
In the realm of ethical hacking and penetration testing, the post-exploitation phase is a critical juncture where an attacker seeks to establish and maintain control over a compromised system. It’s during this phase that hackers often need to gather valuable system information to assess their level of access and plan their next moves.
Kali Linux, a popular penetration testing distribution, offers a variety of system information commands that can be immensely valuable in this context.
In this article, we’ll explore some of these essential commands to help you navigate the post-exploitation phase effectively.
- Checking Uptime
- Monitoring Logged-In Users
- Identifying User Information
- Exploring User Details
- Checking Kernel Information
- Examining CPU Information
- Gathering Memory Information
- Analyzing Disk Usage
- Monitoring Memory and Swap Usage
- Reviewing Command History
- Detecting GPU Model
1. Checking Uptime
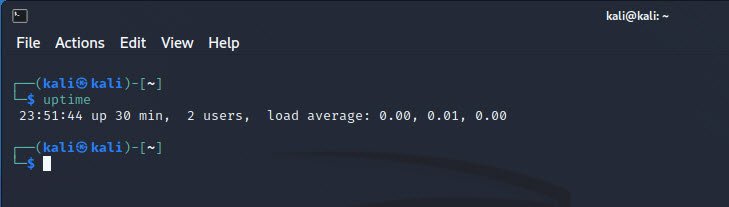
The `uptime` command allows you to view the current host’s uptime. This information can be crucial in understanding how long the system has been running since the last reboot. To execute it, simply type `uptime` in your terminal.
2. Monitoring Logged-In Users
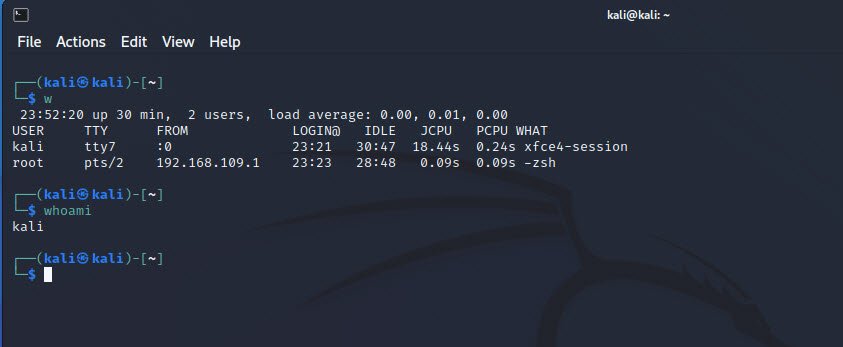
Knowing who is currently logged into the system is vital for an attacker. You can use the `w` or `whoami` command to achieve this. `w` provides a more detailed view, displaying information about all logged-in users, while `whoami` tells you the username of the currently logged-in user.
3. Identifying User Information
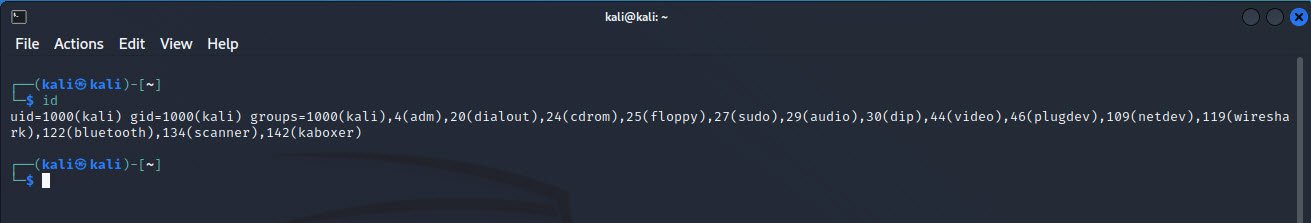
The `id` command reveals information about the user executing it. It displays user and group IDs, aiding in verifying whether you’ve successfully escalated privileges during the exploitation. Execute it by simply typing `id` in the terminal.
