
The CCNA Cyber Ops SECOPS (Implementing Cisco Cybersecurity Operations) certification is a valuable credential for individuals looking to pursue a career in cybersecurity operations.
This certification validates the knowledge and skills required to detect and respond to cybersecurity incidents, ensuring the security of information systems within an organization. Preparing for the CCNA Cyber Ops SECOPS exam involves understanding various cybersecurity concepts, tools, and techniques.
One effective way to gauge your readiness for the exam is by practicing with sample test questions.
In this article, we’ll provide a set of practice questions along with detailed answers to help you assess your knowledge and identify areas for improvement.
1. Which function in the Linux shell allows for collection of regex groups?
- pcregrep
- ls
- grep
- man grep
2. Under which framework are auditable backups mandated?
- SOX
- HIPAA
- PCI DSS
- FOI
3.Why is DNS an important service for cybersecurity operators to monitor?
- It is commonly used by threat actors.
- It is commonly used in many legitimate applications.
- It is commonly used by threat actors because it is also used in common legitimate applications.
- It can be used to identify a targeted system.
4. An administrator suspects that a vulnerability exists on one of the host computers. It is communicating with the command and control host using HTTP messages. The hosts are all running Windows and Mozilla Firefox. Which user-agent string might be suspicious?
- Mozilla/5.0 (Windows NT 5.1; rv:7.0.1) Gecko/20100101 Firefox/7.0.1
- Mozilla/5.0 (Windows NT 10.0; WOW64; rv:50.0) Gecko/20100101 Firefox/50.0
- Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:25.0) Gecko/20100101 Firefox/29.0
- Mozilla/5.0 (X11; x86_64; rv:21.0) Gecko/20100101 Firefox/21.0
5. Which of the following is a description of deterministic analysis?
- Analysis based on potential vulnerabilities
- Analysis based on likely causes
- Analysis based on log files only
- Analysis resulting in conclusive results
6. Which of the following is true about tcpdump compared with Wireshark?
- tcpdump uses relative timestamps, where as Wireshark’s packet list pane uses UTC time.
- tcpdump uses UTC time, where Wireshark’s packet list pane uses relative timestamps.
- Wireshark’s packet details pane displays only layers 3-7, where as tcpdump can show all details in Hex and ASCII using the (-X) option.
- Wireshark is able to open PCAP files made in tcpdump, where tcpdump is not able to open PCAP files made in Wireshark.
7. Which of the following correlation rules should be investigated first?
- A rule with priority 3 in a policy with priority 2
- A rule with default priority in a policy with priority 5
- A rule with priority 1 in a policy with priority 4
- A rule with priority 2 in a policy with priority 1
8. Which of the following correctly lists the four elements under the VERIS schema?
- Actors, Actions, Assets, Attributes
- Action, Blame, Countermeasures, Device
- Threat, Target, Technique, Tactics
- Preparation, Detection, Containment, Post-Incident
9. Which of the following is the most likely reason that a threat actor might try to capture corporate email addresses using the reconnaissance phase of the Cyber Kill Chain?
- To determine the format for emails within the organization in order to generate whale phishing targets from the publicly accessible directors list
- To make contact with potential insider threats
- To reveal the email hosting provider used by the corporation
- To determine the location of a SMTP or POP server
10. Which of the following is a general principle for a standard data format?
- As generic as possible
- As tailored to local settings as possible
- As readable as possible
- As few formatting marks as possible
11. Which method of allocating virtual memory allocates full pages to applications, which is faster but sometimes results in higher memory usage?
- HeapAlloc
- LocalAlloc
- CoTaskMemAlloc
- Virtual Alloc
12. Which of the following statements is true?
- At the network layer, the address is maintained from the sending computer to the destination computer
- At the transport layer, the address is changed at every device
- At the application layer, the address is the application’s physical ID
- At the physical layer, the address is the logical address of the next hop device
13. A vulnerability allows an attacker to insert fraudulent invoices into the list that is sent to a company’s finance department to be processed. Which score might this vulnerability be given?
- Privileges Required: High
- Availability: High
- Confidentiality: Low
- User Interaction: Required
14. Which of the following are impact metrics?
- Attack Vector | Availability | Privileges Required
- Attack Vector | Attack Complexity | Privileges Required
- Confidentiality | Integrity | Availability
- Attack Complexity | User Interaction | Scope
15. Which of the following might occur in the weaponization phase of the Cyber Kill Chain?
- Potential vulnerabilities are identified.
- Exploits are sent to users.
- Exploits are linked to observed vulnerabilities in the system.
- Privileges are escalated.
16. Which of the following pieces of data should be kept with a hard drive removed for evidential purposes? (Select all that apply):
- Name of the investigator
- Date of collection
- Tools used for hard drive removal
- Suspect Name
17. Which of the following statements on integrity of evidence during data normalization is untrue?
- Some data is removed during the normalization process.
- The format of data is changed during the normalization process.
- Only a copy of the original data should be changed during the normalization process.
- Changing the data does not affect integrity if the process is documented.
