
Continuing our exploration of the MCSE (Microsoft Certified Systems Engineer) Windows 2000 Server exam, we now move on to part 2 of the sample questions. These questions cover additional areas of expertise required to successfully achieve the MCSE certification.
Also Read: MCSE Windows 2000 Server Exam Question with Answers – Part 1
Let’s dive into the questions and their explanations to further enhance your exam preparation.
Question 1 Which of the following TCP/IP properties can be added to the DHCP scope to be distributed to clients? (Choose all that apply.)
A. DNS Server
B. Router
C. Time Server Address
D. All of the above
Answer – D
Explanation – All the items can be added to the scope.
Question 2 The Corporate Policies and Procedures department has requested shared folders be included on all Windows 2000 servers to provide copies of the company’s procedures to all employees. Policies pertaining to certain departments may be contained in individual folders on other servers. The proposed solution must meet the following requirements:
- You must provide secure read-only access to the policies documents on the server.
- You must ensure up-to-date copies of the policies are available to all users at all times.
- You must ensure departmental policies are accessible from the Policies folder.
- Members of the Policies and Procedures department should have administrator access to the documents in the folders.
The proposed solution is to implement a Policies and Procedures folder on the NTFS volume of all servers. Members of the Policies and Procedures group are assigned Full Control NTFS permission to the folders; members of the Everyone group are assigned the Read permission. Configure a Dfs root for the primary Policies folder and create root replicas for folders on all other servers. Configure the Dfs replication policy to synchronize folders on all servers. Configure the share properties for the Policies folder to allow Full Control for the Policies and Procedures group and Read access for the Everyone group.
Which of the following does the proposed solution provide? (Choose all that apply.)
A. The proposed solution provides secure read-only access to the policies documents on the server.
B. The proposed solution ensures copies of the policies are available to all users at all times.
C. The proposed solution ensures departmental policies can be accessed from within the Policies folder.
D. The proposed solution gives members of the Policies and Procedures group administrator access to the documents in the folders.
Answer – A, B, and D
Explanation – Setting NTFS Full Control for the Policies and Procedures group gives them administrative control over the files in the folders; setting Read gives users the access they require. Utilizing Dfs to create replicas of the primary Policies folder ensure the most up-to-date files are copied to all servers automatically. However, there is no provision listed in the solution for access to folders outside the default folder; therefore, answer C is incorrect.
Question 3 Which of the following items is not a valid local policy?
A. Audit policy
B. User Policy
C. User Rights Assignment
D. Security Options
Answer – B
Explanation – User policy does not exist. The other policies are configured from the Local Security Settings MMC.
Question 4 How do you verify what software is currently loaded on your computer before you upgrade or install Windows 2000 Server?
A. In the System Tools
B. In the Start menu
C. In the Add/Remove Programs applet
D. In the Taskbar
Answer – C
Explanation – The Add/Remove Programs applet, which you can access from the Control Panel, displays a list of all the software you have installed on your computer.
Question 5 Melanie has informed you that her computer has begun to perform very slowly and that her hard disk light stays on for a very long time whenever she attempts to open one of the large database files that she is responsible for editing. What should you do to Melanie’s computer to correct the problem without installing any new hardware? (Choose all that apply.)
A. Defragment her hard drive.
B. Renew her DHCP lease.
C. Perform a disk cleanup on her hard disks.
D. Move her user account to a different OU.
Answer – A and C
Explanation – The most likely cause of Melanie’s problems is that her hard drive is getting full and has become fragmented. In this case, running Disk Cleanup followed by Disk Defragmenter may very well correct the problem for her. Renewing her DHCP lease has nothing to do with this problem; therefore, answer B is incorrect. Moving her user account to a different OU also has nothing to do with this problem; therefore, answer D is incorrect.
Question 6 What counters should be observed to diagnose a disk problem? (Choose all that apply.)
A. Disk Queue Length
B. Disk Bytes/transfer
C. Disk Seeks/Sec
D. % Disk Time
Answer – A and D
Explanation – If the Disk Queue Length is above 2, or the % Disk Time is a sustained 90% or better, the disk unit is too slow.
Question 7 Christopher is attempting to configure driver signing restrictions for the eight Windows 2000 Professional computers in his office running in a peer-to-peer network. After he configures the Block setting on all computers, he notices that other users can still install known unsigned drivers. What is the most likely cause of the problem?
A. Christopher did not configure the setting with an administrative account, and thus the settings are not applied to all computer users.
B. Christopher forget to save the newly configured settings, so they were not put into effect on the computer.
C. The other users must be members of the DNS Admins group, which has the permissions required to override any configured driver signing settings.
D. Christopher forgot to refresh Group Policy after applying the configuration. The changes should take effect after the computers have been restarted.
