OpenSSL is a powerful and versatile open-source tool that provides encryption, decryption, and secure communications. It is widely used in various security applications, including secure sockets layer (SSL) and transport layer security (TLS) protocols.
In this article, we’ll explore into several important OpenSSL commands and their applications.
Checking OpenSSL Version
The following commands provide information about your OpenSSL installation:
openssl versionThis simple command displays the OpenSSL version installed on your system.

To provides more detailed information about your OpenSSL installation, including the build date and platform, the command is:
openssl version -a
If you want to list out all the various OpenSSL commands and their descriptions, the command is:
openssl help
Establishing SSL/TLS Connections
You can use OpenSSL to establish secure connections with remote servers and retrieve information. Here are some commonly used commands:
openssl s_client -connect example.com:443This initiates a basic SSL/TLS client connection to a remote server (example.com) on port 443.
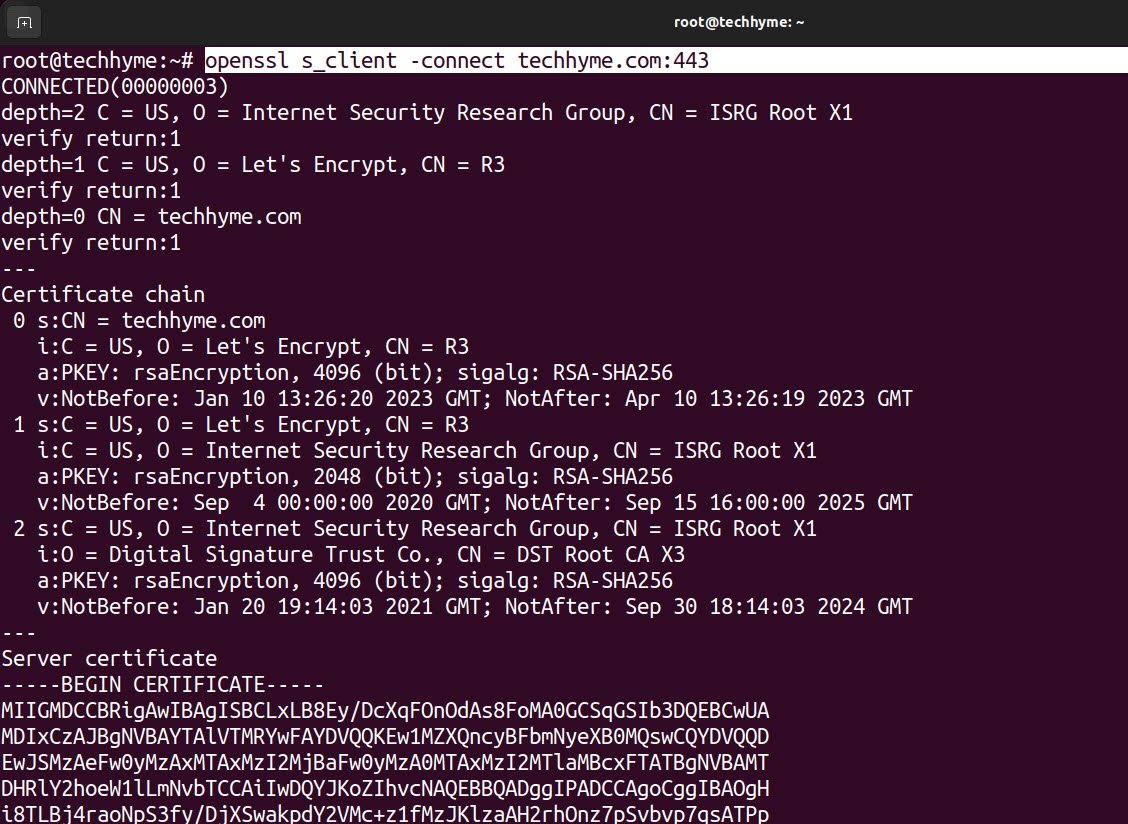
To send an HTTP request to a server, you can use the following commands after establishing the connection:
HEAD /HTTP/1.1
Host: example.com
To send a carriage return and line feed after each line of the request, which is often required for compatibility with certain servers, the command is:
openssl s_client -connect example.com:443 -crlf
To force the use of TLS version 1.2, which is a more secure protocol version, following is the command:
openssl s_client -connect example.com:443 -tls1_2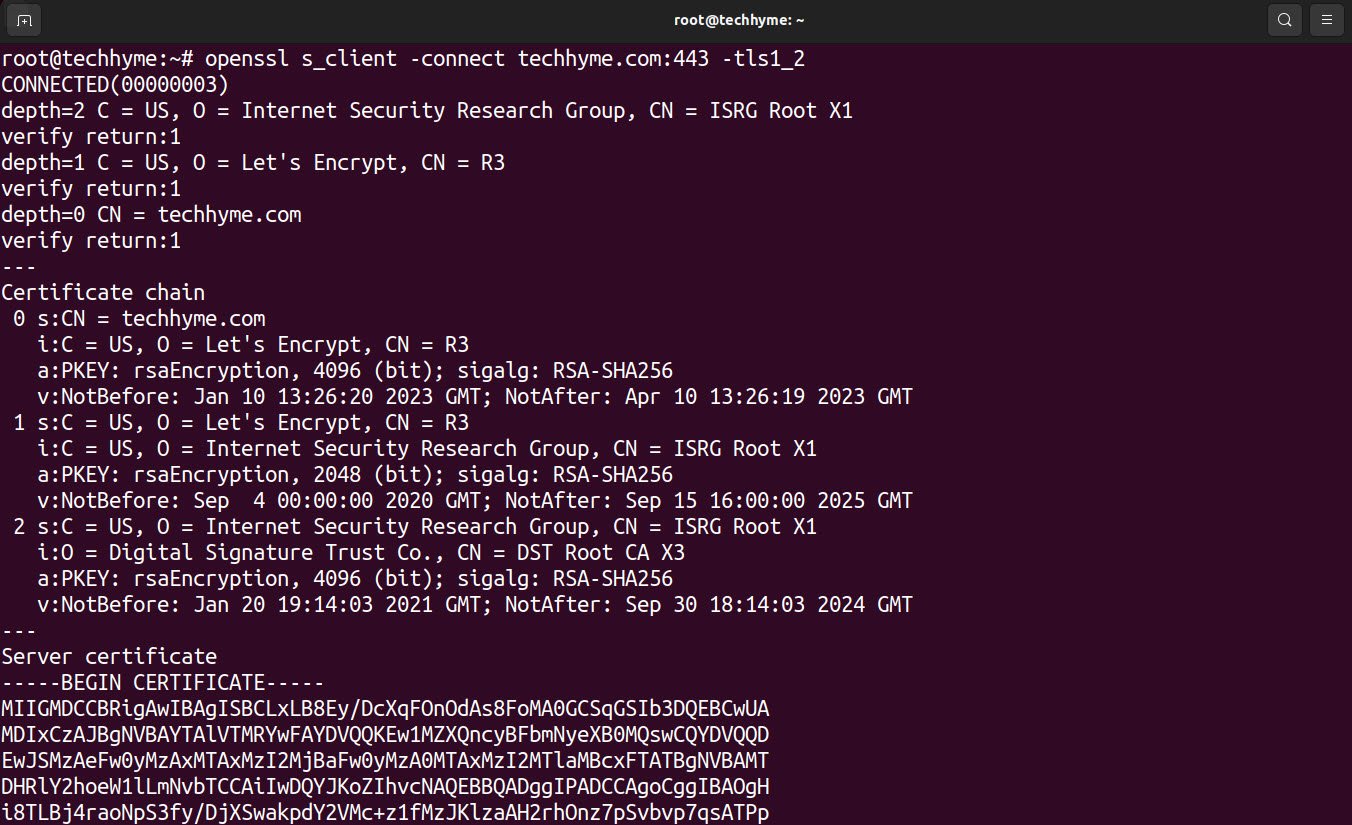
The `-brief` option displays less information during the SSL/TLS handshake process.
openssl s_client -connect example.com:443 -brief
Examining SSL/TLS Certificates