18. Which of the following is not one of the 18 identifiable features according to HIPAA?
- Last name and initial
- Cell phone number
- Year of birth
- Email address
19. Which of the following is an example of probabilistic analysis?
- An HTTP communication with a known command and control server is identified as a potential threat.
- Analysis of a suspicious piece of software in a sandbox shows the same behaviors as a piece of known malware.
- A flow involving a connection via the corporate VPN is labeled as safe.
- A flow involving a Tor exit node is identified as a potential threat.
20. Looking at the following screenshot, what is suspicious about the NetFlow records?
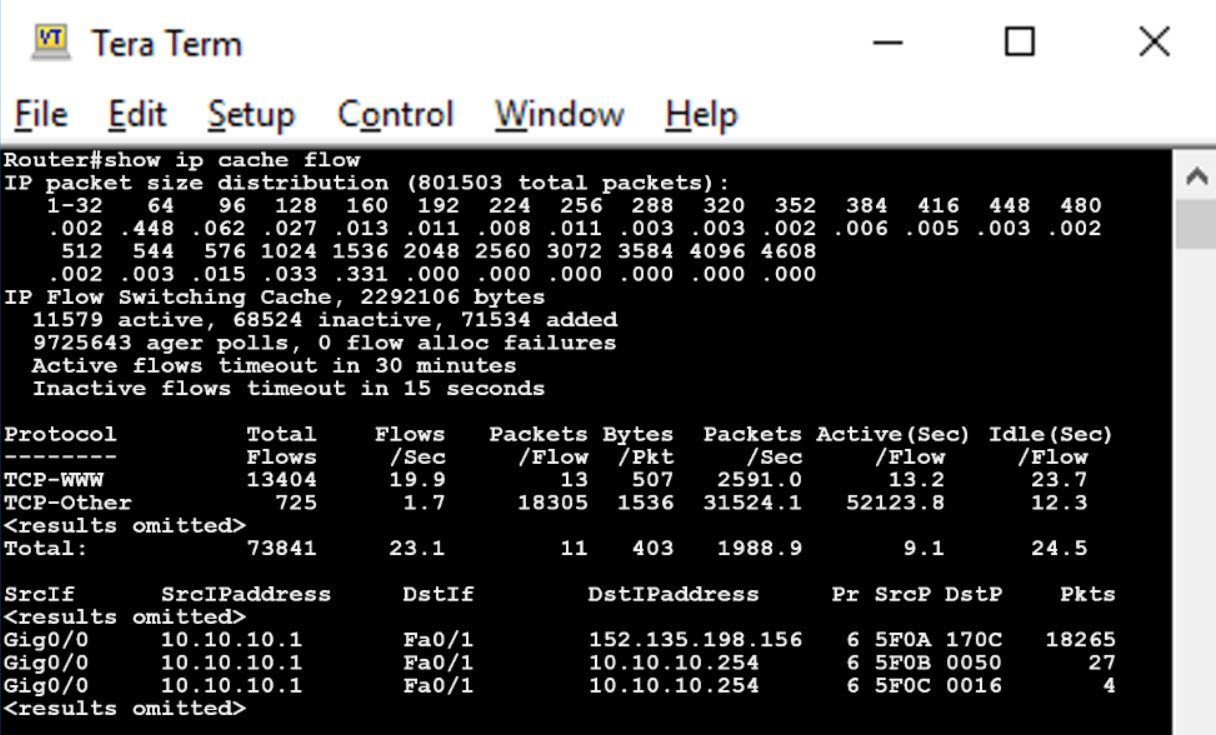
- An external is port scanning the internal server.
- An internal host is sending large amounts of data out of the network.
- An internal host has established a very long session with another internal host.
- Several similar external addresses have established sessions with internal hosts.
21. Which character on the Linux command line allows the results of one function to be passed to another?
- The pipe character (|)
- The greater than sign (>)
- The caret sign (^)
- The ampersand character (&)
22. Which attributes would be scored under VERIS if an encrypted USB pen drive was stolen?
- All attributes have to be given a score under VERIS.
- Confidentiality is affected as for all lost items.
- Availability is affected as the device is not available for use by the legitimate user.
- Confidentiality and Availability are both affected, so both should be scored.
23. Which of the following statements is true?
- The layer 2 address is assigned by the system administrator.
- The layer 3 address cannot be changed.
- The layer 3 address is hierarchical.
- The layer 2 address is assigned by the IANA.
24. Which of the following entities must comply with SOX?
- Any company that processes Visa Electron card payments
- A privately held corporation in America
- A Canadian charity with US branch offices
- A European company that has over 300 US shareholders
25. Which of the following is true about a telnet session?
- NetFlow would record two flows.
- Telnet would show flows to port 22.
- Telnet will encrypt the flow.
- Telnet does not require a password.
26. A user in finance follows a link sent to them from HACME bank, their company’s business banking supplier. The user accessed it through Mozilla Firefox on Windows 10. Which log is suspicious?