Answer – A
Explanation – Christopher most likely configured the settings with his user account, without being logged in as the Administrator. Only when logged on with administrative permissions can you set the current driver signing setting as the computer default. Forgetting to close out the dialog box is possible, but not the most likely cause; therefore, answer B is incorrect. In a peer–to-peer arrangement, there is no Active Directory, thus no DNS Admins group; therefore, answer C is incorrect. These settings have been applied to the local computer because there is no Active Directory domain, thus refreshing group policy is not an issue here; therefore, answer D is incorrect.
Question 8 You have recently created and configured a DHCP server for your network. Clients, however, report that they cannot obtain a DHCP lease from this new server. What is the most likely cause for this problem?
A. The DHCP server is not running Windows 2000.
B. You did not authorize the server in Active Directory.
C. The DHCP server is not running on a domain controller.
D. The DHCP server is running on a domain controller.
Answer – B
Explanation – Before a Windows 2000 DHCP server can begin servicing client requests, it must be authorized to do so in Active Directory. All other answers are incorrect.
Question 9 How do you verify what service pack is on your system before you upgrade or install Windows 2000 Server?
A. Look at the side of the Windows 2000 Server box.
B. Look in the Control Panel.
C. Look in the Start menu.
D. Look in the System window.
Answer – D
Explanation – The System window displays the version information for Windows 2000 Server, including the latest service pack installed. All other answers are incorrect.
Question 10 Which password would meet the complexity requirements of the password policy?
A. Ay324
B. 6!9280
C. XxYgoGq
D. Ay324!
Answer – D
Explanation – The requirements are that the password is at least six characters long, may not contain your username or parts of your full name, and must contain a character from three of the following four groups: A–Z, a–z, 0–9, and punctuation characters.
Question 11 Ron is an administrator of his company’s small Windows 2000 network. Ron’s duties include managing the backup servers and keeping all hardware devices up to date with the latest drivers. As he is browsing over the Cisco Web site, he comes across a new driver for the Cisco Aironet 350 WLAN adapter that his laptop computers use. He downloads the new driver file to a file server on the network. What does Ron need to do now to ensure that all of his portable computers get the updated driver installed?
A. He should manually copy the driver files into the systemroot \System32 folder on each portable computer. The portable computers will then automatically install the new driver files on the next restart.
B. He should create a new network connection using the same Cisco Aironet 350 adapter with the new driver. Windows 2000 will automatically clean up and remove the old outdated driver and network connection upon the next restart.
C. He should edit the properties of the network adapter from the Services console to ensure that it starts using the updated driver upon the next computer restart.
D. He should open the Device Manager, find the applicable device, and open the Properties page for it. On the Driver tab, he should use the Update Driver button to update the installed driver with the new driver.
Answer – D
Explanation – Ron needs to manually update the driver for the WLAN adapter using the Update Driver button on the Properties page of the device. Under no circumstances will the new driver automatically install itself; therefore, answer A is incorrect. Creating a duplicate instance of the same device will most likely lead to system instability or other issues. Windows 2000 will not perform any sort of automatic clean up either; therefore, answer B is incorrect. Manually configuring the service’s properties in the Service Manager will not cause the driver to become updated and will most likely result in the device not functioning properly; therefore, answer C is incorrect.
Question 12 Which of the following ports is automatically assigned to the Administration Web site when IIS is installed?
A. 80
B. 21
C. 443
D. None of the above
Answer – D
Explanation – The Administration Web site is assigned a random port number when it is installed, to limit the chance someone would attempt unauthorized access to the site to damage the server.
Question 13 When using Performance Logs and Alerts, what type of file should you log data to if you’re low on disk space?
A. Text File (CSV)
B. Text File (TSV)
C. Binary File
D. Binary Circular File
Answer – D
Explanation – The binary circular file will wrap around when it reaches its maximum limit, allowing you to keep recording data, but not using up all of the disk space. The two text file options are useful for importing performance data into a spreadsheet or graphing program; therefore, answers A and B are incorrect. The binary file will stop recording when the disk is full; therefore, answer C is incorrect.
Question 14 Why should you view the Hardware Compatibility List on the Microsoft Web site? (Choose all that apply.)
A. So you know whether your hardware is compatible with Windows 2000 Server.
B. Because you should become more familiar with the Microsoft Web site.
C. So you can download the latest drivers for your hardware devices.
D. So you know what hardware is available.
Answer – A and C
Explanation – You need to know whether your hardware is compatible with Windows 2000 Server before you install the operating system. The HCL also contains links to download drivers from the Windows or manufacturer’s Web site.
Question 15 Hannah is configuring a mirror set on her Windows 2000 Professional computer. She has two 80GB hard disks installed on her computer with the following simple volumes already created:
- C—45GB
- E—35GB
- F—45GB
- G—35GB
If Hannah creates a mirror set using volumes C and F, how much total storage capacity will she have on her computer?
A. 90GB
B. 160GB
C. 80GB
D. 115GB
Answer – D
Explanation – Hannah will have a total of 115GB of storage capacity available to her: 45GB in the mirror set, 35GB on volume E, and 35GB on volume G; therefore, answers A, B, and C are incorrect.
