
SSH (Secure Shell) is a network protocol used for secure remote access to a computer system. It is a cryptographic network protocol that provides a secure channel between two networked devices, allowing secure communication over an unsecured network such as the internet. SSH was designed as a replacement for Telnet and other insecure remote shell protocols.
The SSH protocol uses encryption to protect data sent over the network, preventing eavesdropping and other forms of network-based attacks. The SSH protocol also provides strong authentication mechanisms to ensure that only authorized users can access the system.
There are two major versions of SSH protocol in use: SSH-1 and SSH-2. SSH-1 was developed in the mid-1990s and had several security issues, including weak encryption and poor key management. SSH-2, developed in the late 1990s, addressed these issues and is now the standard version of SSH.
SSH works by establishing a secure, encrypted connection between two devices. When a user attempts to log in to a remote system using SSH, the client sends a request to the server. The server responds by generating a random session key and encrypting it with the client’s public key. The client then decrypts the session key using its private key and sends an acknowledgment to the server. The session key is then used to encrypt all subsequent communications between the client and server.
SSH enumeration is the process of gathering information about a target system that has the SSH (Secure Shell) service enabled. The goal of SSH enumeration is to identify potential vulnerabilities or weaknesses that can be exploited to gain unauthorized access to the system.
SSH enumeration typically begins with identifying the target system’s IP address or domain name. Once the target has been identified, the attacker can use various tools and techniques to enumerate information about the SSH service running on the target system.
One common technique used in SSH enumeration is banner grabbing. This involves connecting to the SSH service on the target system and retrieving the SSH banner message. The SSH banner message often contains information about the SSH service version, which can be used to identify potential vulnerabilities or weaknesses in the SSH implementation.
You can also identify the open ports with the help of Nmap tool.
Command: nmap -sV -sC <Target IP>

Furthermore, you can also use “Searchsploit” module which is available in Kali Linux Operating System for exploit.
Command: searchsploit openssh

For Enumeration with Metasploit Framework, you can run the framework by using the below command:
Command: msfconsole
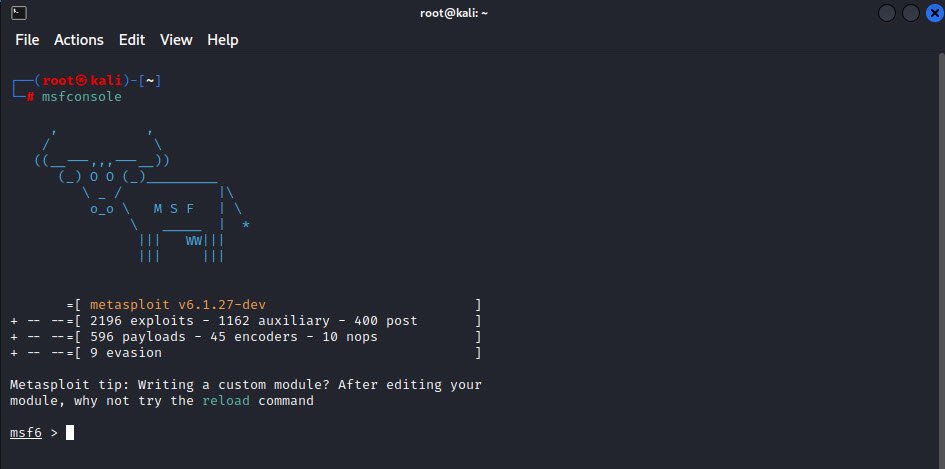
You can search different auxiliary and exploit modules by using the “search” command. After identifying, you can use the “use” operator to run those modules against the target.
Command: search ssh_enumusers
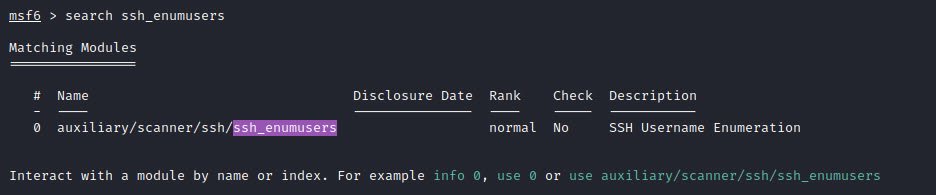
Other modules related to ssh are also available in msfconsole.
Command: search ssh_login

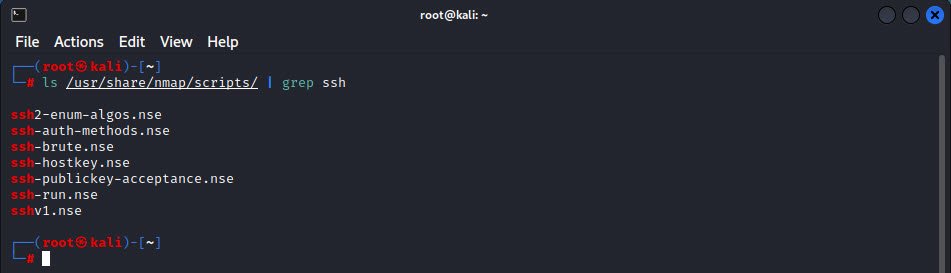
Nmap also provides many NSE scripts which are readily available to enumerate ssh.
Command: ls /usr/share/nmap/scripts/ | grep ssh
You may also like:
- How To Install Python 2.7.18 From The Source
- How To Parse SSH Authentication Logs with Logstash
- How To Easily Crack Wi-Fi Password
- 6 Most Useful Windows Command Prompt Commands
- Ripgrep – Searching for Specific File Types and Beyond
- Insert and Create Data in Elasticsearch
- Manage Time and Date in Linux with timedatectl
- How to Set Network Adapter Priority on Windows 11
- How to Add a User to Sudoers on Ubuntu
- 25 Popular Linux IP Command Examples








