logger mode. Wireshark is usually used in conjunction with TCPdump.
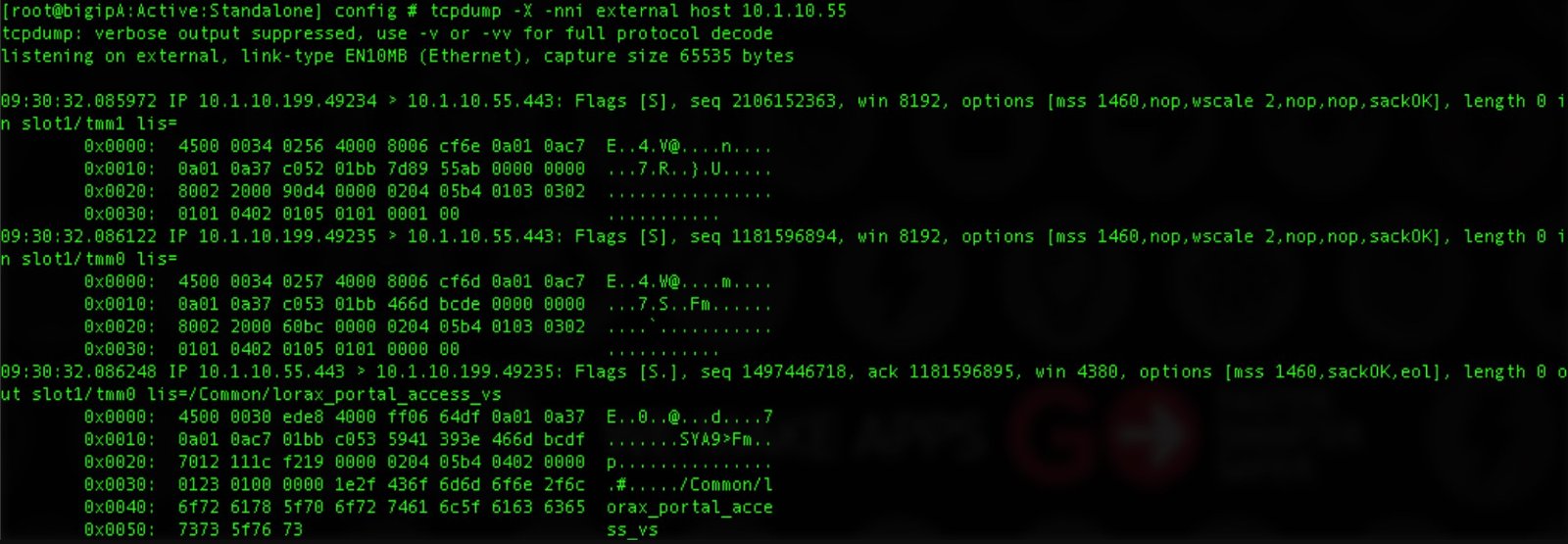
The greatest strength of the TCPdump is the fact that it easily captures filters and uses various Unix commands to make work much shorter and easier. If you have a good knowledge of the Unix-like systems, dealing with traffic and capturing the specific parts you are interested in will not be a problem.
8. Kismet
A lot can be said about Kismet. It is a burglary detection system, packet sniffer and network detector in one. The preferred function is when working on a LAN. It works with most wireless cards and can pass through many different types of traffic. This tool is compatible with Linux, OS X, OpenBSD, NetBSD and FreeBSD. The Kismet has very limited support for Windows systems because very few network adapters support Kismet’s monitoring mode.
This software is licensed under the Gnu GPL license. The way it differs from other wireless network detectors lies in the fact that the work is done passively. It does not use logable packets, but directly detects the presence of access points. It also makes connections between them. Of the open-source tools for wireless network monitoring, this is the most widely used.
9. Nikto
Nikto is another piece of excellent open-source software. It is one of the most popular web server scanners. Its main function is to run web servers through a myriad of tests to find traces of thousands of different programs that can threaten your security. It can work with different versions of many different servers. It checks server configurations and checks for system anomalies.
Nikto is designed for speed rather than stealth. It will test a web server as soon as possible, but its passage will appear in log files and be detected by intrusion detection and prevention systems.

Nikto is licensed under the GNU GPL. It can be downloaded from GitHub.
10. OpenVAS
The OpenVAS, also known as the Open Vulnerability Assessment System, is a set of tools that provide many comprehensive vulnerability scans. Most of the system’s components are open source and the software is completely free.
OpenVAS has two main components. The first part of the software is the scanner. As the name suggests, it is responsible for scanning the computers. The manager is the second part. The manager works as a controller for the scanner and works with the results of the scans.
The Network Vulnerability Tests database is an additional component that you can add to the software to make it more efficient. You can download the software from two software: the Greenborne Security Feed and Greenborne Community Feed. The latter is free while the former is paid.
11. OSSEC
OSSEC stands for Open Source Security. It is a host-based program used for intrusion detection. This type of detection system differs from the network-based counterparts in that the host itself runs the program. Trend Micro owns OSSEC. In terms of IT security, this name carries quite a bit of weight.
The primary use of this software is in Unix-like software where the work is devoted to configuration and file scanning. It also sees some use on Windows systems where it keeps an eye on the registry. The tool alerts you via the console or email when something suspicious is detected.
OSSEC has a relatively major drawback, just like any other host-based IDS. You must install a new copy on every device you want to protect. This is somewhat mitigated by the fact that the information can be directed to a centralized console.
OSSEC is also licensed under the GNU GPL. If you want to use it, you can download it from the website. OSSEC is also distributed under the GNU GPL license and can be downloaded from its own website.
12. Nexpose
Nexpose is another common tool. It was created by Rapid7 and is used to manage vulnerabilities. It does everything a vulnerability manager can. It complies with the so-called lifecycle of the vulnerability manager. This means that the software handles all phases involved in the process.
When it comes to the features it comes with, it’s a complete whole. The software has many interesting features, such as the virtual scan option and dynamic detection. It can scan many different types of environments and can handle a number of IP addresses. It is software under development and is constantly growing.
There are two versions of the product you can get. There is a community edition that has far fewer features than the full commercial versions, prices start at $ 2,000 a year. If you have any questions about the software or would like to download Nexpose, please visit the official website.
13. GFI LanGuard
The GFI LanGuard is acclaimed as an excellent IT security tool for companies. This tool was created to assist you with network scanning and automatic patching. It also helps you meet compliance standards. This software is compatible with most operating systems.
GFI LanGuard has a very intuitive dashboard that also helps identify viruses. It also works with web browsers. Another strength of the software is the fact that it works with a wide variety of devices.
If you are looking for the GFI LanGuard, you will find that there are many different options when it comes to additional features. The price is flexible and is renewed annually. If you are unsure about purchasing the software, you can try the trial version first.
You may also like:- Gmail and Facebook Users Advised to Secure Their Accounts Immediately
- Pentagon’s Proactive Approach to Cybersecurity – Over 50,000 Vulnerability Reports Since 2016
- Windows Hardening – Key Points To Remember
- Top 10 Fundamental Questions for Network Security
- How to Remove x-powered-by in Apache/PHP for Enhanced Security
- 12 Point Checklist – PHP Security Best Practices
- Secure Programming Checklist – 2023 Compilation Guide
- The Ultimate Network Security Checklist – 2023 Complete Guide
- A Comprehensive Guide to Crafting Strong Passwords
- Top 28 Essential Tips To Safeguard Your Computer