Question 16 Hannah wants to find out which 3Com network adapters are certified compatible with Windows 2000 before she buys any for her 25 new computers. What is the best way for her to get this information?
A. She should examine the Windows 2000 Readiness Analyzer.
B. She should visit the 3Com Web site to determine which network adapters are Windows 2000 certified.
C. She should look on the network adapter box and look for the Windows 2000 compatible logo.
D. She should visit the HCL and search for 3Com network adapters.
Answer – D
Explanation – Hannah should visit the Hardware Compatibility List (HCL) for the most up-to-date listing of hardware devices that are compatible with Windows 2000. Using the Windows 2000 Readiness Analyzer works well during the installation of Windows 2000 on a new computer, but will not help Hannah determine what hardware she should buy that is Windows 2000 compatible; therefore, answer A is incorrect. Visiting the 3Com Web site will not tell her for sure that any particular network adapter is certified for Windows 2000; therefore, answer B is incorrect. Looking at the box for a Windows 2000 logo is not a dependable way to ensure that the hardware is Windows 2000 compatible; therefore, answer C is incorrect.
Question 17 What counters should be observed to diagnose a network problem? (Choose all that apply.)
A. Bytes Total/Sec
B. Output Queue Length
C. Current Bandwidth
D. Datagrams/sec
Answer – A and B
Explanation – The Bytes Total/sec should never be above 75% of the network interface card rating and the Output Queue Length should not be above 2.
Question 18 Where do you examine the results of auditing that you have configured on your computer?
A. Performance Monitor
B. Active Directory Users and Computers console
C. Event Viewer
D. Local Security Policy console
Answer – C
Explanation – You can find audit entries located in the Event Viewer’s Security Log. All other answers are incorrect.
Question 19 Windows 2000 Terminal Services supports how many connections in Remote Administration mode?
A. One
B. Two
C. Three
D. Unlimited
Answer – B
Explanation – Windows 2000 Terminal Services supports two concurrent connections in Remote Administration mode. All other answers are incorrect.
Question 20 What counters should be observed to diagnose a processor problem? (Choose all that apply.)
A. % Processor Time
B. Processor Queue Length
C. % Processor Bandwidth
D. Processor Interrupts/Sec
Answer – A and B
Explanation – If the Processor Queue Length is above 2, or the % Processor Time is a sustained 80% or better, the processor is a bottleneck. All other answers are incorrect.
Question 21 In Windows 2000, which of the following types of disk configurations can you create on a Windows 2000 Server? (Choose all that apply.)
A. Mirrored volume
B. RAID-5 array
C. Spanned volume
D. Primary partition
Answer – A, B, C, and D
Explanation – On a Windows 2000 Server, you can create primary, extended, and logical partitions on a basic disk. You can also create mirrored, spanned, striped, and simple volumes on a dynamic disk as well as RAID-5 arrays. RAID-5 arrays are not available for use on Windows 2000 Professional computers, only on Windows 2000 Server computers.
Question 22 What choices do you have in regard to configuring licensing for a new Windows 2000 Server installation? (Choose all that apply.)
A. Per Seat
B. Per Server
C. Per Network
D. Per Processor
Answer – A and B
Explanation – You can choose from either Per Seat or Per Server licensing when installing a new Windows 2000 Server computer. All other answers are incorrect.
Question 23 You are establishing an intranet site for employee access to files and important company information. All client computers are running Windows 98 or Windows 2000 Professional with Internet Explorer version 5. The proposed solution must meet the following security requirements:
- You must use an authentication method that is supported by all clients.
- You must use an encrypted authentication method.
- You must ensure all requests are authenticated.
- You must choose an authentication protocol that is part of the HTTP specification.
The proposed solution is to configure the Web site to use only Digest authentication. Which of the following does the proposed solution provide? (Choose all that apply.)
A. The proposed solution uses an authentication method supported by all clients.
B. The proposed solution uses an encrypted authentication method.
C. The proposed solution ensures all requests are authenticated.
D. The proposed solution uses a protocol that is part of the HTTP specification.
Answer – A, B, C, and D
Explanation – Digest authentication is supported by Internet Explorer 5 and later, is an encrypted authentication method, and is part of the HTTP 1.1 standard. Because Allow anonymous access is not selected, all requests must be authenticated.
Question 24 Andrea is the network administrator for a small software development company. She is responsible for 7 Windows 2000 servers and 58 Windows 2000 Professional clients running in an Active Directory domain. Andrea wants to provide automatic protection for the client computers used by the sales and administration departments so that they cannot install unsigned digital drivers on them under any circumstances. Andrea does not want to prevent the installation of these types of drivers on the computers used by the developers, but does want them to be queried before any unsigned driver is installed. What should Andrea do to accomplish these goals? (Choose all that apply.)
A. Andrea should configure a Group Policy Object with the Block setting and link it to an OU that contains all of the computer accounts for the sales and administration departments.