- GET HACME.com/login.php HTTP/1.1 in the proxy log
- Records to [hacme.com]:443 in NetFlow, where [hacme.com] is the correct IP address for the bank’s web server
- user-agent Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0 in the proxy log
- Records to [hacme.com]:80 in NetFlow, where [hacme.com] is the correct IP address for the bank’s web server
27. Which of the following VERIS entries would describe loss of data caused by a wildfire affecting a data center?
- Asset: P – Maintenance | Action: Physical: .Variety: Unknown
- Actor: External | Action: Physical: .Variety: Tampering
- Asset: U – Other | Action: Environmental
- Actor: External | Action: Environmental
28. Which is the best description of a logical copy of a disk?
- Best evidence
- A copy of every sector on a disk
- A copy of the files on a disk
- Unaltered disk image
29. A network administrator is investigating 10 user service desk tickets saying they are unable to connect to the wireless network. The network has not been compromised. Which of the following might be the cause of this?
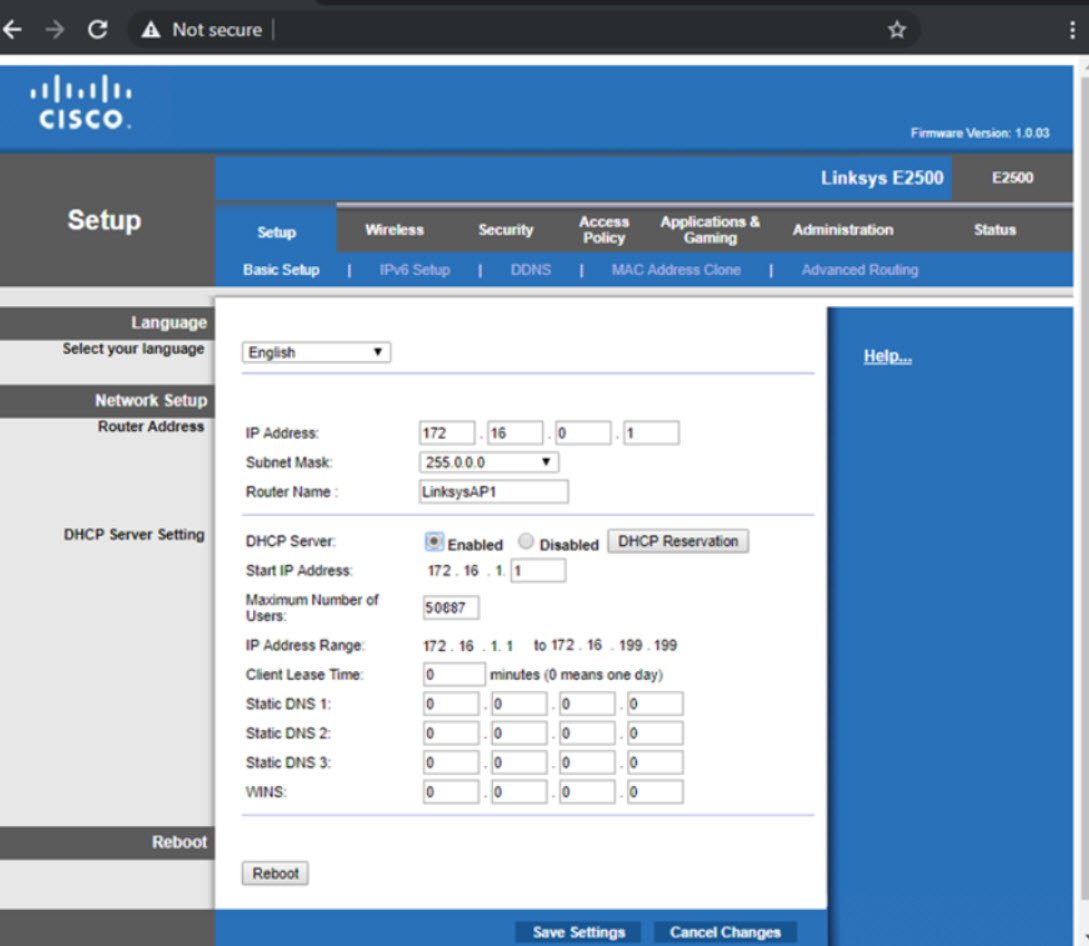
- DHCP pool depletion caused by too many users
- DHCP pool depletion caused by excessively long lease time
- MAC address filtering on the access point
- Disruption of the network between the Access Point and the DHCP server
30. Which of the following is a reason to attempt threat actor attribution?
- To deter future attacks
- To prevent poor publicity
- To help detect future attacks
- To allow the SOC to demonstrate its abilities
31. The following data is extracted from a data stream. Which application layer protocol is most likely?
Source: 10.10.10.10.52357
Destination: 10.10.10.128.443
- DNS
- SSL
- SSH
- DHCP
32. Which system components are not in the scope of PCI DSS security requirements?
- Technologies that store, process, or transmit cardholder data
- Applications that share data with applications in the CDE
- Systems in the same subnet or VLAN as the CDE
- Systems on the transmission path for cardholder data that are on public infrastructure (for example, the internet)
33. What feature of the IP 5-tuple makes it suitable for correlation of network events?
- The 5-tuple identifies the application layer protocols involved.
- The 5-tuple identifies the specific physical address of the source and destination.
- The 5-tuple is unchanged throughout the journey from host to host.
- The 5-tuple includes details of the route taken from start to finish.