4. Exploring User Details
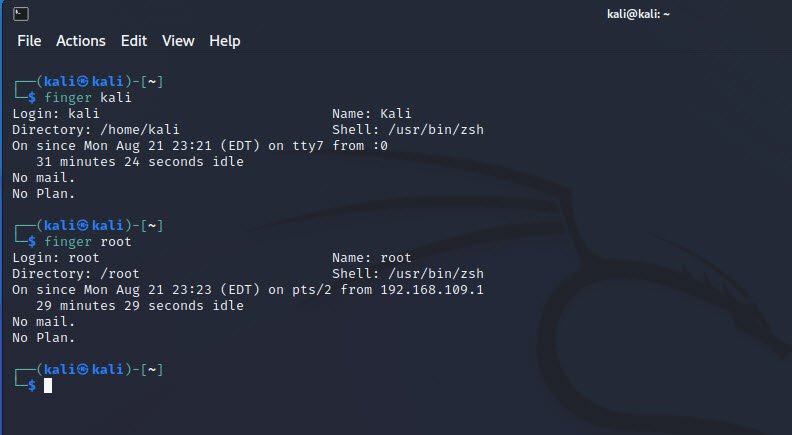
If you want to delve deeper into a specific user’s details, use the `finger` command followed by the target user’s name, e.g., `finger username`. This command can provide a wealth of information about the user, including their home directory, login shell, and more.
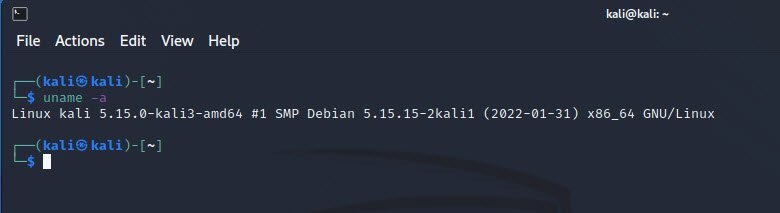
5. Checking Kernel Information
To obtain information about the system’s kernel, such as its version and build details, use the `uname -a` command. This can be beneficial in assessing potential vulnerabilities based on kernel versions.
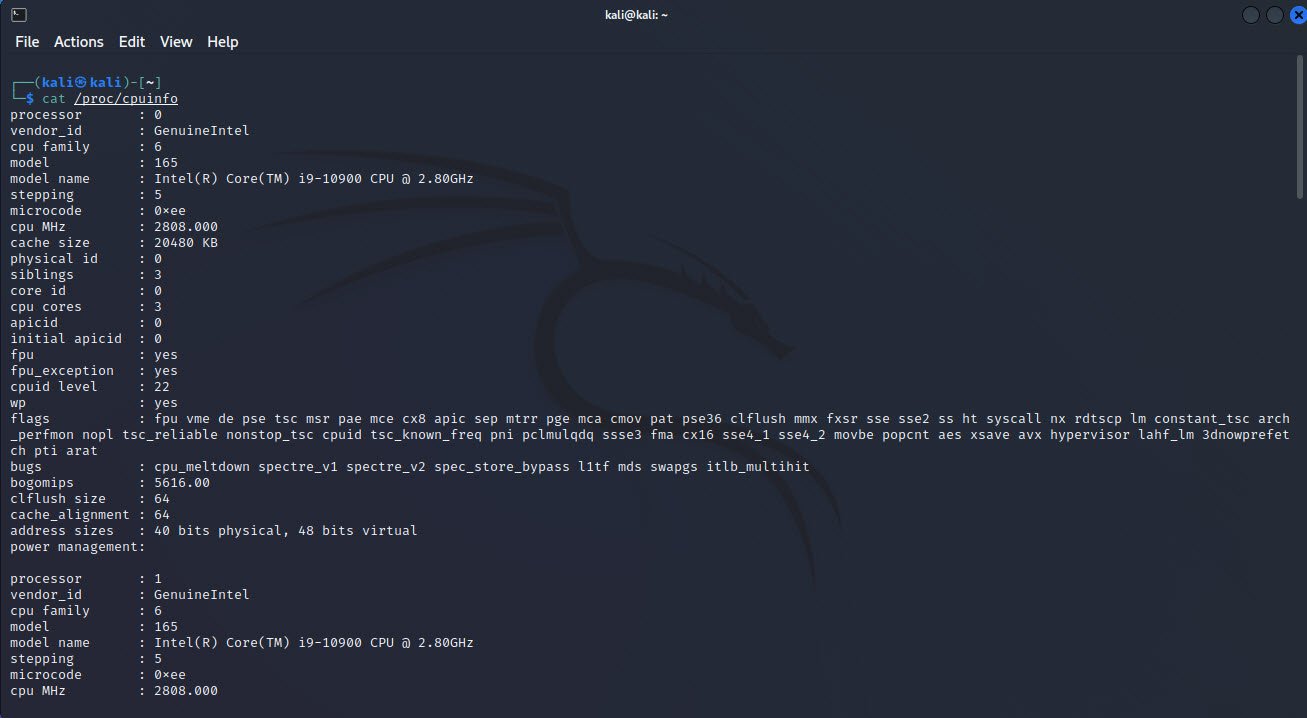
6. Examining CPU Information
Understanding the system’s CPU can help you plan resource-intensive tasks effectively. The `cat /proc/cpuinfo` command provides comprehensive details about the CPU, including its model, architecture, and capabilities.