B. Andrea should configure a Group Policy Object with the Block setting and link it to an OU that contains all of the user accounts for the sales and administration departments.
C. Andrea should configure a Group Policy Object with the Ignore setting and link it to an OU that contains all of the user accounts for the developers department.
D. Andrea should configure a Group Policy Object with the Warn setting and link it to an OU that contains all of the user accounts for the developers department.
Answer – B and D
Explanation – Remember that driver signing in Group Policy is tied to the User configuration settings, not the computer configuration settings. By configuring Block for the sales and administration groups and Warn for the developers group, Andrea will have met the requirements of the stated problem. Configuring driver signing is done in the user configuration of a GPO, not in the computer configuration area; therefore, answer A is incorrect. Creating a policy with the Ignore setting for the developers allows them to install unsigned drivers with no warning dialogue, which is against the stated objectives of the question; therefore, answer D is incorrect.
Question 25 In Windows 2000, you can have what minimum number and what maximum number of hard disks in a spanned volume?
A. Minimum of 1, maximum of 16
B. Minimum of 2, maximum of 32
C. Minimum of 2, maximum of 26
D. Minimum of 1, maximum of 26
Answer – B
Explanation – In Windows 2000, you can create spanned volumes with between 2 and 32 disks; therefore, answers A, C, and D are incorrect.
Question 26 Which of the following statements is true concerning EFS encryption and NTFS compression?
A. You can encrypt and compress a file simultaneously.
B. You cannot encrypt and compress a file simultaneously.
C. EFS encryption and NTFS compression require the FAT32 file system or better.
D. EFS encryption and NTFS compression require a digital certificate.
Answer – B
Explanation – EFS encryption and NTFS compression are mutually exclusive in Windows 2000. You can, however, use a third-party compression utility (such as WinZIP) to compress your files and folders that are EFS encrypted. EFS encryption and NTFS compression require that NTFS v5 be in use. All other answers are incorrect.
Question 27 Christopher is the administrator of a Windows 2000 network consisting of 125 Windows 2000 servers and 1,750 Windows 2000 Professional clients. His company is organized into four departments: Sales, Administration, Shipping and Receiving, and Engineering. The company manufactures and markets custom medical computer solutions to several hundred medical facilities. Christopher reimages approximately 25 clients per week due to users who have installed unsigned device drivers, causing the system to become unstable and even unresponsive at times. Christopher would like to find a way to avoid having to reimage his client computers. At the same, he needs to allow a small working group in the Engineering department to test drivers that they have created for the company’s solutions. What steps should Christopher perform to solve his problems without limiting the capability of the developers group? All computer and user accounts are in one of four OUs that correspond to the four departments in the company. (Choose all that apply.)
A. From Active Directory Users and Computers, Christopher should create a GPO and link it to the Sales, Administration, Shipping and Receiving, and Engineering OUs. Configure the driver signing policy in the GPO for Ignore.
B. From Active Directory Users and Computers, Christopher should create a GPO and link it to the Sales, Administration, Shipping and Receiving, and Engineering OUs. Configure the driver signing policy in the GPO for Block.
C. From Active Directory Users and Computers, create a new OU for the developers and move their user accounts to this new OU. Create a GPO and link it to the new developers OU and configure driver signing in the GPO to Warn.
D. From Active Directory Users and Computers, create a new OU for the developers and move their computer accounts to this new OU. Create a GPO and link it to the developers OU and configure driver signing in the GPO to Warn.
Answer – B and C
Explanation – Christopher has two basic needs here: prevent the reimaging of his client computers and not prevent the developers from being able to work with the driver files they are creating. Thus, his best course of action is two create two GPOs. Create and configure one GPO to Block unsigned driver installation and link it to the Sales, Administration, Shipping and Receiving, and Engineering OUs. The Developers OU, which contains the developers’ user accounts, should get a separate GPO that is configured with the Warn option, which still allows unsigned driver installation after acknowledgement of the fact the driver is unsigned. Configuring the Ignore option will allow the silent, successful installation of all driver files, signed or unsigned; therefore, answer A is incorrect. Driver signing is linked to the user configuration, not the computer configuration; therefore, answer D is incorrect.
Question 28 How can you install Windows 2000 Server if you cannot upgrade your current installation of Windows using the upgrade version? (Choose all that apply.)
A. You can throw the upgrade version away.
B. You can install the upgrade version to a different hard drive or partition.
C. You can set up a multiple-boot system and start the operating system you want when you boot the computer.
D. You can format the hard drive that contains the current operating system, and then install the upgrade version on that formatted drive.
Answer – B and C
Explanation – The upgrade version of Windows 2000 Server lets you install the upgrade version onto a different hard drive or partition, and this lets you boot to multiple operating systems on your computer. All other answers are incorrect.
Question 29 You have decided to disable the default IIS Web and FTP sites and create new sites from scratch. You will be configuring multiple Web and FTP sites on a single IIS server behind a Proxy server on the local network to be accessed by employees via the Internet.