34. Which organization draws data from a number of sources in order to provide insights into future actions or trends?
- Coordination centers
- Analysis centers
- Managed security service providers
- Distributed Internal CSIRTs
35. Which actions are carried out in the detection and analysis phase of an incident response?
- Profiling networks and servers to establish new baselines for activity
- Updating IPS/IDS/Firewalls
- Placing infected hosts in quarantine
- Verification of suspected incident
36. Which of the following is not a reason to use retrospective analysis?
- Detecting polymorphic malware through behavioral analysis is slow.
- Long dwell times between breach and detection.
- Not all threats have existing signatures.
- To detect future threat.
37. Which of the 4 As relates to the impact of the incident on the affected organization?
- Assets
- Actors
- Attributes
- Actions
38. Which command could be issued in Command Prompt on a user device to determine who was logged into it?
- last | grep “logged in”
- query user
- w
- whoami
39. A legitimate file enters the system, but the IDS incorrectly flags it as malicious. What does the administrator have to do?
- Nothing. The IDS has taken no action, so the file reached its intended target.
- Find, contain, and remove the malicious file. The IDS was correct, but has taken no preventative action.
- Advise the intended user, and remove the file from quarantine.
- Run a virus scan.
40. Where would you find a log of non-critical system messages?
- ~/log
- /var/log/messages
- /etc/log/info
- /bin/info
41. In which phase of the Cyber Kill Chain might an exploited device signal the attacker using a bespoke HTTP message?
- Exploration
- Communication
- Actions on objectives
- Command and control
42. What is the defining characteristic of an attack that has completed the installation phase in the Cyber Kill Chain?
- An attacker has hands-on-keyboard access.
- An attacker has persistent access.
- An attacker has achieved their objective.
- An attacker has executed the exploit.
43. Which of the following regex statements could be used to match the terms beginning in SS (for example, SSH and SSL) but not SSD?
- (SSH | SSL)
- [SSHL^D]
- SS[^D]
- SS(H|L)
44. Which of these questions might be asked to test the planning for containment, eradication, and recovery within the organization?
- What precursors of the incident, if any, might the organization detect
- What could be done to prevent similar incidents
- To which people would the team report the incident
- Which sources of evidence, if any, should be acquired
45. In which phase of the Cyber Kill Chain might an attacker attempt to take services offline?
- Reconnaissance
- Exploitation
- Actions on objectives
- Command and control
46. What is the most significant benefit of using a SIEM over the systems individually?
- Cybersecurity operators need only review a single log
- Understanding of the context of each entry
- Alerts all come from a single source
- Automated normalization
47. How does NetFlow use the IP 5-tuple?
- As a primary key
- To determine whether a new connection is being established
- To identify the appropriate flow
- To apply the ACL
48. What Cisco technology can be used to reveal layer-7 information?
- CDP
- LLDP
- NetFlow
- NBAR
49. Which of the following questions does not relate to the lesson-based hardening phase in incident handling?
- How could communication with the public be improved?
- How should employees be trained differently?
- What changes need to be made to the security audit and compliance policies?
- Have all the customer effects from the incident been reset?
50. How does NTP help log collation?
- By maintaining a unified time across all the devices in the network
- By maintaining a unified time format across all the devices in the network
- By providing time with a greater precision than would otherwise be available
- By coordinating when each service submits its logs to the collator
- Attack Vector | Availability | Privileges Required
- Attack Vector | Attack Complexity | Privileges Required
- Confidentiality | Integrity | Availability
- Attack Complexity | User Interaction | Scope
52. Which transport layer protocol is the most likely to be used for the destination: 192.168.1.254:snmp?
- DNS
- TCP
- HTTP
- UDP
53. Which of the following will be matched by the regex statement, [PacktPub]{8}?
- packtpub
- Packt Pub
- PACKTPUB
- backtack
54. What element of a network profile describes how much data is successfully transmitted over the network per second?
- Total throughput
- Session duration
- Critical asset utilization
- Running tasks
55. Which of the following is a reason to conduct probabilistic analysis?
- Innovative threats
- Inconsistent timestamps on logs
- Incomplete logs
- Integrity concerns on processed logs
56. How can an operator extract an application that’s been downloaded from a website using Wireshark?
- File | Export Objects | HTTP….
- File | Export Objects | UDP….
- File | Export Objects | Application/octet-stream.
- Applications can only be downloaded from a TCP stream.
57. Which of the following is true of trends in the analysis for cybersecurity?
- Increasing processing power means analysts are ahead of attackers.
- Increased information sharing means deterministic analysis is becoming accessible for smaller companies.
- Machine learning techniques are increasingly being used to support probabilistic analysis.
- Increasingly sophisticated attacks are pushing deterministic analysis into popularity.
58. A user in finance follows a link that’s sent to them from HACME bank, their company’s business banking supplier. The user accessed the website through Mozilla Firefox on Windows 10. Which log is suspicious?