7. Gathering Memory Information
To assess the system’s memory usage and configuration, use `cat /proc/meminfo`. This command provides data about total and available memory, as well as other memory-related statistics.
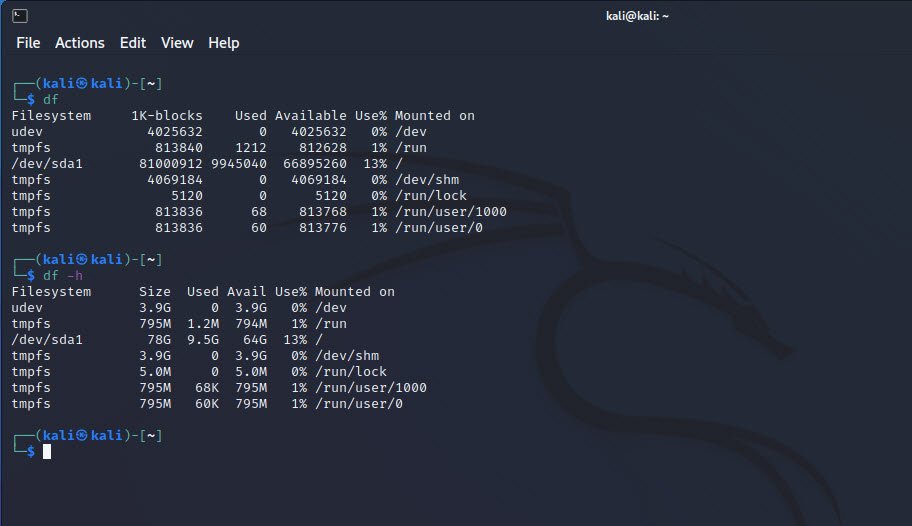
8. Analyzing Disk Usage
The `df` command is invaluable for checking disk space usage on the system. It displays information about mounted filesystems, including their sizes, used space, and available space.
9. Monitoring Memory and Swap Usage
To get a snapshot of both memory and swap space usage, use the `free` command. It provides detailed statistics on physical and virtual memory.

10. Reviewing Command History
In some situations, reviewing the command history can be helpful. The `history` command displays a list of all previously executed commands, revealing what actions have been performed on the system.

11. Detecting GPU Model
For systems equipped with a Graphics Processing Unit (GPU), determining the GPU model can be essential. You can use `lspci | grep VGA` to extract GPU-related information from the system.
These system information commands in Kali Linux are not only invaluable for ethical hackers and penetration testers but also for system administrators and security professionals. They empower users to understand the target system’s configuration, making it easier to identify vulnerabilities and make informed decisions during the post-exploitation phase.
Remember always to use this knowledge responsibly and within the boundaries of the law and ethical guidelines.
You may also like:- How To Install Python 2.7.18 From The Source
- How To Parse SSH Authentication Logs with Logstash
- How To Easily Crack Wi-Fi Password
- 6 Most Useful Windows Command Prompt Commands
- Ripgrep – Searching for Specific File Types and Beyond
- Insert and Create Data in Elasticsearch
- Manage Time and Date in Linux with timedatectl
- How to Set Network Adapter Priority on Windows 11
- How to Add a User to Sudoers on Ubuntu
- 25 Popular Linux IP Command Examples