The proposed solution must meet the following requirements:
- All sites must begin with the same configuration settings.
- Each site must be limited in the amount of network capacity it is allowed to utilize, while not limiting the overall bandwidth available to the IIS server.
- Sites must be secured to the highest possible level.
- By default, all Web sites must only be managed by members of the group IIS Admins.
The proposed solution is to access the Internet Information Services snap-in and select the server object, and then select Properties from the Action menu. On the server’s Properties page, select Enable Bandwidth Throttling, and then click Apply. Select the WWW Service in the Master Properties section, and then click Edit. Select the Operators tab, remove Administrators, and then add IIS Admins. Select the Directory Security tab, click Edit in the Authentication Control section, unselect Anonymous Access if selected, and then select only Digest authentication.
Which of the following does the proposed solution provide? (Choose all that apply.)
A. The proposed solution lets all sites begin with the same configuration settings.
B. The proposed solution limits the amount of bandwidth allowed for each site to be configured individually.
C. The proposed solution is secured to the highest possible level.
D. The proposed solution specifies that only members of the IIS Admins group are allowed to manage Web sites.
Answer – C and D
Explanation – Digest authentication is the highest possible level of authentication available for users across the Internet. Changing the default Operators for the WWW service ensures that all Web sites are managed only by members of the IIS Admins group. Because the Master Properties for the FTP service were not changed, all sites are not configured to begin with the same configuration, only Web sites; therefore, answer A is incorrect. The default bandwidth throttling option limits the bandwidth available to the IIS server, not for each site individually; therefore, answer B is incorrect.
Question 30 What tasks can be performed from the Task Manager? (Choose all that apply.)
A. Stop a running process.
B. Start a new process.
C. Switch the active window to a different application.
D. Set the priority on a process.
Answer – A, B, C, and D
Explanation – You can perform many tasks with the Task Manager, such as starting and stopping processes, switching windows, setting process priority, and viewing system resource usage and network usage.
Question 31 Chris reports to you that her CD-ROM is no longer functioning. You instruct her to open the Device Manager and inspect the status of the CD-ROM. When she opens Device Manager, she sees the image shown below. What is the most likely solution to the problem?
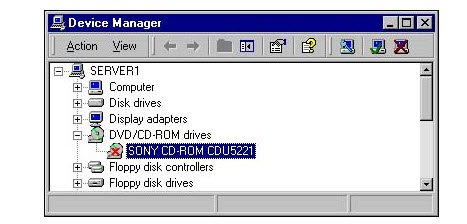
A. You should install new drivers for the CD-ROM.
B. You should manually enable the CD-ROM.
C. You should manually assign the resources for the CD-ROM.
D. You should allow Windows 2000 to resume automatic management of the CD-ROM resources.
Answer – B
Explanation – The CD-ROM is depicted with a red X over its icon—indicating that it has been manually disabled. Manually enabling the device will correct the problem. Installing new drivers for the CD-ROM will not correct the problem; therefore, answer A is incorrect. Manually assigning the resources for the CD-ROM will not correct the problem; therefore, answer C is incorrect. Allowing Windows 2000 to automatically manage the CD-ROM resources is not related to this issue and will not correct the problem; therefore, answer D is incorrect.
Question 32 Howard has implemented a RAID-5 array on one of his Windows 2000 servers that uses 11 80GB hard disks. What is the total amount of storage space that will be available to Howard in this implementation?
A. 720GB
B. 760GB
C. 800GB
D. 880GB
Answer – C
Explanation – RAID-5 arrays require all disks to have the same capacity. The parity information will require the capacity of one of the disks in the array; thus, if Howard uses 11 80GB disks to construct a RAID-5 array, he will have 800GB available for storage and 80GB used for the parity information; therefore, answers A, C, and D are incorrect.
Question 33 The WINS database can be configured to automatically backup every:
A. 3 hours
B. 12 hours
C. 6 hours
D. 24 hours
Answer – A
Explanation – The WINS server will perform a backup every three hours. All other answers are incorrect.
Question 34 What options are available when a threshold is reached in Performance Logs and Alerts? (Choose all that apply.)
A. Log an entry in the System Log.
B. Send a network message.
C. Start a performance log.
D. Run a program.
Answer – B, C, and D
Explanation – The Alerts program can log an event in the Application log, not the System log; therefore, answer A is incorrect.
Question 35 How can your network users obtain certificates?
A. Through a Web site set up when Windows 2000 Server sets up certificates
B. On a disk
C. On a network folder
D. As an attachment in an email message
Answer – A
Explanation – After you set up a Certification Authority and grant certificates, Windows sets up a Web site on the server so users can get those certificates. All other answers are incorrect.
Question 36 Andrea is configuring a mirror set on her Windows 2000 Professional computer using two 80GB hard disks. She has previously created a simple volume on each of the hard disks. How much storage capacity will she have after she has configured the mirror set?