- GET HACME.com/login.php HTTP/1.1 in the proxy log
- user-agent Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0 in the Proxy Log
- GET %D2%A2ACME.com/login.php HTTP/1.1 in the Proxy Log
- Records to [hacme.com]:443 in NetFlow, where [hacme.com] is the correct IP address for the bank’s web server
59. Which of the following teams may act as a response team of last resort, leading the response for organizations that may not have their own response team?
- Coordination centers
- Analysis centers
- Managed security service providers
- National CSIRT
60. A signature-based antivirus software is an example of what type of analysis?
- Deterministic analysis
- Probabilistic analysis
- Narrative analysis
- Predictive analysis
61. What is the purpose of ARP?
- To map IP addresses to MAC addresses
- To map IP addresses to port numbers on a switch
- To map sockets to port numbers on a switch
- To map sockets to MAC addresses
62. Which of the following might occur in the reconnaissance phase of the Cyber Kill Chain?
- Unsolicited emails are sent, telling users to click a link.
- Unsolicited telephone calls are made, telling users to allow a remote desktop connection.
- Unsolicited professional social media requests are made, asking for information about an upcoming job opportunity.
- Unsolicited merchandise, including USB pen drives.
63. Which of the following is not a category of a safeguard under HIPAA?
- Administrative safeguards
- Preemptive safeguards
- Technical safeguards
- Physical safeguards
64. Which of the following is a property of the NTFS filesystem?
- Maximum file size of 4 GB
- Maximum directory depth of 60 levels
- Support for encryption
- Full journaling (metadata and file data) support
65. Which of the following is a feature of sandbox detection?
- Sandbox detection allows the API calls to be recorded.
- Sandbox detection can negate some of the complexities associated with polymorphic malware.
- Sandbox detection is faster than signature-based detection.
- Sandbox detection uses file features extracted from the file itself to classify unknown files using machine learning.
66. Which of the following might occur in the exploitation phase of the Cyber Kill Chain?
- The attack code is launched.
- The attack code is downloaded to an infected host.
- The attack code is constructed based on the observed vulnerabilities.
- The infected host’s beacon back to the command and control server.
67. Who will coordinate the incident response activity if there is a single, distributed CSIRT in a large organization?
- Coordination center
- Organizational senior management
- IT support
- Information assurance
68. What can an organization use to manually configure alert priorities?
- Correlation rules in the Firepower Management Console
- Traps for syslog messages
- Severity scores in the IDS
- Metasploit
69. Who is ultimately responsible for reviewing and accounting for deficiencies under SOX?
- IT service managers
- Executive board members
- External auditors
- Internal verifiers
70. An email attachment enters the system and is characterized as malware. Which of the following is true?
- If the attachment was malicious, this is a true negative.
- If the attachment was legitimate, this is a true positive.
- If the attachment was legitimate, this is a false positive.
- If the attachment was malicious, this is a false negative.
71. The network’s security software went offline two days ago. An investigator suspects that malware has found its way onto a user’s computer in this time. Which of the following would be considered corroborative evidence?
- Antivirus scan logs that detected no threats
- Network data showing a spike in traffic from that computer over the last two days
- Activity logs showing that the computer has not been used in a week
- Multiple files on the computer being deleted over a number of months
72. Which of the following is a benefit of removing partial and transitive dependencies during normalization?
- Removing anomalies
- Reducing duplication
- Structuring metadata
- Collating information
73. An IPv6 packet has a length field value of 0. What might this mean?
- The packet header has been corrupted.
- The packet has no payload.
- The packet has a total length greater than 65,535 bytes.
- The packet is being used to establish a session.
74. Which of the following items is sensitive authentication data?
- Cardholder name
- Service code
- Magnetic-strip information
- Cardholder address
75. Which of the following is the highest priority item for collection according to NIST.SP800-86?
- Network connections
- Running processes
- Contents of memory
- Open files
76. Which option allows case sensitivity to be enforced with grep?
- -i
- -o
- grep is case-sensitive by default
- -C
77. Which of the following precautions reduce the threat to data during an investigation? (Select all that apply.)
- Antistatic wristbands used during physical handling
- Performing analysis on the original drive
- Storage in specialist storage facilities
- Encrypting the data
78. Which of the following statements about the following screenshot are true? (Select two.)
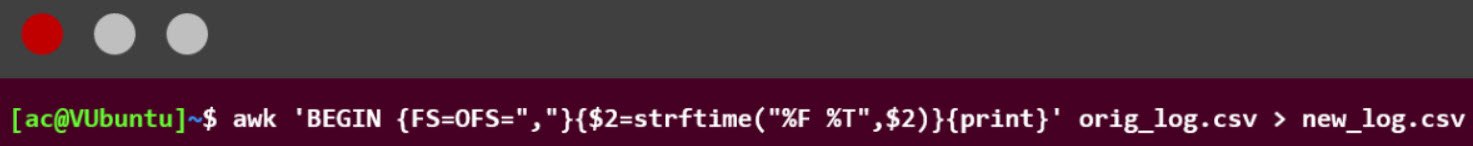
- Creating a new file creates duplication and, therefore, may create update anomalies.
- A new file should be created with the | command.
- Creating a new file with the > command maintains the integrity of the original.
- A new file should be created with the mv command.
79. Which of the following HTTP responses might indicate that the web server is currently experiencing a denial of service attack?