You can use OpenSSL to examine SSL/TLS certificates provided by remote servers. Here’s how you can do it:
To check the validity of the server’s SSL/TLS certificate, you can use the following command:
echo | openssl s_client -connect example.com:443 2>/dev/null | openssl -x509 -noout -datesThis command connects to the server and then extracts and displays the certificate’s validity dates.

To examine the Subject Alternative Name (SAN) extensions in the server’s certificate, you can use the following command:
echo | openssl s_client -connect example.com:443 2>/dev/null | openssl -x509 -noout -ext subjectAltNameThis command provides information about alternative names (such as domain names or IP addresses) associated with the certificate.

These commands are valuable for inspecting certificates and ensuring their authenticity when connecting to secure servers. They are especially useful when working with web servers, email servers, and other systems that rely on SSL/TLS encryption for secure communications.
OpenSSL commands are essential tools for securing data transmission and validating the authenticity of servers on the internet. Understanding these commands and their applications is crucial for anyone involved in managing secure connections and ensuring the privacy and integrity of data in today’s digital world.
You may also like:- How To Install Python 2.7.18 From The Source
- How To Parse SSH Authentication Logs with Logstash
- A Comprehensive Guide to File System Commands in Linux
- Essential File Compression Commands in Linux
- Secure Shell (SSH) Protocol – A Comprehensive Guide
- Monitoring Active Connections in Kali Linux Using Netstat
- How To Easily Crack Wi-Fi Password
- 6 Most Useful Windows Command Prompt Commands
- Ripgrep – Searching for Specific File Types and Beyond
- Insert and Create Data in Elasticsearch