A. 160GB
B. 80GB
C. 120GB
D. 140GB
Answer – B
Explanation – Mirror sets require two volumes of the same size, thus her total capacity will be 80GB after the mirror set has been created; therefore, answers A, C, and D are incorrect.
Question 37 What is the name of the flat file used for host name to IP address mapping?
A. LMHOSTS
B. HOSTS
C. LMHOST
D. HOST
Answer – B
Explanation – HOSTS is the file used for DNS mappings. LMHOSTS is the file that is used to preload NetBIOS name mappings; therefore, answer A is incorrect. Answers C and D are incorrect because they are invalid terms.
Question 38 Which of the following IIS 5.0 features allows recovery of interrupted file transfers?
A. Virtual Directories
B. Delegated Administration
C. FTP Restart
D. WebDAV
Answer – C
Explanation – FTP Restart allows interrupted file transfers to be recovered from the point of disconnect, rather than restarting the transfer from the beginning. The other IIS features do not control file transfer parameters; therefore, answers A, B, and D are incorrect.
Question 39 You are trying to finish a database query so that you can go home for the evening. Which priority should you set for the database process in Task Manager?
A. Priority 1
B. Priority 4
C. Priority 8
D. Priority 9
Answer – D
Explanation – Because the normal priority for a process is 8, only 9 would be an improvement. All other answers are incorrect.
Question 40 Which of the following password policies would prevent your computers from being susceptible to a dictionary attack?
A. Account Threshold
B. Account Lockout Counter
C. Account Lockout Threshold
D. Account Lockout
Answer – C
Explanation – The Account Lockout Threshold allows you to configure how many failed attempts will be accepted before the account is disabled. The other choices do not exist and are therefore incorrect.
Question 41 What size partition is the minimum recommended on a hard drive to install Windows 2000 Server?
A. 140MB
B. 2GB
C. 500MB
D. 1GB
Answer – D
Explanation – You need 1GB of space minimum to install Windows 2000 Server. All other answers are incorrect.
Question 42 Rosa has a new driver that she would like to install on her computer for her scanner. When she tries to install the driver, which she obtained from the manufacturer’s Web site, she is not allowed to install it. She must have the driver installed on her computer to use some important new features from her scanner. What can you do to get the driver installed?
A. Log on to Rosa’s computer using your administrative account and change the driver signing behavior to Warn. Install the driver and then change the driver signing behavior back to Block.
B. Change the driver signing behavior for the OU that Rosa’s computer account belongs to. Install the driver and the change the driver signing behavior back to Block.
C. Change the driver signing behavior for the OU that Rosa’s user account belongs to. Install the driver and the change the driver signing behavior back to Block.
D. Restart Rosa’s computer in Safe Mode and install the driver. Restart Rosa’s computer again to place it back into normal operation.
Answer – A
Explanation – The easiest way to allow the driver to be installed is for you to log on to Rosa’s computer, change the driver signing behavior, install the driver, and then return the driver signing behavior back to Block. Driver signing applies to a user configuration, not a computer configuring; therefore, answer B is incorrect. Changing the driver signing behavior of the entire OU is not a good choice because it will allow other users to install unsigned drivers; therefore, answer C is incorrect. Installing the driver in Safe Mode is also not a good choice; therefore, answer D is incorrect.
Question 43 You have applied disk quotas across all file servers in your network. You want to allow the graphic arts department to have a larger disk quota than all other departments. Additionally, you want to ensure that all departments except the graphic arts department are denied disk usage when the quota setting is exceed. What should you do?
A. You should change the disk quota settings for the graphic arts department by editing the GPO that is linked to the Graphic Arts OU.
B. You should change the disk quota settings for the graphic arts department from the Quota Entries window.
C. You should move all of the graphic arts users to a new file server.
D. You should move all of the other users to a new file server.
Answer – B
Explanation – Disk quota settings can be configured manually for a variety of reasons from the Quota Entries window. Disk quotas are not controlled from Group Policy; therefore, answer A is incorrect. Moving users from one file server to another will not solve this problem and will most likely cause new problems in the process; therefore, answers C and D are incorrect.
Question 44 Which of the following IP addresses are private addresses? (Choose all that apply.)
A. 172.32.0.5
B. 191.168.0.10
C. 10.10.254.5
D. 172.30.8.9
Answer – C and D
Explanation – The private addresses are 10.0.0.0–10.255.255.255, 172.16.0.0–172.31.255.255, and 192.168.0.0–192.168.255.255; therefore, answers A and B are incorrect.
Question 45 Dawn reports that her computer’s modem is not functioning properly. When you examine the Device Manager on Dawn’s computer, you see the display shown below. What is the most likely solution to this problem?