- HTTP/1.1 408 Gateway Timeout
- HTTP/1.1 503 Service Unavailable
- HTTP/1.1 301 Moved Permanently
- HTTP/1.1 400 Bad Request
80. A network administrator issues the following command. What are they trying to do?
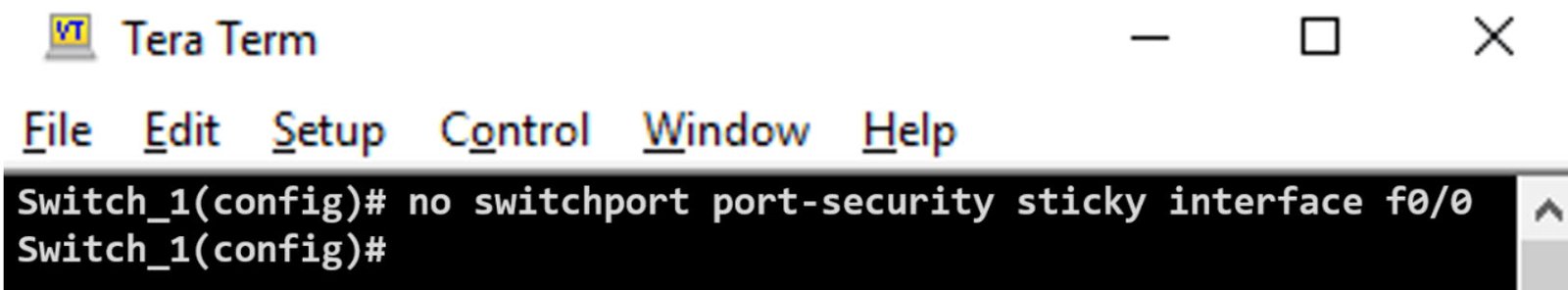
- Shut down this unused port
- Prevent an unauthorized host using this unused port
- Prevent an unauthorized host from unplugging the legitimate device and using the port in its place
- Reset the saved MAC addresses associated with the port
81. In which phase of the Cyber Kill Chain does lateral movement and privilege escalation occur?
- Exploitation
- Installation
- Command and control
- Actions on objectives
82. How can an investigator collect information about the network connections on a device running Windows?
- The CLI command, w
- The CLI command, netstat
- The CLI command, ifconfig
- The CLI command, ipconfig
83. The following screenshot shows part of a NetFlow output for an organization using PAT. What can be said about the position of the NetFlow collection device relative to the network?
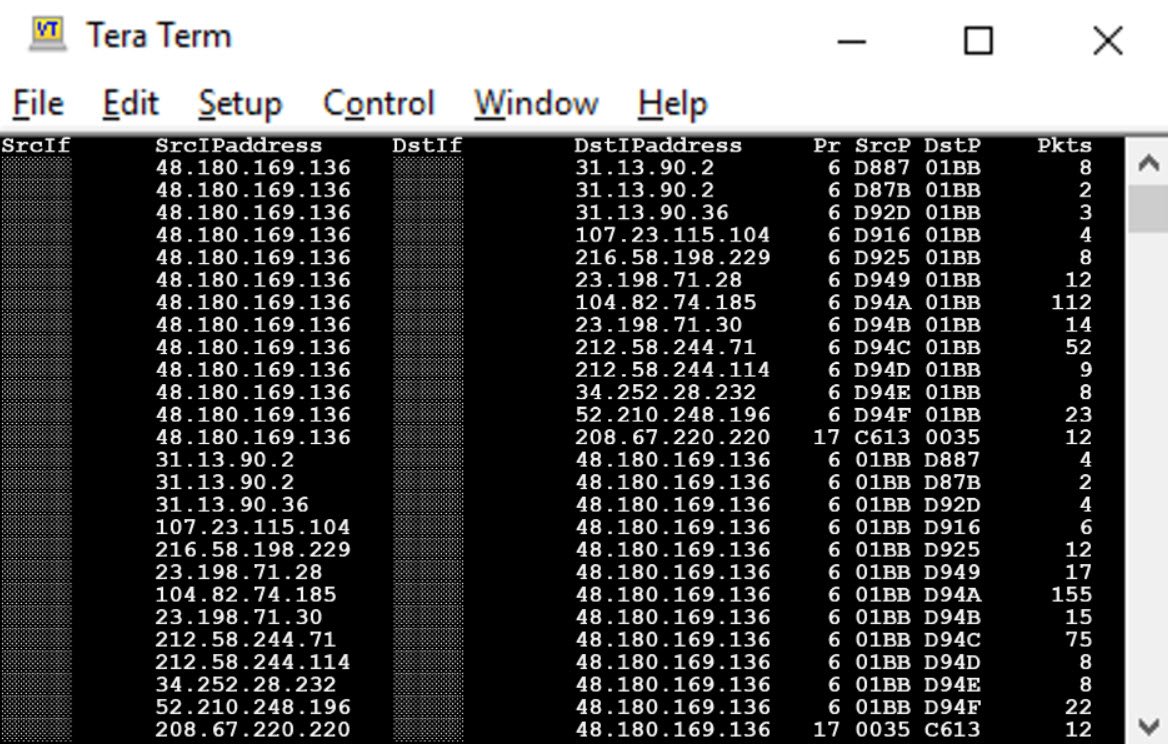
- The data is being collected before translation has been applied on the outbound interface and before translation has been applied on the inbound interface.
