
In January 2021, Microsoft pushed a security updated regarding the fixation of “Windows Print Spooler Spoofing Vulnerability” originally known as CVE-2021-1678
The vulnerable component is bound to the network stack and the set of possible attackers extends beyond the other options listed, up to and including the entire Internet. Such a vulnerability is often termed ‘remotely exploitable’ and can be thought of as an attack being exploitable at the protocol level one or more network hops away.
Furthermore, successful exploitation of this vulnerability requires a user to take some action before the vulnerability can be exploited.
There is total loss of confidentiality, integrity and availability resulting the attacker can gain full access of the system.
When the security update was released, it did not automatically protect devices from the vulnerability. However, it did add a new Registry key that admins could use to increase the RPC authentication level used for network printing to mitigate the vulnerability.
In other words, this update did not fix any vulnerability unless a Windows administrator created the following Registry key: “RpcAuthnLevelPrivacyEnabled”=dword:00000001
However, later this month’s September 14th Patch Tuesday security updates, Microsoft automatically enabled this setting by default for every Windows device even if that Registry setting was not created.
Once this was enabled by default, Windows users began experiencing some 0x0000011b errors when printing to network printers. This error is mainly seen in small business and home networks that can’t take advantage of a Kerberos setup on a Windows domain.
You can easily fix this 0x0000011b error by uninstalling the security updates but it will be again vulnerable to PrintNightmare and MSHTML vulnerabilities.
The quick turnaround of this solution is to disable the CVE-2021-1678 mitigation by editing the settings of Registry Editor.
To do that, open the Windows Registry Editor (by typing “regedit” in run command) and navigate to the HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Print,
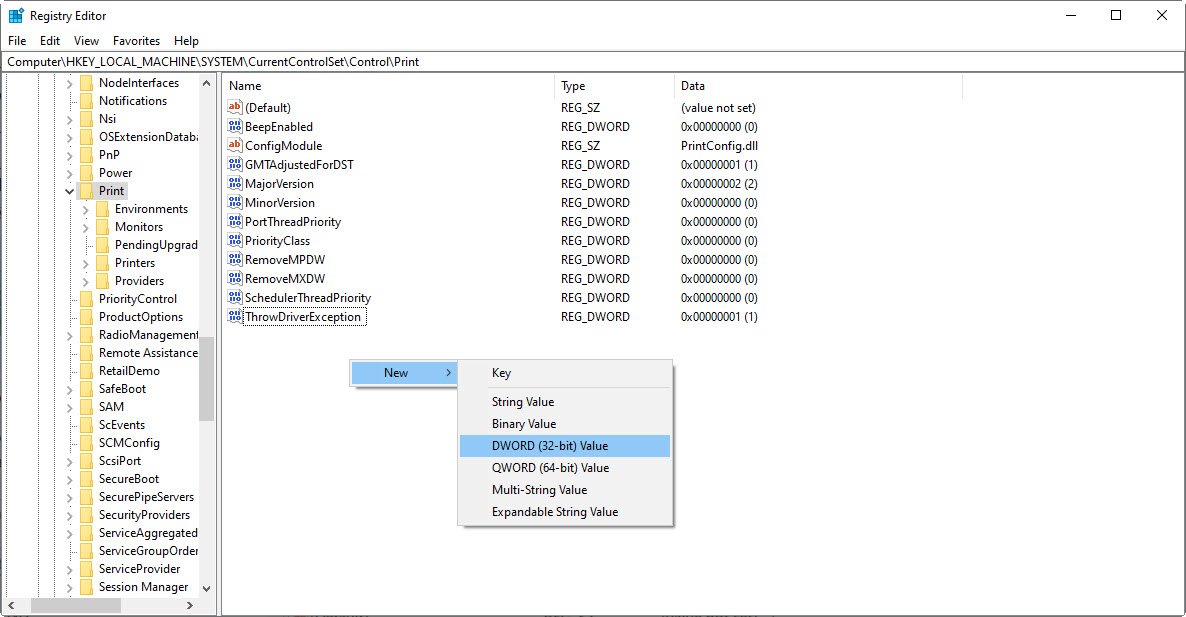
Create a new DWORD-32 bit value named RpcAuthnLevelPrivacyEnabled, and set it to 0, as shown below:
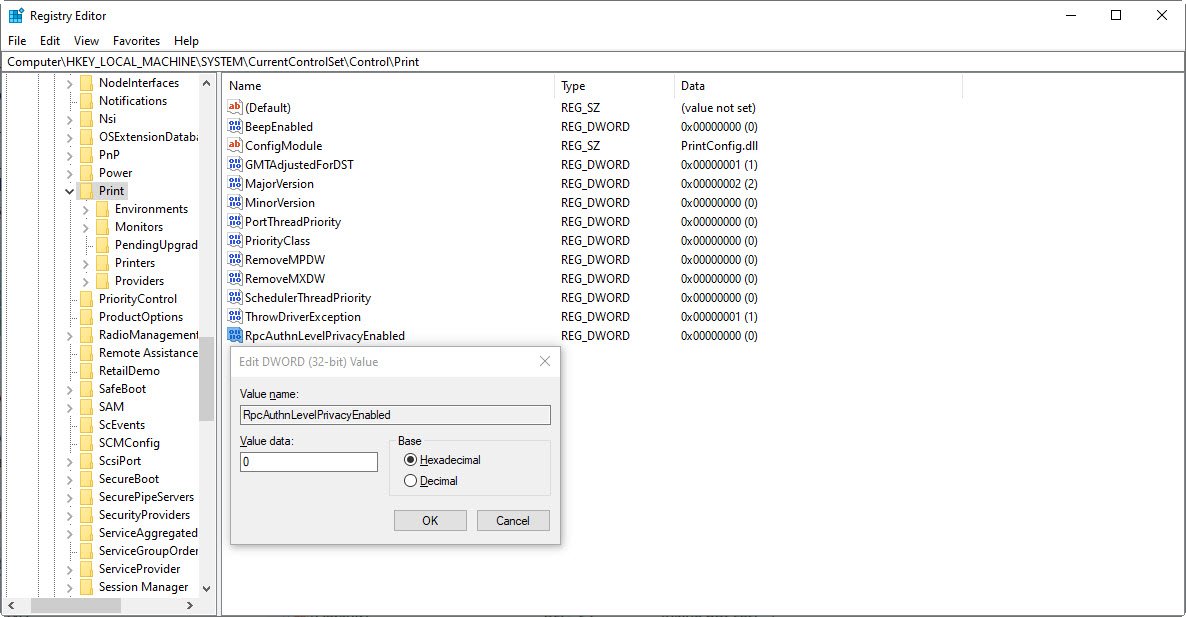
Once you disable this mitigation, you will no longer be protected from the vulnerability, but it will hopefully allow you to print again.
Alternatively, for better fast turnaround, you can use the fix-0x0000011b.reg file.
You may also like:- How To Install Python 2.7.18 From The Source
- How To Parse SSH Authentication Logs with Logstash
- How To Easily Crack Wi-Fi Password
- 6 Most Useful Windows Command Prompt Commands
- Ripgrep – Searching for Specific File Types and Beyond
- Insert and Create Data in Elasticsearch
- Manage Time and Date in Linux with timedatectl
- How to Set Network Adapter Priority on Windows 11
- How to Add a User to Sudoers on Ubuntu
- 25 Popular Linux IP Command Examples