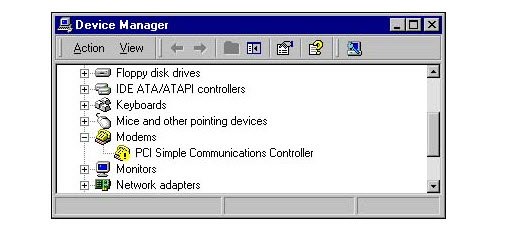
A. You should install new drivers for the modem.
B. You should manually enable the modem.
C. You should manually assign the resources for the modem.
D. You should allow Windows 2000 to resume automatic management of the modem resources.
Answer – A
Explanation – The modem is being shown with a yellow exclamation point over its icon. This indicates a device that is missing its driver. The device is not disabled, so manually enabling the modem is not the solution; therefore, answer B is incorrect. Manually assigning resources for the device is not possible because no drivers are installed; therefore, answer C is incorrect. Allowing Windows 2000 to take automatic control of the modem’s properties will not be possible until the Plug and Play drivers have been installed; therefore, answer D is incorrect.
Question 46 Which of the following accurately describes a situation where Dfs replication will be triggered immediately?
A. The administrator adds a file to the shared folder that acts as the Dfs root.
B. A user is denied access to files on a Dfs link.
C. The KCC identifies a change in topology that requires replication.
D. There are no circumstances in Dfs that will trigger immediate replication.
Answer – D
Explanation – Dfs replication runs on a specified schedule, which cannot be triggered automatically. All other answers are incorrect.
Question 47 In Windows 2000, you can have what minimum number and what maximum number of hard disks in a RAID-5 array?
A. Minimum of 2, maximum of 32
B. Minimum of 2, maximum of 16
C. Minimum of 3, maximum of 32
D. Minimum of 3, maximum of 16
Answer – C
Explanation – In Windows 2000, your RAID-5 arrays can have between 3 and 32 disks; therefore, answers A, B, and D are incorrect.
Question 48 Which users can decrypt an EFS encrypted file? (Choose all that apply.)
A. User with DRA rights
B. Enterprise Admins
C. User who encrypted the file
D. Domain Admins
Answer – A and C
Explanation – Only the user who encrypted the file and the user account with recovery agent rights are able to decrypt an encrypted file. All other answers are incorrect.
Question 49 Bill is responsible for the six Windows 2000 Professional clients in his company’s office. The company has no plans to install a Windows 2000 Server computer. To save himself extra work, Bill allows the computers to default to using APIPA. All of his computers receive an 169.254.x.x IP address. It all seems to work until they try to access the Internet. What is Bill’s problem?
A. Bill has some Windows 98 clients.
B. Bill forgot to add the gateway IP address to the APIPA configuration.
C. APIPA doesn’t distribute gateway IP addresses.
D. The APIPA service isn’t starting.
Answer – C
Explanation – APIPA only assigns private IP addresses in the 169.254.x.x range to clients—it does not distribute information, such as a default gateway, in the way that a DHCP server does. All other answers are incorrect.
Question 50 Bob is the only IT professional in his company. He works in a small department that has a Windows 98 workgroup. He has just received a new computer with nothing on the hard drives. He wants to install Windows 2000 Server to make it a file and print server, and he has the Windows 2000 Server CD-ROM. Due to miscommunication, the BIOS has been configured with a password, and he cannot set up the machine to boot from the CD-ROM. He needs to create a set of setup disks to begin the installation of Windows 2000. How can he accomplish this?
A. Bob needs to find another Windows 2000 Server on which to run the makebt32 program from his Windows 2000 CD.
B. Bob needs to find another Windows 2000 computer (Server or Professional) on which to run winnt32 from his Windows 2000 CD.
C. Bob can use any of his Windows 98 computers and run the makeboot program from his Windows 2000 CD.
D. Bob can use any of his Windows 98 computers and run the makebt32 program from his Windows 2000 CD.
Answer – D
Explanation – You can create setup disks from any machine running a Microsoft operating system if it has CD-ROM support and a floppy disk. As a result, Bob does not need to go to a Windows 2000 machine; he can use his Windows 98 machines by running the makebt32 program; therefore, answer A is incorrect. The winnt32 program is used to install Windows 2000, not to create setup disks; therefore, answer B is incorrect. Because Windows 98 is a 32-bit operating system, he cannot use the makeboot program; therefore, answer C is incorrect.
Question 51 How are host (A) records created in DNS for legacy (pre-Windows 2000) clients? (Choose all that apply.)
A. Broadcasts, similar to WINS
B. Manually by an administrator
C. Dynamically by the DHCP server
D. From a computer’s domain account
Answer – B and C
Explanation – Windows 2000 DNS host records are either manually created or added automatically from client registration via DHCP. All other answers are incorrect.
Question 52 What counters should be observed to diagnose a memory problem? (Choose all that apply.)
A. Pages Input/sec
B. Page Faults/Sec
C. Available Bytes
D. Cache Faults/Sec
Answer – A, B, and C
Explanation – They are all good indicators of the presence of a memory problem. Cache Faults is a processor measurement; therefore, answer D incorrect.
Question 53 What user account has the default recovery agent role on a standalone server?