- The data is being collected before translation has been applied on the outbound interface and after translation has been applied on the inbound interface.
- The data is being collected after translation has been applied on the outbound interface and before translation has been applied on the inbound interface.
- The data is being collected after translation has been applied on the outbound interface and after translation has been applied on the inbound interface.
84. A system has 10 publicly routable addresses, a publicly accessible web server, and a /8 private (internal) addressing scheme. Which of the following should be considered?
- Applying a dynamic NAT to utilize the full publicly routable address pool
- Applying a PAT to allow more hosts to connect to the Internet simultaneously
- Applying a static NAT from one of the public addresses to the web server, pooling the other addresses for other users
- Using a static IP address allocation to apply control over every host’s IP address
85. What would be listed under Actor in a VERIS report concerning a “script kiddie” who found some code on a “dark web” site and was seeing what it would do?
- Actor: External: .Motive: Fun/.Variety: Unaffiliated
- Actor: External: .Motive: NA/.Variety: Unaffiliated
- Actor: External: .Motive: Unknown/.Variety: Unaffiliated
- Actor: External: .Motive: Grudge/.Variety: Force Majeure (chance)
86. Which of the following is a reason to establish asset attribution?
- To prove that the item is in its original form
- To assert copyrights
- To prevent theft
- To allow the item to be shared
87. At what point should the public affairs and media relations team be notified?
- As soon as an incident has been verified.
- As directed by senior management.
- When the incident has been identified.
- The Public Affairs and Media Relations team will contact the CSIRT if a comment is required.
88. In which phase of the Cyber Kill Chain might an attacker exfiltrate data from the system?
- Reconnaissance
- Actions on Objectives
- Exploitation
- Delivery
89. A vulnerability allows a remote attacker to pretend to be an employee and access internal documents. Which metric is likely to be affected the most?
- Confidentiality
- Privileges Required
- Scope
- Availability
90. For which phase of the Cyber Kill Chain is the use of honey pots an effective defensive tool?
- Actions on Objectives
- Delivery
- Command and Control
- Exploitation
91. An incident has arisen after a series of successful phishing emails were sent. Which would be the correct VERIS action?
- Social
- Misuse
- Error
- Malware
92. Which piece of the data is required at a minimum to qualify as CHD under PCI DSS?
- CVV2
- PAN
- Expiry date
- PIN
93. Which command allows the results of one function to be output to a file?
- The pipe character (|)
- The greater than sign (>)
- The caret sign (^)
- The ampersand character (&)
94. Which protocol allows an administrator to determine the IP addresses of routers between two hosts?
- ICMP
- IPv6
- IPv4
- TCP
95. Which of the following lines from Unix permissions indicates that a file can be executed by anyone within the same group as the owner?
- 0764
- -rw-rw-rw-
- 0710
- -rwxrw-r–
96. Which of the following is not a barrier to retrospective analysis?
- Historic log file truncation
- Incorrect/inconsistent date stamps
- Log file collation and normalization
- Rolling log files
97. Which of the following questions does not relate to the remediation phase in incident handling?
- What are the communication timelines for the resumption of services to customers?
- What is the effect of reverting to a previously backed up version of the data?
- Will compensation be required?
- How can customer relations be improved?
98. An administrator suspects that a vulnerability exists on one of the host computers. It is communicating with the Command and Control host using HTTP messages. The hosts are all running macOS and Safari. Why is the following user-agent string suspicious?
User-agent string: Mozilla/4.0 (compatible; MSIE 5.16; Mac_PowerPC)
- The user-agent string is too short.
- The user-agent string appears to be Mozilla, which is associated with Firefox.
- The user-agent string appears to be running Internet Explorer, which is not installed on the hosts.
- The user-agent string appears to support Mozilla/4.0 instead of Mozilla/6.0.
99. Which of the following entities would not be considered in the identification phase of incident handling under NIST.SP800-61 r2?
- Partner organizations
- Regulators
- Threat actors
- Customers
100. What command can be issued in the Terminal on macOS to display the list of tasks currently running on a device?
- Activity monitor
- tasklist
- ps -e
- last
Correct Answers –
- 1. pcregrep.
- 1. SOX.
- 3. It is commonly used by threat actors because it is also used in common legitimate applications.
- 4. Mozilla/5.0 (X11; x86_64; rv:21.0) Gecko/20100101 Firefox/21.0.
- 4. Analysis resulting in conclusive results.
- 2. tcpdump uses UTC time, where Wireshark’s packet list pane uses relative timestamps.
- 3. A rule with priority 1 in a policy with priority 4.
- 1. Actors, Actions, Assets, Attributes.
- 1. To determine the format for emails within the organization in order to generate whale phishing targets from the publicly accessible directors list.
- 1. As generic as possible.
- 4. Virtual Alloc.
- 1. At the network layer, the address is maintained from the sending computer to the destination computer.
