
DNS enumeration is the process of discovering all the DNS records associated with a particular domain or hostname. The purpose of DNS enumeration is to gather information about the target system that can be used in a variety of ways, including reconnaissance, vulnerability assessment, and penetration testing.
There are various tools and techniques that can be used for DNS enumeration, including:
- DNS zone transfer: This technique involves requesting a copy of the DNS zone file from the target DNS server. This can be done using tools like Dig or NSLookup.
- Reverse DNS lookup: This technique involves looking up the hostname associated with a particular IP address. This can be done using tools like Dig or NSLookup.
- Brute-force DNS enumeration: This technique involves guessing subdomains or hostnames associated with the target domain. This can be done using tools like Fierce, Sublist3r, or Knock.
- Google Hacking: This technique involves using Google search operators to find DNS records related to the target domain. This can be done using the Google search engine.
DNS enumeration can reveal valuable information about the target system, such as IP addresses, hostnames, and mail servers. This information can be used to map out the target network and identify potential vulnerabilities. However, it is important to note that DNS enumeration can also be used for malicious purposes, so it should only be done with proper authorization and in a responsible manner.
Dnsenum is a popular open-source tool used for DNS enumeration. It is a command-line tool that can be used to gather information about DNS records associated with a particular domain or hostname. The tool uses a variety of techniques, including zone transfers, brute-force, and reverse DNS lookups to enumerate DNS records.
Here are some of the features of Dnsenum:
- Zone transfers: Dnsenum can perform a DNS zone transfer to gather all the DNS records associated with the target domain. This is done by requesting a copy of the DNS zone file from the target DNS server.
- Brute-force: Dnsenum can perform a brute-force DNS enumeration to guess subdomains or hostnames associated with the target domain. It can use a wordlist or dictionary to generate possible domain names.
- Reverse DNS lookup: Dnsenum can perform a reverse DNS lookup to find the hostname associated with a particular IP address.
- Output formats: Dnsenum can output the results of the DNS enumeration in different formats, including plain text, CSV, XML, and HTML.
Dnsenum is a powerful tool that can be used for DNS reconnaissance and information gathering. However, it should be used responsibly and only with proper authorization. It is also important to note that some DNS servers may be configured to block zone transfers, so this technique may not always be effective.
Enumeration With Default Settings
When you run the following command with options, it automatically takes the default values i.e. -threads 5 -s 15 -w
Command: dnsenum -enum <example.com>

Enumeration of Sub-domain using Brute force (Custom File)
You can create a custom wordlist or dictionary file by adding domain names or keywords related to the target domain. For example, if the target domain is facebook.com, you can create a wordlist that includes keywords like “dev”, “prod”, “up”, “ctscan” and so on.
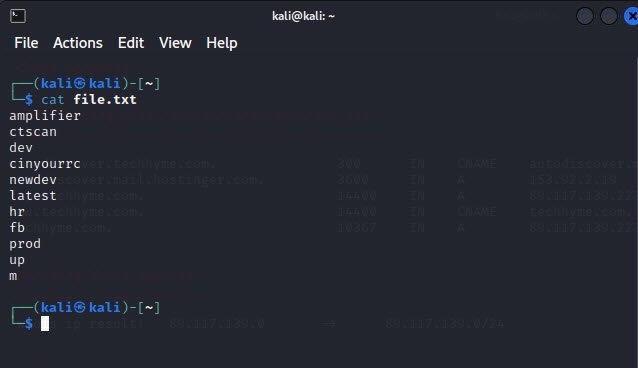
When you run the below command, it performs brute force search on subdomains along with the custom file passed (file.txt) as an attribute.
Command: dnsenum -f <file.txt> -r <example.com>
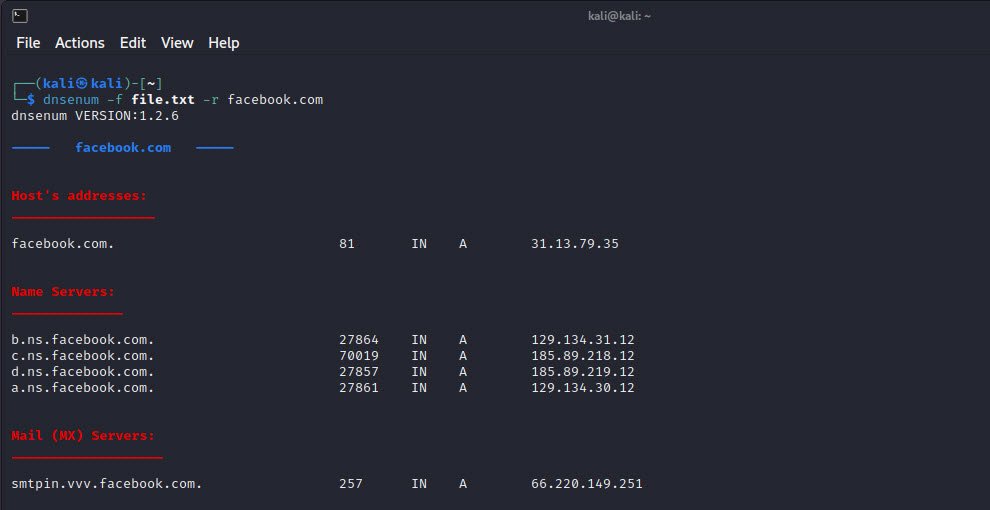
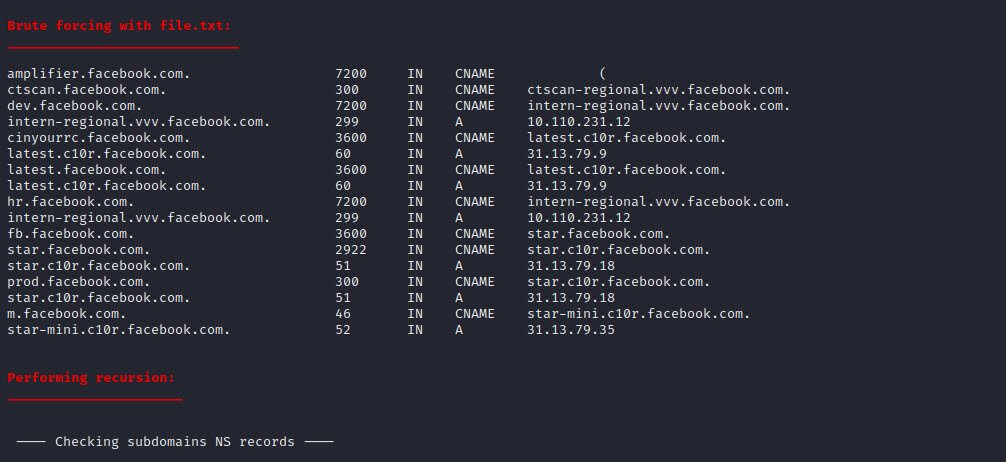
Once the tool has finished running, you can analyze the results. The output section (Brute forcing with file.txt) will contain a list of subdomains that were discovered during the enumeration process.
You may also like:
- How To Install Python 2.7.18 From The Source
- How To Parse SSH Authentication Logs with Logstash
- How To Easily Crack Wi-Fi Password
- 6 Most Useful Windows Command Prompt Commands
- Ripgrep – Searching for Specific File Types and Beyond
- Insert and Create Data in Elasticsearch
- Manage Time and Date in Linux with timedatectl
- How to Set Network Adapter Priority on Windows 11
- How to Add a User to Sudoers on Ubuntu
- 25 Popular Linux IP Command Examples