A. Power Users Group
B. DRA User
C. Domain Administrator account
D. Local administrator
Answer – D
Explanation – By default, the local administrator account is granted the recovery agent role for standalone workstations and servers. All other answers are incorrect.
Question 54 You are working on improving the performance of a database query, and you decide to log the response time of your server that is performing the query. Which tool should you use?
A. System Monitor
B. Task Manager
C. Performance Logs and Alerts
D. Performance Monitor
Answer – C
Explanation – Although System Monitor and Task Manager allow you to monitor performance, they don’t have the logging functionality that Performance Logs and Alerts does; therefore, answers A and B are incorrect. Performance Monitor was used in previous versions of Windows; therefore, answer D is incorrect.
Question 55 Which of the following password policies would prevent your users from selecting a blank password? (Choose all that apply.)
A. Passwords Must Meet Complexity Requirements
B. Password Length
C. Minimum Password Length
D. Require Non-Blank Password
Answer – A and C
Explanation – The complexity requirements are fairly strict, and the minimum password length can be set to at least 1. The other choices do not exist and are therefore incorrect.
Question 56 What is a partition?
A. The blocks of data on a hard drive.
B. The logical division of space on a hard drive.
C. How you divide network data.
D. The division of speed in your Internet connection.
Answer – B
Explanation – A partition is the logical division of space on a hard drive you set when you format the hard drive. All other answers are incorrect.
Question 57 Austin has just installed a new video adapter in one of his servers. Now the video display is in 16-color 640×480 mode. What should Austin do to allow a higher screen resolution and color depth?
A. Austin should remove the video adapter and install a different type of video adapter; this one must be incompatible with Windows 2000.
B. Austin should update the video adapter driver from the Driver tab of the Properties page for the video adapter.
C. Austin should install the default Plug and Play monitor.
D. Austin should restart the computer in Safe Mode and remove the video adapter from the computer via the Device Manager.
Answer – B
Explanation – The most likely case here is that the drivers for the new video card did not install properly or did not provide the desired resolution and color depth. Installing the most recent driver files from the Driver tab will, in most cases, correct this problem. The video adapter is most likely compatible with Windows 2000, but just needs updated drivers; therefore, answer A is incorrect. Installing the default Plug and Play monitor will not correct the problem; therefore, answer C is incorrect. Restarting in Safe Mode and removing the video adapter is not required in this instance because the video adapter is working, just not providing full capability; therefore, answer D is incorrect.
Question 58 Milena is the administrator in your organization that is responsible for all Windows 2000 NNTP servers. All of Milena’s NNTP servers have two 120GB disks installed in a mirrored set. On Monday morning, Milena comes into work and discovers that the secondary disk in one of her NNTP servers has failed. The server is still running, but she needs to restore fault tolerance to it as soon as possible. Which of the following represent steps that Milena should perform to correct the problem as quickly as possible? Note that not all steps might be listed. (Choose all that apply.)
A. She must break the mirror on the server.
B. She must replace the failed disk.
C. She must perform a restoration of data from the most recent backup set.
D. She must create a Windows 2000 boot disk and ensure that the BOOT.INI file on it points to the secondary disk.
Answer – A and B
Explanation – Because the secondary mirror disk failed, Milena has it pretty easy. She must break the mirror set, replace the disk, and then re-create the mirror. No restoration of data should be required because the primary disk is still operating; therefore, answer C is incorrect. The creation of a special Windows 2000 boot disk is only required in this situation when the primary disk in the mirror set is the one that has failed; therefore, answer D is incorrect.
Question 59 Windows 2000 Terminal Services supports how many connections in Application Server mode? (Choose all that apply.)
A. 2
B. 50
C. Unlimited
D. 1000
Answer – C
Explanation – The only limitation is the number of licenses that you purchase and the horsepower of your server. All other answers are incorrect.
Question 60 Which of the following file systems support encryption?
A. FAT
B. FAT32
C. NTFS 4
D. NTFS 5
Answer – D
Explanation – Only NTFS 5, which is included with Windows 2000, supports file and folder encryption. All other answers are incorrect.
- 80 Most Important Network Fundamentals Questions With Answers
- 100 Most Important SOC Analyst Interview Questions
- Top 40 Cyber Security Questions and Answers
- Top 10 React JS Interview Theory Questions and Answers
- CISSP – Practice Test Questions – 2024 – Set 20 (53 Questions)
- Part 2: Exploring Deeper into CCNA – Wireless (145 Practice Test Questions)
- Part 1: Mastering CCNA – Wireless (145 Practice Test Questions)
- [1z0-1085-20] Oracle Cloud Infrastructure Foundations 2020 Associate MCQ Questions – Part 3
- [1z0-1085-20] Oracle Cloud Infrastructure Foundations 2020 Associate MCQ Questions – Part 2
- [1z0-1085-20] Oracle Cloud Infrastructure Foundations 2020 Associate MCQ Questions – Part 1