- 4. User Interaction: Required.
- 3. Confidentiality | Integrity | Availability.
- 3. Exploits are linked to observed vulnerabilities in the system.
- 1. Name of the investigator, and 2. Date of collection.
- 4. Changing the data doesn’t affect integrity if the process is documented.
- 3. Year of Birth.
- 4. A flow involving a Tor exit node is identified as a potential threat.
- 2. An internal host is sending large amounts of data out of the network.
- 1. The pipe character (|).
- 4. Confidentiality and availability are both affected, so both should be scored.
- 3. The layer 3 address is hierarchical.
- 4. A European company that has over 300 US shareholders.
- 1. NetFlow would record 2 flows.
- 4. Records to [hacme.com]:80 in NetFlow, where [hacme.com] is the correct IP address for the bank’s web server.
- 4. Actor: External | Action: Environmental.
- 3. A copy of the files on a disk.
- 2. DHCP pool depletion caused by excessively long lease time.
- 1. To deter future attacks.
- 2. SSL.
- 4. Systems on the transmission path for card holder data which are on a public infrastructure (for example, the internet).
- 3. The 5-tuple is unchanged throughout the journey from host to host.
- 2. Analysis centers.
- 4. Verification of suspected incident.
- 4. To detect future threat.
- 3. Attributes.
- 2. query user.
- 1. Nothing. The IDS has taken no action, so the file reached its intended target.
- 2. /var/log/messages.
- 4. Command and Control.
- 2. An attacker has persistent access.
- 3. SS[^D].
- 4. Which sources of evidence, if any, should be acquired.
- 3. Actions on objectives.
- 2. Understanding of the context of each entry.
- 3. To identify the appropriate flow.
- 4. NBAR.
- 4. Have all the customer effects from the incident been reset?
- 1. By maintaining a unified time across all the devices in the network.
- 2. Attack Vector | Attack Complexity | Privileges Required.
- 4. UDP.
- 4. backtack.
- 1. Total throughput.
- 1. Innovative threats.
- 1. File | Export Objects | HTTP….
- 3. Machine learning techniques are increasingly being used to support probabilistic analysis.
- 3. GET %D2%A2ACME.com/login.php HTTP/1.1 in the Proxy Log.
- 4. National CSIRT.
- 1. Deterministic analysis.
- 1. To map IP addresses to MAC addresses.
- 3. Unsolicited professional social media requests are made, asking for information about an upcoming job opportunity.
- 2. Pre-emptive safeguards.
- 3. Support for encryption.
- 1. Sandbox Detection allows the API calls to be recorded.
- 1. The attack code is launched.
- 2. Organizational senior management.
- 1. Correlation rules in the Firepower management console.
- 2. Executive board members.
- 3. If the attachment was legitimate, this is a False Positive.
- 2. Network data showing a spike in traffic from that computer over the last two days.
- 2. Reducing duplication.
- 3. The packet has a total length greater than 65,535 bytes.
- 3. Magnetic-strip information.
- 1. Network connections.
- 3. grep is case-sensitive by default.
- 1. Anti-static wristbands used during physical handling and 3. Storage in specialist storage facilities.
- 1. Creating a new file creates duplication and therefore may create update anomalies and 3. Creating a new file with the “>” command maintains the integrity of the original.
- 2. HTTP/1.1 503 Service Unavailable.
- 4. Reset the saved MAC addresses associated with the port.
- 3. Command and Control.
- 2. The netstat CLI command.
- 3. The data is being collected after translation has been applied on the outbound interface and before translation has been applied on the inbound interface.
- 3. Applying static NAT of one of the public addresses to the web server, pooling the other addresses for other users.
- 1. Actor: External: .Motive: Fun/.Variety: Unaffiliated.
- 2. To assert copyrights.
- 2. As directed by senior management.
- 2. Actions on objectives.
- 1. Confidentiality.
- 1. Actions on objectives.
- 1. Social.
- 2. PAN.
- 2. The greater than sign (>).
- 1. ICMP.
- 3. 0710.
- 3. Log file collation and normalization.
- 4. How can customer relations be improved?
- 3. The user-agent string appears to be running Internet Explorer, which isn’t installed on the hosts.
- 3. Threat actors.
- 3. ps -e.
- 80 Most Important Network Fundamentals Questions With Answers
- 100 Most Important SOC Analyst Interview Questions
- Top 40 Cyber Security Questions and Answers
- Top 10 React JS Interview Theory Questions and Answers
- CISSP – Practice Test Questions – 2024 – Set 20 (53 Questions)
- Part 2: Exploring Deeper into CCNA – Wireless (145 Practice Test Questions)
- Part 1: Mastering CCNA – Wireless (145 Practice Test Questions)
- [1z0-1085-20] Oracle Cloud Infrastructure Foundations 2020 Associate MCQ Questions – Part 3
- [1z0-1085-20] Oracle Cloud Infrastructure Foundations 2020 Associate MCQ Questions – Part 2
- [1z0-1085-20] Oracle Cloud Infrastructure Foundations 2020 Associate MCQ Questions – Part 1









This Post Has One Comment